dynamic multipoint VPN (DMVPN)
What is a dynamic multipoint virtual private network (DMVPN)?
A dynamic multipoint virtual private network (DMVPN) is a secure network that exchanges data between sites/routers without passing traffic through an organization's virtual private network (VPN) server or router, located at its headquarters. A DMVPN allows organizations to build a VPN network with multiple sites, without the need to configure devices statically.
VPNs connect each remote site to the company headquarters. A DMVPN creates a mesh VPN topology. In this "hub and spoke" mesh, each remote site's router is configured to connect to the company's VPN hub device to provide access to the required resources.
At the same time, each site ("spoke") can connect directly with all other spokes, irrespective of their location and without having to go through the hub.
How a DMVPN works
With DMVPN, branch locations can communicate using the same resources via a public WAN or internet connection. A DMVPN runs on VPN routers and firewall concentrators. Each remote site has a router configured to connect to the company headquarters' VPN hub.
When two spokes exchange data -- for a Voice over IP call, for example -- one spoke will contact the hub, obtain the necessary information about the second spoke, and create a dynamic IPsec VPN tunnel between them. The spokes don't utilize a permanent VPN connection; instead they communicate through a centralized hub-and-spoke model that can apply VPN protection and granular access controls as required.
DMVPN also supports encryption via IPsec. These features make DMVPN a popular topology for connecting sites/branches via the internet.
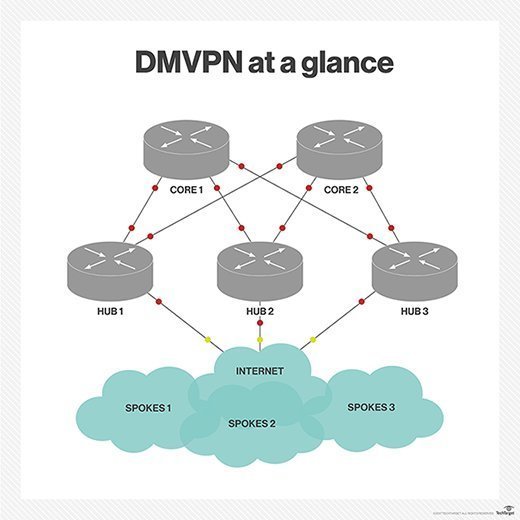
Components of a DMVPN
A DMVPN consists of four key components.
Multipoint GRE tunnel interfaces
For an enterprise network where sites need to connect, internet connections with multiple GRE tunnel interfaces can get messy and be difficult to scale. DMVPN and multipoint GRE (mGRE) allow a business to add multiple destinations, with only one tunnel interface on each router.
Essentially, mGRE features a single GRE interface on each router with the possibility of multiple destinations. This interface secures multiple IPsec tunnels and reduces the overall scope of the DMVPN configuration.
However, if two branch routers need to tunnel traffic, mGRE and point-to-point GRE may not know which IP addresses to use. To solve this issue, the Next Hop Resolution Protocol (NHRP) is used.
NHRP
The NHRP can deploy spokes with assigned IP addresses. These spokes can be connected from the central DMVPN hub.
This protocol is required by one branch router to find the public IP address of the second branch router. NHRP uses a "server-client" model, where one router functions as the NHRP server, while the other routers are the NHRP clients. In the multipoint GRE/DMVPN topology, the hub router is the NHRP server and all other routers are the spokes. Each client registers with the server and reports its public IP address, which the server tracks in its cache.
Through a process that involves registration and resolution requests from the client routers, and resolution replies from the server router, traffic is enabled between various routers in the DMVPN.
IPsec Tunnel Endpoint Discovery
Tunnel Endpoint Discovery (TED) allows routers to automatically discover IPsec endpoints, so that static crypto maps between individual IPsec tunnel endpoints need not be configured. TED allows endpoints or peers to dynamically and proactively initiate the negotiation of IPsec tunnels to discover unknown peers.
These remote peers do not need to have TED configured to be discovered by inbound TED probes. So, while configuring TED, VPN devices that receive TED probes on interfaces -- that are not configured for TED -- can negotiate a dynamically initiated tunnel using TED.
