What is the Server Message Block (SMB) protocol? How does it work?
The Server Message Block (SMB) protocol is a client-server communication protocol used for sharing access to files, printers, serial ports and other resources on a network. It can also carry transaction protocols for interprocess communication.
A group at IBM developed the SMB protocol in the 1980s. The protocol has since spawned multiple variants, also known as dialects, to meet evolving network requirements over the years. Throughout that time, SMB has been widely implemented and continues to be one of the most popular solutions for file sharing in the workplace.
What is the Server Message Block protocol used for?
The SMB protocol is mainly used to facilitate shared access to the resources on a network. These may be printers, serial ports, files, directories, etc. SMB also provides client applications with a secure and controlled method for opening, reading, moving, creating and updating files on remote servers. The protocol can also communicate with server programs configured to receive SMB client requests.
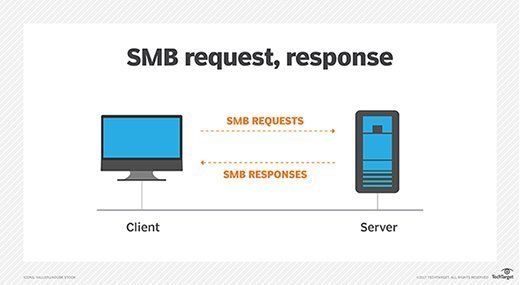
How does the SMB protocol work?
Known as a response-request protocol, the SMB protocol is one of the most common methods used for network communications. In this model, a series of request-response messages are used to initiate and facilitate communication between devices on a computer network.
The client sends an SMB request to the server to initiate the connection. When the server receives the request, it sends an SMB response back to the client, establishing the communication channel necessary for a two-way conversation. Once it is granted access, the client can access the required resource for reading, writing, executing and so on. Since the network server has a resource that it shares with one or more clients, the protocol is also known as a server-client protocol.
The SMB protocol operates at the application layer but relies on lower network levels for transport. At one time, SMB ran on top of Network BIOS over TCP/IP or, to a lesser degree, legacy protocols, such as Internetwork Packet Exchange or NetBIOS Extended User Interface.
When SMB was using NBT, it relied on ports 137, 138 and 139 for transport. Now, SMB runs directly over TCP/IP and uses port 445. Port 445 supports data encryption and digital signing of SMB packets, providing a more secure means of communication than port 139. Communications with devices that do not support SMB directly over TCP/IP require the use of NetBIOS over the transport protocol.
SMB protocol in Windows
Over the years, SMB has been used primarily to connect Windows computers. Microsoft Windows operating systems (OSes) since Windows 95 have included client and server SMB protocol support.
Windows Server 2012 and up include the SMB 3.0 feature, enabling applications to do the following:
- Access and read resources, including files, at a remote server.
- Create and update files on the remote server.
- Communicate with server programs that can receive SMB client requests.
The SMB 3.0 protocol can also be used to store virtual machine files -- by standalone file servers and clustered file servers -- to store user database files on SMB file shares and to reduce application latencies over wide area networks (WANs).
These OSes include numerous functionalities to streamline resource sharing and access over a network. One such functionality is SMB Transparent Failover, which simplifies the hardware or software maintenance of nodes in a clustered file server. Admins can perform these maintenance tasks without interrupting any server applications that may be storing data on the file shares. Other key SMB 3.0 features in Windows Server include SMB Scale Out to create file shares that provide simultaneous access to data files, SMB performance counters that enable admins to analyze the performance of SMB 3.0 file shares, SMB Directory Leasing that reduces round trips from client to server and maintains cache coherency, and SMB Encryption that encrypts and protects SMB data on untrusted networks from eavesdropping.
Most other OSes also include client components for connecting to SMB resources. In addition, Unix-based systems can use Samba to facilitate SMB access to file and print services.
What are SMB protocol dialects?
