What is the Nessus vulnerability scanning platform?
Nessus is a platform developed by Tenable that scans for security vulnerabilities in devices, applications, operating systems, cloud services and other network resources. Originally launched as an open source tool in 1998, its enterprise edition became a commercial product in 2005.
Nessus is now available in two enterprise versions: Nessus Professional and Nessus Expert. Both versions support unlimited IT vulnerability assessments and multiple systems for vulnerability scoring. Nessus Expert also includes capabilities that are not available in Nessus Professional, such as web application scanning, external attack surface scanning and cloud infrastructure scanning.
What is Nessus used for?
The Nessus platform (officially known as Tenable Nessus) is a vulnerability assessment solution that enables organizations to proactively identify and fix security weaknesses or vulnerabilities across their attack surface before cyberattackers have a chance to exploit them. In doing so, they can stay ahead of these adversaries and better protect their business-critical assets from compromise, theft and damage.
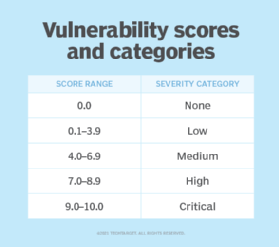
Nessus identifies software flaws, missing patches, malware and misconfiguration errors across a wide range of operating systems, devices and applications used in organizations. It also provides configuration, compliance and security audits that enable IT teams to expose previously unknown vulnerabilities that make the business susceptible to cyberattacks and data breaches. Furthermore, Nessus supports multiple vulnerability scoring systems, including CVSS (Common Vulnerability Scoring System) v4, EPSS and Tenable's Vulnerability Priority Rating (VPR) feature, so firms and their security teams can effectively prioritize vulnerability remediation.
How does Nessus work?
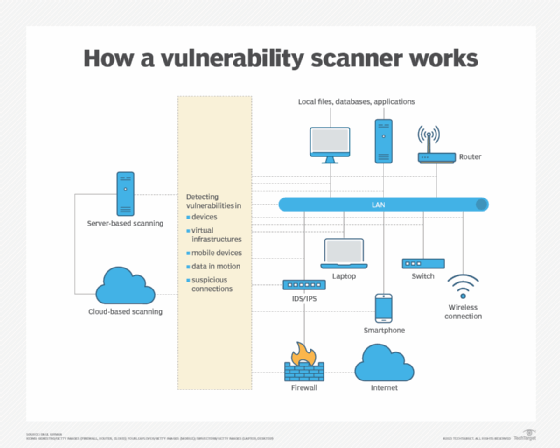
The Nessus vulnerability scanner scans the IT assets on an organization's attack surface. These scans run regardless of operating systems, devices and applications to identify the vulnerabilities, misconfigurations, software flaws and noncompliant conditions associated with each asset. Nessus compares this information against a database of known issues and generates detailed and configurable reports outlining the discovered vulnerabilities to facilitate remediation.
Nessus includes preconfigured scan templates that enable IT teams to understand where the vulnerabilities exist, which helps them take action to remediate those vulnerabilities. In addition, using out-of-the-box compliance and configuration templates, they can audit the organization's configuration compliance against globally accepted benchmarks and best practices like Center for Internet Security (CIS) and take action to close compliance gaps.
Key features of Nessus
A key feature of Nessus is its vast and growing plugin database. This database is updated with over 100 new plugins that are released weekly within 24 hours of vulnerability disclosure. Also, these plugins update automatically in real time to help IT and security teams speed up assessment, research and remediation of vulnerabilities. They are also dynamically compiled, reducing the database footprint and improving scan performance, efficiency and completion time. These plugins can be customized to create specific checks unique to an organization's application ecosystem and security needs.
Both versions of Nessus include the Predictive Prioritization capability via VPR. VPR -- which is generated by combining Tenable-collected vulnerability data with third-party vulnerability and threat data -- enables IT teams to identify vulnerabilities by their severity. With this information, they can determine which threats pose the greatest risk and highest urgency.
Another key Nessus feature is Live Results, which performs intelligent vulnerability assessment in offline mode so IT teams don't have to run a scan every time a plugin updates. They simply need to log into the platform to get visibility into all potential vulnerabilities based on scan history. And they can also validate vulnerabilities to simplify the process of vulnerability assessments, prioritization and remediation.
Nessus also provides the ability to create configurable reports in a variety of formats, including HTML, comma-separated values and Nessus XML. Reports can be filtered and customized depending on what information is most useful, such as vulnerability types, vulnerabilities by host, vulnerabilities by client, etc.
