Layer Two Tunneling Protocol (L2TP)
What is Layer Two Tunneling Protocol (L2PT)?
Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by internet service providers (ISPs) to enable virtual private networks (VPNs). To ensure security and privacy, L2TP must rely on an encryption protocol to pass within the tunnel.
L2TP can transfer most L2 data types over an IP or Layer Three (L3) network. The process initiates a tunnel between an L2TP access concentrator (LAC) and an L2TP network server (LNS) on the internet. This facilitates a Point-to-Point Protocol (PPP) link layer that is encapsulated and transferred across the internet.
The end user initiates a PPP connection to an ISP through either an Integrated Services Digital Network (ISDN) or public switched telephone network service.
L2TP merges the best features of two other tunneling protocols:
L2TP is composed of two core components:
- LAC -- the device that physically terminates the call; and
- LNS -- the device that terminates and can authenticate the PPP stream.
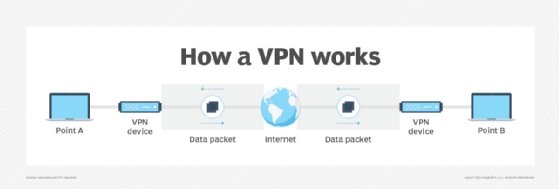
L2TP is not well known. Early versions were limited to carrying PPP. However, this limitation no longer exists. PPP defines a means of encapsulation to transmit multiprotocol packets over L2 point-to-point links.
In this scenario, the user connects to the network access server (NAS) through ISDN, Asymmetric Digital Subscriber Line, Plain Old Telephone Service or other services, and PPP runs over that connection. In this configuration, the L2 and PPP session endpoints are both on the same NAS.
What is L2TP used for?
L2TP uses packet-switched network connections to enable endpoints to reside in different machines.
The user has an L2 connection to a LAC, which tunnels individual PPP frames to the NAS. As a result, packets can be processed separately from the location of the circuit termination.
If the circuit concentrator is local, long-distance charges are eliminated. Additional benefits are reliability, stability, compatibility, configurability and protection from man-in-the-middle attacks.
L2TP also supports various authentication options carried by PPP. This includes Password Authentication Protocol, Microsoft Challenge-Handshake Authentication Protocol and CHAP. An additional way to authenticate the endpoints of a tunnel is to use L2TP to provide extra security implemented with IP Security (IPsec).
L2TP also has some drawbacks. These include transmission failure due to mismatched security keys, limited port support and slower speeds.
How does L2TP differ from PPTP?
There are several differences between L2TP and PPTP.
For example, L2TP can use a variety of tunnel media, whereas PPTP can only tunnel over IP networks.
L2TP also supports several tunnels between two endpoints, each having its own quality of service. PPTP supports one tunnel between two endpoints.
Compressed L2TP headers are 4 bytes, and compressed PPTP headers are 6 bytes.
What are the Layer 2 protocols?
There are several L2 communications protocols used by L2 devices, such as multiport bridges and network interface cards, to carry data between nodes in a local area network (LAN) or across a wide area network.
Other data link L2 protocols besides L2TP include the following:
- Attached Resource Computer Network;
- Asynchronous Transfer Mode;
- Ethernet;
- Ethernet Automatic Protection Switching;
- Fiber Distributed Data Interface;
- High-Level Data Link Control;
- IEEE 802.2 -- provides logical link control functions to Institute of Electrical and Electronics Engineers (IEEE) 802 media access control layers;
- IEEE 802.11 wireless LAN;
- Multiprotocol Label Switching;
- Spanning Tree Protocol;
- Token Ring; and
- Unidirectional Link Detection.
Other Layer Two Tunneling Protocol features
Additional frequently asked L2TP-related questions include the following.
What is L2TP passthrough?
L2TP passthrough is an L2 tunneling protocol used for point-to-point sessions via the internet on L2.
What is TCP tunneling?
TCP tunneling helps aggregate and transfer packets sent between a single TCP connection and the end hosts. The TCP tunnel improves fairness among aggregated flows and enables the transparent transmission of several protocols through a firewall.
What is L2TP over IPsec?
L2TP over IPsec combines technologies like the L2 transfer protocol and IPsec. It works like a VPN, where IPsec helps create a secure channel that encapsulates L2TP traffic.
What is an L2TP secret?
An L2TP secret or VPN secret is a unique password used in place of a regular password to access the VPN. PPTP connections to the VPN must use an L2TP secret.








