What is ICMP (Internet Control Message Protocol)?
ICMP (Internet Control Message Protocol) is a network layer error-reporting protocol that's used to communicate data transmission problems. Network devices, such as routers, use ICMP to generate error messages to the source Internet Protocol address when network problems prevent the delivery of IP packets. ICMP creates and sends messages to the source IP address indicating that a gateway to the internet, such as a router, service or host, can't be reached for packet delivery. Any IP network device can send, receive or process ICMP messages.
ICMP is not a transport protocol that sends data between systems.
While ICMP isn't used regularly in end-user applications, network administrators use it to troubleshoot internet connections in diagnostic utilities, including traceroute and ping.
What is ICMP used for?
ICMP is a network layer protocol that routers, intermediary devices and hosts use to communicate error information or updates to other routers, intermediary devices and hosts.
ICMP messages are sent in several scenarios. For example, if one device sends a message that's too large for the recipient to process, the recipient drops that message and sends an ICMP message back to the source. Another example is when the network gateway finds a shorter route for the message to travel. When this happens, an ICMP message is sent, and the packet is redirected to the shorter route.
ICMP is also used for network diagnostics, specifically the traceroute and ping terminal utilities, in the following ways:
- Traceroute. The traceroute utility is used to display the physical routing path between two internet devices communicating with each other. It maps out the journey from one router to another -- sometimes called a hop -- and provides information on how long it took for data to get from source to destination. Using traceroute to diagnose network problems can help administrators locate the source of a network delay.
- Ping. The ping utility is a simpler traceroute. It sends out pings -- also referred to as ICMP echo request messages -- and then measures the amount of time it takes the message to reach its destination and return to the source host. These replies are called echo reply messages. Ping commands are useful for gathering latency information about a specific device. Unlike traceroute, ping doesn't provide picture maps of the routing layout.
ICMP can also be misused in ways that negatively affect network performance. For example, the ping utility is often exploited for certain denial of service (DoS) attacks, where an attacker targets a server by overwhelming it with a flood of pings or ICMP packets. This excessive traffic can lead to server unresponsiveness and disrupt normal operations.
The widely used IP version 4 (IPv4) address class and the newer IPv6 use similar versions of the ICMP protocol -- ICMPv4 and ICMPv6, respectively.
How does ICMP work?
ICMP is one of the main protocols of the TCP/IP suite. However, ICMP isn't associated with any transport layer protocol, such as Transmission Control Protocol (TCP) or User Datagram Protocol. It's a connectionless protocol, meaning a device doesn't need to open a connection with the target device before sending a message. This contrasts with TCP, for example, where a connection must be established before a message can be sent, establishing that both devices are ready through a TCP handshake.
ICMP messages are transmitted as datagrams and consist of an IP header that encapsulates the ICMP data. Similar to a packet, a datagram is a self-contained independent entity of data. Think of it as a package carrying a piece of a bigger message across the network. ICMP packets are IP packets with ICMP in the IP data portion. ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed.
The following shows, step by step, how ICMP works:
- A network device, such as a router or host, detects an issue or wants to communicate the network status due to packet loss, routing problems or unreachable destinations.
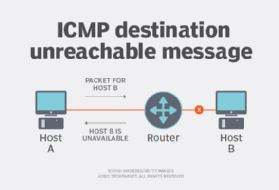
- The network device creates an ICMP message describing the nature of the problem, such as "Destination Unreachable" or "Time Exceeded."
- The message is then encapsulated within an IP packet. This encapsulated IP packet contains the ICMP message, error codes and the portion of the original data packet's header that caused the issue in order to help with problem diagnosis.
- The IP packet containing the ICMP message is delivered to the source IP address of the original packet. This enables the sender to receive feedback about the status of its transmission.
- Upon receiving the ICMP message, the original sender takes appropriate action based on the information provided. For example, if the sender receives the Destination Unreachable message, they can then choose to retry the transmission or redirect the data to a different destination.
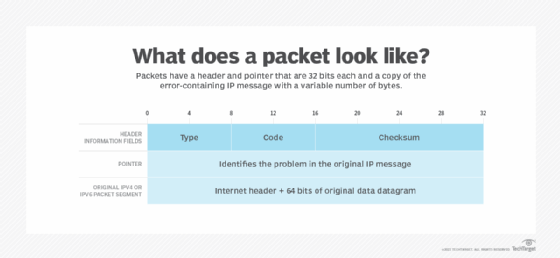
The ICMP header appears after the IPv4 or IPv6 packet header and is identified as IP protocol number 1. The protocol contains three parameters, followed by the ICMP data and the original IP header, which together identify the failed packet.

ICMP parameters
ICMP parameters exist in the packet header and identify the errors in the packet to which they pertain. The parameters are similar to a shipping label on a package. They provide identifying information about the packet and the data it contains. That way, the protocols and network tools receiving the ICMP message know how to handle the packet.
The first 32 bits of every ICMP message's packet header contain three informational fields. Those parameters are type, code and checksum:
- Type. The first 8 bits are the message types. Some common message types are the following:
- Type 0 -- Echo Reply.
- Type 3 -- Destination Unreachable.
- Type 5 -- Redirect.
- Type 8 -- Echo.