Another important feature in Nessus is Grouped View. Nessus groups similar issues or categories of vulnerabilities and presents them in one thread, enabling easier vulnerability assessment and prioritization.
The Nessus packet capture feature enables teams to debug and troubleshoot scanning issues, so teams can debug such issues quickly. This minimizes interruptions and provides continuous protection for the enterprise IT environment.
In addition to the above features, Nessus Expert also includes the following:
- Support for asset discovery (software, hardware, cloud) in the IT environment.
- Audits of operating systems, databases, applications and network infrastructure.
- Audits against security framework standards and internal/regulatory requirements.
- Active Directory (AD) checks.
- Version and change control for servers and endpoints.
- Integration-ready scan results -- with third-party IT and security platforms.
Types of Nessus scans
Both Nessus Professional and Nessus Expert provide unlimited IT vulnerability assessments plus vulnerability scoring with CVSS v4, EPSS and Tenable VPR (for top 10 vulnerabilities). The Expert version also provides web application scans, external attack surface scans and cloud infrastructure scans.
Web application scanning enables organizations to discover and remediate vulnerabilities in web applications, fortifying these assets against attacks and compromise. When running these scans with Nessus Expert, organizations can add five fully qualified domain names (FQDNs) to provide the exact locations of web applications in the DNS for vulnerability scanning. Nessus also includes the option to add FQDNs as needed.
Through external attack surface scans and cloud infrastructure scans, security teams address more threats that put the organization at an increased risk of cyberattacks. As the attack surface expands beyond traditional desktops, workstations and network equipment to include more internet-facing and cloud-native assets, the automated point-in-time assessments provided by Nessus Expert allow teams to quickly identify and remediate vulnerabilities.
Benefits of Nessus scans
In addition to finding and fixing vulnerabilities in traditional IT assets, internet-facing assets, cloud infrastructure and web applications, companies can also use Nessus Expert to scan their infrastructure as code (IaC) repositories. By doing so, they can scan their cloud services and infrastructure before pushing code to production -- an approach known as shift left -- to prevent unknown risk and confidently deploy new apps and workloads to the cloud.
The other benefits of Nessus scans include the following:
- Teams can proactively assess and remediate vulnerabilities for all kinds of assets and workloads.
- They can scan for disruptive and potentially costly vulnerabilities before code deployment.
- Early and frequent scans can help prevent vulnerabilities, misconfigurations and other issues from reaching cloud production instances.
- Scans are supported by commercial threat intelligence feeds, thus highlighting malware and ransomware running on hosts and providing actionable insights for remediation efforts.
- Scans cover over 47,000 unique IT assets and can also identify more than 400 zero-day vulnerabilities (Nessus Expert).
What are the pros and cons of Nessus?
New security vulnerabilities are emerging every day. Organizations need to be aware of these vulnerabilities and proactively prevent them from harming their assets. Nessus provides a fast, user-friendly way to find and fix vulnerabilities in many kinds of IT assets, including internet-facing and cloud-based resources.
As of January 2025, Nessus covers more than 77,000 Common Vulnerabilities and Exposures (CVEs) to provide broad and deep vulnerability coverage for organizations and their security teams. Additionally, Tenable Research maintains programs to detect new vulnerabilities. These programs, known as plugins, contain vulnerability information and simple remediation actions for security teams. The Nessus plugin library contains more than 227,000 plugins covering vulnerabilities across four severity types: low, medium, high and critical.
Nessus provides more than 450 preconfigured templates to help users understand where vulnerabilities are present. They can use these templates to run basic network scans, advanced scans, advanced dynamic scans, malware scans, as well as scans to identify vulnerabilities in mobile devices, web applications, AD, etc. Nessus also provides prebuilt templates to detect WannaCry ransomware, SolarWinds Solorigate vulnerabilities and Apache Log4j CVE. Templates are also available to check configuration compliance against internal best practices and regulatory requirements like CIS benchmarks .
Another benefit of Nessus is that it has a low false-positive rate of 0.32 defects per 1 million scans. This indicates a rate that's better than Six Sigma accuracy. Too many false positives can overwhelm security teams and lead to alert fatigue, causing legitimate threats to be overlooked. This is why a low false-positive rate is highly desirable in a vulnerability scanner.
