What is User Datagram Protocol (UDP)?
User Datagram Protocol (UDP) is a communications protocol primarily used to establish low-latency and loss-tolerating connections between applications on the internet.
UDP speeds up transmissions because it enables data transfer before the receiving party provides an agreement. As a result, UDP is beneficial in time-sensitive communications, such as voice over Internet Protocol (VoIP), domain name system (DNS) lookup, and video or audio playback.
UDP is an alternative to Transmission Control Protocol (TCP). Both UDP and TCP run on top of IP and are sometimes referred to as UDP/IP or TCP/IP. However, there are important distinctions between the two. For example, UDP enables process-to-process communication, while TCP supports host-to-host communication.
TCP sends individual packets and is a reliable transport medium. UDP sends messages, called datagrams, and is considered a best-effort mode of communication. This means UDP doesn't guarantee data delivery or offer special features to retransmit lost or corrupted messages.
UDP provides the following two services not provided by the IP layer:
- Port numbers. Port numbers help distinguish different user requests on a network.
- Checksum. An optional capability that verifies if data arrived intact.
UDP features
UDP's attributes make it beneficial for applications that can tolerate lost data. UDP features include the following:
- Packets can be dropped and received in a different order than they were transmitted, which is suitable for real-time applications where latency might be a concern.
- Transaction-based protocols, such as DNS or Network Time Protocol, can use UDP for communication.
- UDP is useful in locations with many clients where real-time error correction isn't necessary, such as online gaming, voice or video conferencing and media streaming.
- UDP is connectionless; no connection must be established before data is transmitted, making it faster.
UDP header composition
UDP uses headers when packaging message data for transfer over network connections. UDP headers contain a set of parameters, called fields, defined by the protocol's technical specifications. The UDP header includes the following four fields, each of which is 2 bytes:
- Source port number. The number of the sender.
- Destination port number. The number of the port to which the datagram is addressed.
- Length. The length in bytes of the UDP header and any encapsulated data.
- Checksum. These are used in error checking. Internet Protocol version 6 requires checksums, but they're optional in IPv4.
How UDP works
UDP uses IP to send a datagram from one computer to another. It gathers data in a UDP packet and adds its header information to the packet. This data consists of the source and destination communication ports, the packet length and a checksum. After UDP packets are encapsulated in an IP packet, they are sent to their destinations.
Unlike TCP, UDP doesn't guarantee that the packets will reach the correct destinations. This means UDP doesn't connect to the receiving computer directly, which TCP does. Instead, it sends the data out and relies on the devices between the sending and receiving computers to move the data where it needs to go.
Most applications wait for replies they expect to receive from packets sent with UDP. If an application doesn't receive a reply within a specific time frame, it either sends the packet again or stops trying.
UDP uses a simple transmission model that doesn't include handshake dialogues to provide reliability, ordering or data integrity. Consequently, UDP traffic can be unreliable. Packets might arrive out of order, appear to have duplicates or disappear without warning.
Although this transmission method doesn't guarantee the data will reach its destination, it does have low overhead and is popular for services that don't have to work the first time.
TCP vs. UDP
TCP and UDP are part of the TCP/IP suite, which includes several protocols for network communications.
TCP has emerged as the dominant protocol for the bulk of internet connectivity due to its ability to break large data sets into individual packets, check for and resend lost packets, and reassemble packets in the correct sequence. However, these additional services come at a cost in terms of data overhead and latency.
In contrast, UDP is considered a connectionless protocol because it doesn't require establishing a virtual circuit before any data transfer occurs. The communication protocol only sends packets, which means it has much lower bandwidth overhead and latency. With UDP, packets might take different paths between sender and receiver, resulting in some packets being lost or received out of order.
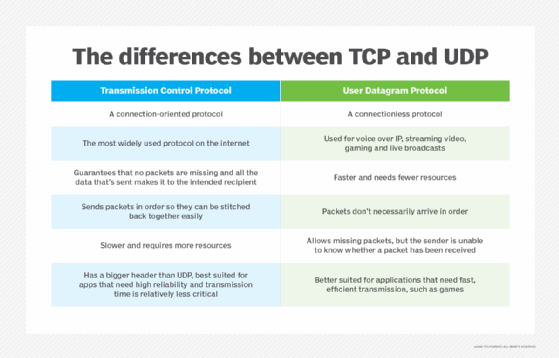
UDP characteristics include the following:
- Connectionless.
- Used for VoIP, video streaming, gaming and live broadcasts.
- Faster and requires fewer resources.
- Packets don't necessarily arrive in order.
- Allows missing packets, which is useful for real-time communications, but the sender doesn't receive an acknowledgment of whether a packet has been received.
- Better suited for applications such as games that need fast, efficient transmission and can tolerate occasional packet loss.
TCP characteristics include the following:
- Connection-oriented.
- The most widely used protocol on the internet.
- Guarantees that no packets go missing and all sent data arrives at the intended recipient.
- Sends packets in order so they can be stitched back together easily.
- Slower and requires more resources.
- Has a bigger header than UDP.
- Best suited for apps that need high reliability, and transmission time is relatively less critical.
UDP applications and use cases
Applications of UDP include the following:
- Lossless data transmission.
- Gaming, voice and video.
- Services that don't need fixed packet transmission.
- Multicasting and routing update protocols.
- Fast applications.
- Domain name system lookup.
Lossless data transmission
Applications that require lossless data transmission can use UDP. For example, an application configured to manage retransmitting lost packets and correctly arrange received packets might use UDP. This approach can help improve the data transfer rate of large files compared to TCP.
In the Open Systems Interconnection communication model, UDP is in Layer 4, the transport layer. To help manage data transmission services, UDP works with higher-level protocols, including Trivial File Transfer Protocol, Real Time Streaming Protocol and Simple Network Management Protocol.
Gaming, voice and video
UDP is an ideal protocol for network applications in which perceived latency is critical, such as gaming, voice and video communications. These applications can suffer some data loss without adversely affecting their perceived quality. However, in some cases, forward error correction techniques are used in addition to UDP to improve audio and video quality despite some loss.
Services that don't need fixed packet transmission
UDP can also be used in applications that depend on the reliable exchange of information but should have their own methods for answering packets. These services are advantageous because they aren't bound to fixed patterns to guarantee the completeness and correctness of the data packets sent. Users can decide how and when to respond to incorrect or unsorted information.
Multicasting and routing update protocols
Multicasting can use UDP because it supports packet switching. In addition, some routing update protocols, such as Routing Information Protocol, can also use UDP.
Fast applications
UDP can be used in applications where speed -- rather than reliability -- is critical. For example, it might be prudent to use UDP in an application that sends data from a fast acquisition where losing some data points is OK.
DNS lookup
DNS lookup takes a human-readable domain name -- such as techtarget.com -- and turns it into an IP address for a machine to consume. Due to its lightweight nature and rapid transit, UDP enables quick, small DNS queries and responses to facilitate fast name resolution.
How and why UDP is used in DDoS attacks
UDP's connectionless nature means that no handshake is required; the flip side of this convenience is that data can flow into a system without getting an all-clear signal from that system.
Since a DDoS (distributed denial-of-service) attack bombards a system with service requests designed to overwhelm it by maxing out its services, UDP is an ideal point of attack for hackers, opening the door to crashing a target server with fake requests.
Organizations can defend against UDP vulnerabilities by implementing a combination of security measures, including virtual private networks, firewalls and content delivery networks.
DNS uses both TCP and UDP ports to communicate. Learn how these two transport layer protocols compare.






