SYN scanning
What is SYN scanning?
SYN scanning is a tactic that a malicious hacker can use to determine the state of a communications port without establishing a full connection.
This approach, one of the oldest in the repertoire of hackers, is sometimes used to perform a denial-of-service (DoS) attack. SYN scanning is also known as half-open scanning.
How does SYN scanning work?
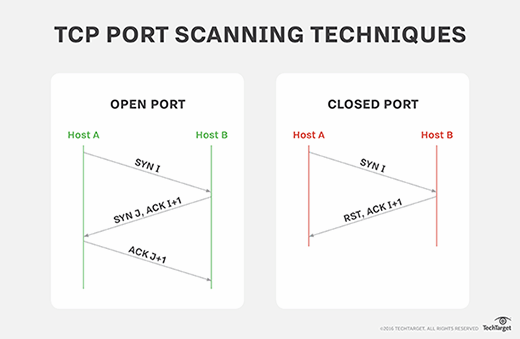
In SYN scanning, similar to port scanning, the threat actor attempts to set up a Transmission Control Protocol/Internet Protocol (TCP/IP) connection with a server at every possible port. This is done by sending a SYN (synchronization) packet, as if to initiate a three-way handshake, to every port on the server.
If the server replies with an ACK (acknowledgement) response -- or SYN/ACK (synchronization acknowledged) packet -- from a particular port, it means the port is open. Then, the hostile client sends an RST (reset) packet.
As a result, the server assumes that there's been a communications error and the client has not established a connection. In this scenario, the assumption is wrong. The open port remains open and vulnerable to exploitation.
If the server responds with an RST packet from a particular port, it indicates that the port is closed and cannot be exploited.
When a hacker continuously sends large numbers of SYN packets to a server, it can consume server resources. What results is that few or no communications from legitimate clients can take place.
As part of a extensive network security program, it's important to understand that other port scanning techniques can be used in conjunction with SYN scanning or as a substitute for it.
What other types of port scans exist?
The following is a list of some scan types that can be done by a port scanner.
TCP SYN scan
The TCP SYN scan -- a variant of the traditional SYN scan -- is commonly used. It is a quick and efficient scan, not restricted by firewalls since it never completes the full TCP connection. For this reason, TCP SYN scanning is also commonly referred to as half-open scanning and can indicate open, filtered and closed port states.
It works by sending a SYN packet in an attempt to open a connection. A SYN/ACK response indicates an open TCP port, whereas an RST response indicates a closed port. If no response is received or if an Internet Control Message Protocol (ICMP) unreachable error is received, it indicates a filtered state.
On rare occasions, a SYN packet may be returned without the ACK flag, indicating an open port and the presence of a TCP three-way handshake.
TCP connect scan
If a SYN scan can't be performed, a TCP connect scan is a popular alternative for hackers. A TCP scan is common for users who don't have raw packet access privileges, but it is less efficient than a SYN scan. Instead of requiring a raw packet like other scan types, Nmap will request a connection with the target operating system (OS) using a system call.
UDP scan
Instead of running over TCP, hackers can deploy User Datagram Protocol (UDP) scans over domain name system, Dynamic Host Configuration Protocol or Simple Network Management Protocol. They are slower and more complex to send than a SYN or TCP packet but can be combined with those types of scans to check UDP ports.
UDP scans are done by sending UDP packets to all ports. If an ICMP unreachable error comes back, the port is closed. But, if it responds with a UDP packet, the port is open. If no response is received, the port is identified as an open/filtered port.
It's important to note that hosts such as Linux are strict about the number of ICMP messages that can be received during a session. Linux's limit is one per second.
Stealth scans
Stealth scan types are those where packet flags cause the target system to respond without having a fully established connection. Stealth scanning is used by hackers to circumvent the intrusion detection system (IDS), making it a significant threat.
Therefore, it's important for system administrators to run stealth scans on their systems to penetration test the firewall and the functionality of the IDS.
Some common stealth scans include the following:
- FIN (finished) scans. These send FIN packets with a flag set. If an RST is returned, the port is considered open; if nothing is received, it's considered closed.
- NULL scans. These don't establish any flags on the TCP packet. In other words, the TCP flag header is set to 0, and response protocols are the same as FIN scans.
- Xmas scans. These utilize FIN, URG (urgent) and PSH (push) flags, which light up the packet like a Christmas tree. If an RST packed is received, the port is considered closed; no response indicates an open or filtered state. An ICMP unreachable error also indicates a filtered port.
Major OSes, like Microsoft Windows, have built-in protection against these types of scans. They accomplish this by automatically sending RST responses regardless of the true port status.