Since the SMB protocol was introduced in the 1980s, a number of SMB dialects have been released that have improved on the original implementation, delivering greater capabilities, scalability, security and efficiency. A client and server can implement different SMB dialects. If they do, the systems must first negotiate the differences between editions before starting a session.
Here is a brief overview of the most notable dialects:
- SMB 1.0 (1984). SMB 1.0 was created by IBM for file sharing in DOS. It introduced opportunistic locking (OpLock) as a client-side caching mechanism designed to reduce network traffic. Microsoft later included the SMB protocol in its LAN Manager product and incorporated SMB support into the Windows Server OS.
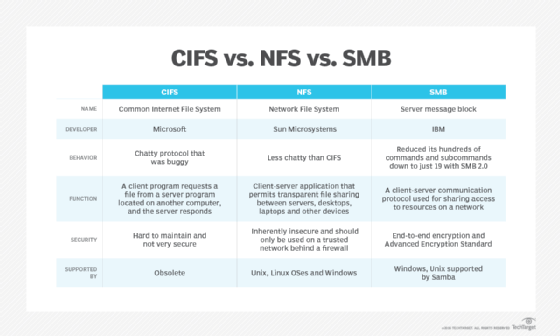
- Common Internet File System (1996). CIFS, an improvement over SMB 1.0, is a Microsoft-developed SMB dialect that debuted in Windows 95. CIFS added support for larger file sizes, direct transport over TCP/IP, and symbolic links and hard links.
- SMB 2.0 (2006). SMB 2.0 was released with Windows Vista in 2006 and Windows Server 2008. It reduced chattiness in SMB 1.0 to improve the protocol's performance and enhance its efficiency, scalability and resiliency. It also added support for WAN acceleration.
- SMB 2.1 (2010). SMB 2.1 was introduced with Windows Server 2008 R2 and Windows 7. The client OpLock leasing model replaced OpLock to enhance caching and improve performance. Other updates included large maximum transmission unit support and improved energy efficiency, which enabled clients with open files from an SMB server to enter sleep mode.
- SMB 3.0 (2012). SMB 3.0 debuted in Windows 8 and Windows Server 2012. It added several significant upgrades to improve availability, performance, backup, security and management. Noteworthy new features included SMB Multichannel, SMB Direct, Transparent Failover of client access, Remote Volume Shadow Copy Service support, SMB Encryption and more.
- SMB 3.0.2 (2014). SMB 3.0.2 was introduced in Windows 8.1 and Windows Server 2012 R2. It included performance updates and the ability to disable CIFS/SMB 1.0 support, including removal of the related binaries. Other features included CopyFile SRV_COPYCHUNK over SMB support, performance improvements for small input/output workloads and automatic rebalancing of scale-out file server clients.
- SMB 3.1.1 (2015). SMB 3.1.1 was released with Windows 10 and Windows Server 2016. It added support for advanced encryption, preauthentication integrity to prevent man-in-the-middle (MitM) attacks and Cluster Dialect Fencing, among other updates. Additional features included directory caching, rolling cluster upgrades and direct client support.
Why is SMB vulnerable?
In 2017, the WannaCry and Petya ransomware attacks exploited a vulnerability in SMB 1.0 that made it possible to load malware on vulnerable clients and then propagate the malware across networks. Many of these attacks were the result of threat actors exploiting known vulnerabilities in SMB 1.0, such as EternalBlue, EternalRomance, EternalChampion and EternalSynergy.
Microsoft subsequently released patches to address these vulnerabilities. However, experts have advised users and administrators to disable SMB 1.0/CIFS on all systems and upgrade to the more secure SMB 3.0.
Is the SMB protocol safe?
SMB 3.0 and later are far more secure than previous dialects, having introduced a number of protections. For example, SMB 3.0 added end-to-end data encryption while protecting data from eavesdropping. Encryption may be enabled for any scenario where data traverses over an untrusted network without incurring costs for deploying IPsec, specialized hardware or WAN accelerators. SMB 3.0 also offered secure dialect negotiation, which helps protect against MitM attacks.
