flooding (network)
What is network flooding?
In a computer network, flooding occurs when a router uses a nonadaptive routing algorithm to send an incoming packet to every outgoing link except the node on which the packet arrived.
Flooding is a way to distribute routing protocols updates quickly to every node in a large network. Examples of these protocols include the Open Shortest Path First and Distance Vector Multicast Routing Protocol.
Network flooding also has some other uses, including the following:
- multicasting data packets from one source node to many specific nodes in a real or virtual network;
- bridging;
- peer-to-peer file sharing; and
- and ad hoc wireless networks.
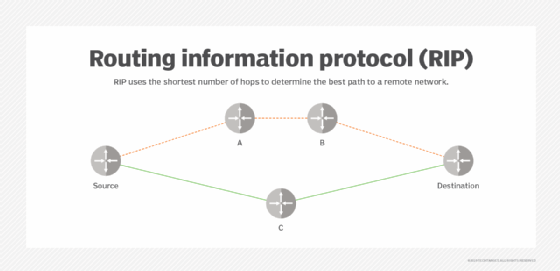
How do flooding algorithms work?
In computer science, flooding algorithms can be configured in one of two ways:
- every node acts as a sender and a receiver; or
- every node tries to send the packet to each of its counterparts except for the source node.
Either way, the end result is that the flooded information eventually reaches all nodes within the network.
What are the different types of network flooding?
Network flooding can occur in one of three ways, controlled flooding, uncontrolled flooding and selective flooding.
- In controlled flooding, two algorithms are used in order to ensure that the flooding can be contained. These algorithms are Reverse Path Forwarding and Sequence Number Controlled Flooding.
- In uncontrolled flooding, there is no conditional logic to control how the node distributes information packets to its counterparts. Without these restraints, repeated distribution of the same packet can occur. These are referred to as broadcast storm or ping storm.
- In selective flooding, nodes are configured to only send incoming packets to routers in one direction. This can help to prevent some of the mishaps that occur with uncontrolled flooding, but is not as sophisticated as controlled flooding.
The downfalls of network flooding
While network flooding is simple to implement, it can have a number of drawbacks. For example, network flooding can waste network traffic bandwidth if information packets are sent needlessly to all IP addresses when only a few require the information.
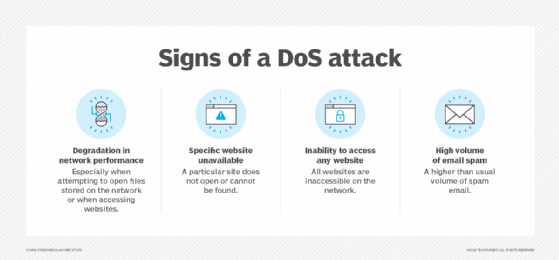
Furthermore, cybercriminals can use flooding in denial of service (DoS) attacks to cause a service timeout or to disrupt a computer network.
Network administrators can prevent flooding attacks and connectivity issues caused by uncontrolled flooding with a few best practices:
- implement a firewall to prevent cybercriminals from gaining the access they need to implement a DoS attack;
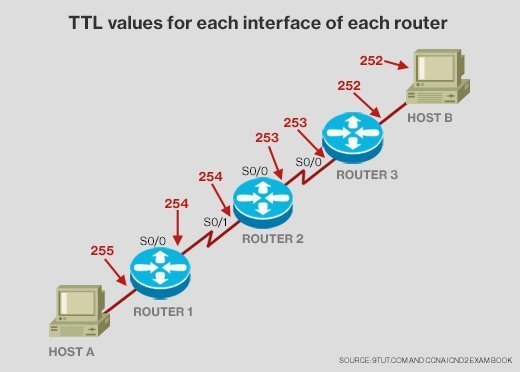
- use a time to live or hop count when implementing network flooding to prevent the number of nodes that a packet must move through to reach its final destination;
- employ controlled flooding to ensure packets are only forwarded to a node once; and
- enforce a network topology that does not allow loops.








