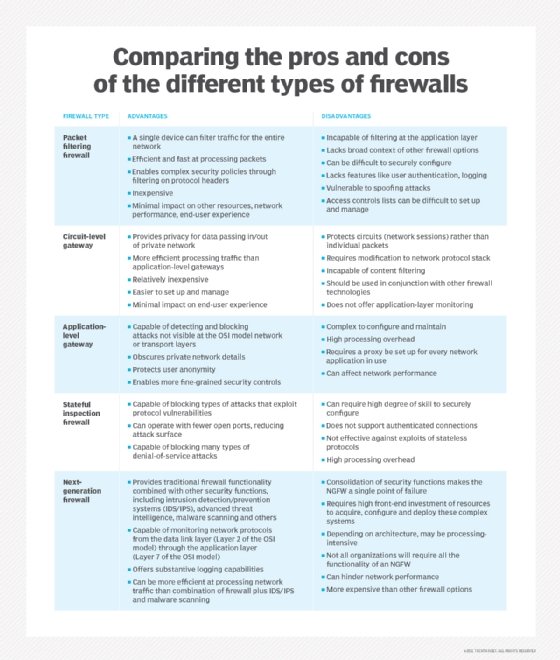
packet filtering
What is packet filtering?
Packet filtering is the process of passing or blocking data packets at a network interface by a firewall based on source and destination addresses, ports or protocols. The packet filter examines the header of each IP packet based on a set of rules and decides to prevent it from passing (drop) or allow it to pass (accept).
Most computer networks, including the internet, use packets to transmit data. Each packet is a self-contained bundle of data that can be routed by the network, and each packet has two parts. The packet header contains information about the source IP address, destination IP address, protocol and port. The packet payload contains the data to be transmitted. A packet filter is a method to decide to allow or drop each packet going through the firewall based on the header information.
To illustrate, each data packet is like a letter with the header being the To and From address on the outside and the payload being what is inside the letter. A packet filter is like deciding to forward the letter or destroy it based on the information printed on the outside. For example, the mailroom could be told to destroy any letters from a country that it doesn't do business with or to block any outgoing mail from a department that handles sensitive information.
Packet filtering firewalls are often deployed at network boundaries. For example, they may be put between a corporate network and the internet or between a server network and clients. It may also exist as software on a computer protecting its network connection.
Packet filtering is the most common and simplest type of firewall. Almost all firewall products support packet filtering.
Traditional packet filtering is relatively limited compared to the modern cyber threat landscape. This has led to new systems, such as deep packet inspection, proxy firewalls and next-generation firewalls. Packet filtering remains relevant, though, as a simple, low-cost option for small business and home use or in larger organizations when combined with other security approaches, such as intrusion detection systems or zero trust.
Packet filtering rules
Packet filtering firewalls use rules to decide if it should allow or drop the data packet. These rules are set by the firewall administrator.
Packet filtering relies on the IP packet header information and information about the firewall appliance, such as the following:
- Source IP address.
- Destination IP address.
- Source port.
- Destination port.
- Network protocol.
- IP flags.
- Firewall interface.
- Direction, ingress or egress.
Many rules are often used in conjunction with each other in a set precedence to create an overall policy.
Here is an example of packet filtering rules set up for outgoing employee internet traffic. The higher rules take precedence than the lower ones:
- Allow File Transfer Protocol traffic to a trusted IP address.
- Drop traffic to a list of known malicious IP addresses.
- Allow one internal IP address access to one file sharing IP address.
- Drop traffic to file sharing IP addresses for all other internal IP addresses.
- Allow web traffic using known ports 80 and 443.
- Drop all other traffic.
Types of packet filtering firewalls
There are a few different kinds of packet filtering firewalls.
Dynamic and static firewalls
In a static firewall, all rules are set by the administrator. The rules do not adjust automatically based on changing conditions.
A dynamic firewall can activate or deactivate rules based on changing conditions. These rules can be based on things like time or traffic. For example, a dynamic firewall could automatically add bad IP addresses to a drop list during a distributed denial-of-service attack.
Stateful and stateless firewalls
A stateless firewall does not maintain any information about connections over time. These can only make decisions based solely on predefined rules and the information present in the IP packet.
A stateful firewall can maintain information over time and retain a list of active connections. This enables the firewall to make more informed decisions. For example, if an internal client sent a request to an outside server, the stateful firewall logs this, and then, when a reply packet comes in from the server the firewall knows, it is part of the existing connection and allows it. Alternatively, if an external server sent an incoming reply with no corresponding outgoing request, the firewall drops it as malicious.
Advantages and disadvantages of packet filtering
Packet filtering as a network protection system has its advantages and disadvantages.
Advantages
- Simple to use.
- Cost-effective.
- Fast.
- Does not use a lot of compute resources.
- Deterministic, predictable behavior.
Disadvantages
- Not effective against modern attacks.
- Can be circumvented with spoofing.
- Cannot make decisions based on application or authentication.
- Rule lists can become large and hard to manage over time.








