Point-to-Point Protocol (PPP)
What is Point-to-Point Protocol (PPP)?
Point-to-Point Protocol (PPP) refers to a suite of computer communication protocols that provide a standard way to transport multiprotocol data over point-to-point links. PPP has the following three main components:
- a way to encapsulate multiprotocol datagrams;
- Link Control Protocol to establish, configure and test the data link connection; and
- a group of separate network control protocols that establish and configure different types of network layer protocols.
In terms of the Open Systems Interconnection model, however, PPP provides Layer 2, or data link layer, service that creates the foundation for network layer protocols to operate on top.
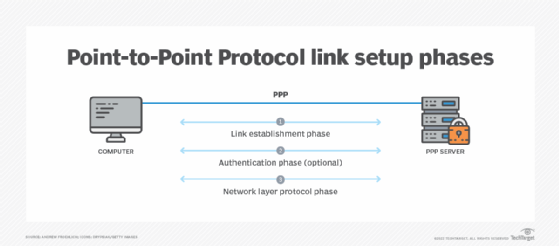
From an operational standpoint, PPP is a peer-to-peer protocol, meaning that either side of the link can be used to establish a PPP connection. However, when it is put in real-world situations, there typically is a PPP server that operates as a connection hub for multiple PPP clients.
The PPP server sits idle until a PPP client attempts to establish a connection. If the PPP server is configured for authentication, the server responds to the client with an authentication request. PPP can use Challenge-Handshake Authentication Protocol or Password Authentication Protocol. Once authenticated, the final step is to establish the Network Control Protocol (NCP) used between systems. The most commonly used NCP is Internet Protocol Control Protocol. Once established, the client and server can begin communicating and transmitting packets between each other.
What is PPP used for?
PPP is a full-duplex protocol that can be used on a variety of physical media, including twisted-pair copper wire, fiber optic lines or satellite links. It is a standards-based protocol outlined in the Internet Engineering Task Force's Request for Comments 1661 that was issued in 1994.
PPP can provide services over multiple mediums, ranging from dial-up modems to Secure Sockets Layer (SSL)-encrypted virtual private network (VPN) connections. PPP uses a variation of High-level Data Link Control for packet encapsulation. For example, a high-security application on a company network connects to the network via the VPN and establishes an SSL link. The client for the application can then establish a PPP tunnel on top of that, which carries IP packets to the application's server.
PPP is also used to tunnel IP or other network Layer 3 data between two directly connected nodes over a physical connection or over a direct link. Since IP and TCP do not support point-to-point connections, the use of PPP can enable them over Ethernet and other physical media.
However, the most popular use of PPP was during the days of dial-up modems throughout the mid- to late 1990s. Customers would install PPP client software on their modem-attached computers and use the protocol suite to dial in and authenticate to their internet service provider (ISP). In turn, the PPP server would connect to the internet on the back end and be used as an aggregate internet access point for all dial-up clients.
Point-to-point protocols are sometimes considered members of the TCP/IP suite of protocols. Variations of PPP exist for running over Ethernet using the PPP over Ethernet (PPPoE) specification and for asynchronous transfer mode using the PPP over ATM specification. PPPoE remains widely used today by ISPs that use Digital Subscriber Line (DSL). However, its use is often hidden from customer view. For example, it has been used to connect DSL and cable modems to their back-end services. Yet, for the most part, the customer does not interact with PPP directly. Instead, it is handled transparently through a PPPoE-capable DSL modem or router.
Learn about seven TCP/IP vulnerabilities and what steps organizations can take to help prevent security issues.