Routing protocols
Routing protocols enable the DMVPN to find routes between different endpoints efficiently and effectively. To build a scalable and stable DMVPN, it's important to choose the right routing protocol. One option is to use Open Shortest Path First (OSPF) as the interior routing protocol. OSPF is best suited for small-scale DMVPN deployments.
For large-scale implementations, the Enhanced Interior Gateway Routing Protocol (EIGRP) or Border Gateway Protocol (BGP) are more suitable. EIGRP is not restricted by the topology limitations of a link state protocol and is easier to deploy and scale in a DMVPN topology. BGP can scale to many peers and routes and it puts less strain on the routers compared to other routing protocols.
DMVPN phases
The DMVPN design model consists of three phases.
Phase 1
In phase 1, the DMVPN spokes are registered with the hub. In this early phase, there is no direct communication between the spokes, so all traffic goes through the hub. Each spoke uses regular point-to-point GRE tunnel interfaces and requires only a summary or default route to the hub to reach other spokes. As a result, the routing configuration in this phase is simple.
Phase 2
This phase allows spoke-to-spoke tunnel deployment with all spoke routers using multipoint GRE tunnels. These spoke-to-spoke tunnels are on demand, i.e., triggered based on the spoke traffic. This means the data does not have to travel to a central hub first. While the hub is used for the control plane, it is not necessarily in the data plane. This key fact differentiates Phase 2 from Phase 1.
Phase 3
In phase 3, the spoke-to-spoke tunnels are deployed without using specific pre-made routes. To secure those routes on the fly, this phase uses NHRP traffic indication messages (redirect and shortcuts) from the hub. This phase improves the scalability of phase 2.
DMVPN benefits
A dynamic multipoint VPN provides a number of benefits, including the following:
Simplified hub/spoke router configuration
With DMVPN, multiple tunnel interfaces for each branch (spoke) VPN are not required. Instead, the simple hub-and-spoke configuration provides on-demand mesh connectivity with dynamic routing and IP Multicast. DMVPN also supports "zero touch" deployment to add more remote sites. This simplified, scalable topology is ideal for organizations that need encrypted WAN connectivity between remote sites, including small office/home office, medium-sized and large organizations.
Support for dynamic spoke deployment with NHRP
With DMVPN and the NHRP, spokes can be deployed using dynamically assigned public IP addresses. Each spoke can make a VPN tunnel with other spokes by finding their public IP addresses. It does this by querying the NHRP database for the real IP addresses of the destination spokes.
Lower administration costs
DMVPN simplifies the WAN network topology by reducing configuration overhead. There is no need to configure crypto maps tied to the physical interface or make changes at the hub to add more spokes. Plus, centralized configuration changes at the hub control split tunneling behaviors, which further simplifies the configuration and reduces costs.
QoS support
DMVPN supports multiple advanced quality of service (QoS) mechanisms, including traffic shaping at hub interfaces on a per-spoke/per-spoke-group basis, as well as hub-to-spoke/spoke-to-spoke QoS policies. It also supports dynamic QoS policies that automatically attach QoS templates to tunnels as they are established.
High scalability and availability
DMVPN integrates encryption within the server load balancer or distributed to dedicated headend VPN routers. It can scale to thousands of spokes with hierarchical hub deployments for more scalability. To enhance performance, tunnels are load-balanced over available hubs.
Network address translation traversal
DMVPN enables enhanced security for branch subnets by supporting spoke routers that are running network address translation (NAT) or are placed behind dynamic NAT devices. It also brings efficient and scalable distribution of one-to-many and many-to-many traffic with support for IP multicast traffic between the hub and spokes.
Advantages of DMVPN over traditional VPN
A DMVPN offers many benefits over a permanent VPN, including the following:
- superior network speed and Performance reliability;
- reduced cost for secure communications;
- better connectivity between branches by integrating VPN into existing communication practices;
- fewer network delays;
- conservation of WAN bandwidth;
- reduced bandwidth requirements at the hub;
- increased network resiliency and redundancy; and
- secure routing with IPsec.