SMB 3.1.1 improved on security even further by updating the encryption capabilities of SMB 3.0. The updated protocol also adds preauthentication integrity to protect SMB connections and authentication messages again MitM attacks. It also included a mechanism for negotiating the crypto-algorithm -- AES-128-CCM and AES-128-GCM -- on a per-connection basis.
That said, SMB 3.0 is not completely safe. In 2020, a vulnerability dubbed SMBGhost (CoronaBlue) was discovered in SMB 3.0. If exploited, it could expose users to remote code execution. To protect users, admins must adopt multiple security strategies, including patching against known vulnerabilities, using secure authentication methods and restricting SMB at the host level.
CIFS vs. SMB
As noted above, CIFS is an early dialect of the SMB protocol developed by Microsoft. Although the terms SMB and CIFS are sometimes used interchangeably, CIFS refers specifically to a single implementation of SMB. That said, application interfaces and technical documentation often refer to them as one and the same, particularly SMB 1.0 and CIFS, using labels such as SMB 1.0/CIFS.
However, the distinction between dialects is important to recognize. For example, SMB 1.0 and CIFS do not have the same level of security protections found in later dialects, as demonstrated by the WannaCry ransomware. SMB 3.0 provides far more advanced security protections. For this reason, most modern systems use the newer SMB dialects. For example, Windows 10 and Windows Server 2012 and newer support SMB 3.1.1, the most recent SMB dialect.
Dialects also make a difference when it comes to performance. For instance, CIFS was noted for being a chatty protocol that bogged WAN performance due to the combined burdens of latency and numerous acknowledgments. The dialect to follow, SMB 2.0, improved the protocol's efficiency by drastically reducing its hundreds of commands and subcommands down to just 19.
Samba vs. SMB
Released in 1992, Samba is an open source implementation of the SMB protocol for Unix systems and Linux distributions. The Samba platform includes a server that enables various client types to access SMB resources.
The server supports file sharing and print services, authentication and authorization, name resolution, and service announcements (browsing) between Linux/Unix servers and Windows clients. For example, Samba can be installed on a Unix server to provide file and print services to Windows 10 desktops.
In addition, Samba makes it possible to integrate Linux/Unix servers and desktops in an Active Directory environment. Windows Server systems include built-in SMB support. However, some macOS and Linux systems require Samba for SMB access.
SMB vs. SFTP
Like SMB, Secure File Transfer Protocol (SFTP) enables secure file transfers between a remote host and one or more local systems. It enables users to securely access, upload, retrieve, download and manipulate remote files over a shared network. All data is encrypted and an Secure Shell (SSH) tunnel is created to safeguard files and ensure secure transfers. Admins can configure granular user access controls to further strengthen security.
One of the differences between SFTP and SMB is that SMB enables the sharing of entire file directories. These directories can be mounted as network drives to enable share-level access. Even so, SMB is better suited for small file transfers on a local area network, while SFTP can efficiently handle large batches or files, even over longer distances.
Another difference is that SFTP uses SSH port 22 to enable secure connections and communications, while SMB uses port 445 (3.0) or 139 (older versions). Usability also differs between SMB and SFTP. Whereas SMB shares automatically appear as standard network drives and can be easily accessed via Windows File Explorer, an FTP client is required to use SFTP.
Older versions of SMB operated over TCP for file transfers and did not provide data encryption support. Encryption is included in SMB 3.0 and above. In Windows Server 2012, SMB 3.1.1 also includes a mechanism to negotiate the crypto-algorithm per connection. The newer versions of SMB also include other security features, like preauthentication integrity and reduced application latencies, to provide security benefits that are on par with SFTP and SSH encryption.
Networking enables the internet to function, relying on several key protocols. These essential network protocols facilitate communication and connection across the internet. Learn about common network protocols and their functions.