The type provides a brief explanation of what the message is for so the receiving network device knows why it's getting the message and how to treat it. For example, a Type 8 Echo is a query a host sends to see if a potential destination host or system is available. Upon receiving an Echo message, the receiving device might send back a Type 0 Echo Reply message, indicating it's available. The Internet Assigned Numbers Authority, a nonprofit standards organization, provides a list of all message types ICMP packets use.
- Code. The next 8 bits represent the message type code, which provides additional information about the error type.
- Checksum. The last 16 bits provide a message integrity check. The checksum shows the number of bits in the entire message and enables the ICMP tool to check for consistency with the ICMP message header to ensure the full range of data was delivered.
The next part of the ICMP header is the pointer. It consists of 32 bits of data that point out the problem in the original IP message. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. The receiving device looks at this part of the header to pinpoint the problem.
The final section of the ICMP packet is the original datagram. It consists of up to 576 bytes in IPv4 and 1,280 bytes in IPv6 and includes a copy of the original error-containing IP message.
ICMP in DDoS attacks
ICMP lacks authentication mechanisms and can be used by attackers for carrying out DoS and distributed DoS attacks. In DDoS attacks, attackers overwhelm the target with unwanted traffic so the target can't provide service to its users.
There are multiple ways an attacker can use ICMP to execute these attacks, including the following:
- Ping of death. The attacker sends an IP packet larger than the number of bytes allowed by IP. On the way to its intended destination, the oversized packet is fragmented. However, when the recipient device reassembles it, the size exceeds the limit, causing a buffer overflow and the receiving machine to freeze or crash. Newer devices have defenses against this older attack, but legacy networking devices are still vulnerable to it.
- ICMP flood attack. Sometimes called a ping flood attack, the goal of this attack is to overwhelm the target device with echo request packets. Each echo request packet must be processed by the target and responded to with Echo Reply messages. This sucks up all the target computer's resources, causing DoS to any other users of the target computer.
- Smurf attack. In a Smurf attack, the attacker sends an ICMP packet with a spoofed source IP address, and the network layer equipment replies to the packet, sending the spoofed address a flood of packets. Similar to the ping of death, Smurf attacks are more likely to work on undefended legacy equipment.
- ICMP tunneling. ICMP tunneling is a command-and-control attack technique in which attackers encapsulate and conceal malicious traffic within seemingly benign ICMP headers, making it bypass firewalls and network security measures.
- ICMP router advertising spoofing. During this attack, an attacker sends false ICMP router advertisement messages to a network, misleading devices into using the attacker's machine as their default gateway. This can lead to man-in-the-middle attacks, where the attacker intercepts and potentially alters communications between network devices.
Advantages and disadvantages of ICMP
ICMP serves essential functions in network management and comes with advantages and a few disadvantages as well.
Advantages of ICMP
- Provides network diagnostics. Network monitoring tools, such as traceroute and ping, rely on ICMP to help network admins diagnose connectivity issues and measure round-trip times. This functionality is vital for maintaining network performance and troubleshooting routing issues.
- Offers error reporting. ICMP offers status updates and error reporting, which can include timeouts, unreachable destinations and fragmentation issues. For example, these updates and reporting can be used to alert senders when packets can't be delivered due to various network problems or when a packet's time to live expires.
- Requires low overhead. ICMP messages are typically short and simple and require low overhead and limited bandwidth to be delivered.
- Optimizes network management. By enabling devices to communicate status and error messages, ICMP helps with troubleshooting and optimizing network performance and management.
Disadvantages of ICMP
- Introduces security vulnerabilities. ICMP is a potential vector for various security attacks, such as ping floods, Smurf attacks and tunneling, where attackers use ICMP to overwhelm a target with traffic or use it to bypass security measures.
- Limits data transfer. ICMP isn't designed for large-scale data transfers. It only handles control and error messages, which means it can't be used for transmitting user data or applications.
- Hinders monitoring. Disabling ICMP can hinder network monitoring and diagnostics. Many monitoring tools depend on ICMP to check the availability of devices and blocking it can lower the visibility into the health of a network.
- Limits control. ICMP doesn't provide mechanisms for controlling traffic flow or ensuring delivery, which can lead to challenges in managing network performance.
ICMP FAQs
The following are some commonly asked questions about ICMP.
What are some common uses of ICMP?
ICMP is commonly used for error reporting and network diagnostics. It provides error reporting by informing the sender about issues in data transmission. For network diagnostics, monitoring tools, such as traceroute and ping, use ICMP to check connectivity and measure round-trip times.
Are ICMP and ping the same?
No, ICMP and ping aren't the same, but they're closely related. ICMP is the protocol that facilitates network communications, including error reporting and diagnostics, while ping is a tool that uses ICMP to assess network connectivity and performance.
Can ICMP be blocked?
Yes, many organizations choose to block ICMP traffic to mitigate security risks. However, this can prevent network diagnostics and monitoring, as many tools rely on ICMP for functionality.
Is ICMP a connection-oriented protocol?
No, ICMP is a connectionless protocol. It doesn't require an established connection before sending messages, which enables quicker communication of error messages and diagnostics.
Explore how network administrators divide networks into smaller segments, known as subnets, to enhance control and efficiency. Discover the process of creating subnets in both IPv4 and IPv6 networks.