Nessus is suitable for a wide range of use cases. For example, penetration testers can use Nessus to find major vulnerabilities and then use this information to guide their full breach simulations. Similarly, cybersecurity consultants can use Nessus to find vulnerabilities on organizations' networks. They can also deliver comprehensive reports that include information about these vulnerabilities and provide actionable remediation suggestions to help the client organization strengthen its overall security posture.
Finally, Nessus provides an intuitive experience to users, particularly those on the front lines of an organization's security infrastructure. Also, it is a highly portable vulnerability scanner, making it a useful tool for security professionals who frequently move between locations.
For some organizations, the chief drawback of Nessus is its price. Nessus Expert costs almost twice the cost of Nexxus Professional. Even so, Nessus Professional can be a pricey purchase, especially for smaller organizations with limited cybersecurity budgets. Also, organizations are required to commit to at least a one-year license, regardless of which version they purchase. Services like advanced support and on-demand training are add-ons that must be purchased separately. On the plus side, any organization can try a free version of Nessus Professional or Nessus Expert for seven days before making the final purchase decision.
Nessus Professional vs. Nessus Expert
Both Nessus Professional and Nessus Expert offer unlimited IT vulnerability assessments and other key features, such as access to an extensive plugin database, configurable reports, portability and community support. Nessus Expert offers a few additional features for organizations with more advanced needs.
The Professional version is recommended for security consultants, security practitioners and pen testers. The key features of Nessus Professional are as follows:
- It provides access to a library of more than 210,000 plugins that automatically update in real time and provide remediation actions to help security teams identify and remediate vulnerabilities.
- Custom audit files simplify verifications of the organization's configuration requirements and compliance standards.
- It provides coverage of more than 88,000 CVEs and visibility into more than 47,000 IT assets.
- Seamless integration with multiple commercial threat intelligence feeds generates useful insights into potential malware and ransomware that may be present in the IT environment.
- It comes with preconfigured templates for IT and mobile assets to quickly detect vulnerabilities.
- Its updated user interface simplifies navigation.
In addition, the Professional license can be transferred between computers or run on a Raspberry Pi for high portability and simplified use.
These benefits notwithstanding, Nessus Professional is not suitable for organizations that need to do the following:
- Scan their external attack surface.
- Add domains for web applications.
- Scan cloud infrastructure.
Nessus Expert fills in these gaps and provides greater breadth and depth of coverage into the enterprise attack surface. Expert includes everything in the Professional version and additional features to address risks outside of traditional IT assets. It does this by assessing all IaC repositories for vulnerabilities before they are pushed to production and by discovering internet-exposed IT assets, including cloud services.
Nessus Expert is designed to provide the following benefits:
- Greater visibility into the internet-facing attack surface.
- Discovery of unknown security issues that may be part of the software development lifecycle.
- Discovery of zero-day vulnerabilities for stronger, more proactive protection from emerging risks.
- A more proactive and reliable approach to vulnerability assessment for cloud workloads, newly discovered assets and assets outside the traditional security perimeter.
- Safe and fast vulnerability scanning with minimal disruptions or delays.
Nessus Expert is suitable for large organizations and small to medium-sized businesses that require a more expansive feature set. Furthermore, security consultants, pen testers and developers can benefit from the ease of use, portability and advanced features offered in Nessus Expert.
Want to know more about penetration testing? Check out this Pen testing guide: Types, steps, methodologies and frameworks.
More on Vulnerability Priority Rating capability in Nessus
Both versions of Nessus evaluate the severity of various threats using Tenable's VPR tool that facilitates predictive prioritization of vulnerabilities. VPR assigns a score to each finding based on its potential threat and technical impact to identify the vulnerabilities that pose the greatest risk to an organization's IT and internet-facing environments. The goal is to rate vulnerabilities most in need of immediate remediation.
Machine learning (ML) models are at the heart of Tenable predictive prioritize and VPR. These models are trained on historical data sourced from threat intelligence feeds, exploit repositories, exploit kits and vulnerability advisories. Such training allows the models to create accurate threat forecasts and pinpoint appropriate levels of near-term threats for each discovered vulnerability. The raw data is fed daily to the VPR pipeline and ML threat models are applied to it to generate a threat score for each vulnerability. This score is then combined with the CVSS framework to generate the vulnerability priority rating that security teams can then use for vulnerability prioritization and proactive remediation.
Want to know how Nessus stacks up against other vulnerability scanners? Compare the top vulnerability scanning tools for security teams.







