What are the pros and cons of machine learning in network security?
The predictive nature of machine learning can benefit network security strategies. But it can also benefit those looking to break through secure network barriers.
Machine learning has become a valuable component of network security products, but the technology is a mixed blessing. Unfortunately, hackers can also employ machine learning.
Machine learning in network security separates legitimate network and application operations from attacks by building a set of rules that characterizes both activities. Meanwhile, attackers can use machine learning to probe network defenses, identify ways to evade rules and carry out successful attacks.
Pros and cons of machine learning in network security
One advantage of machine learning in network security is that it can identify a zero-day attack. It takes time to identify and analyze a new signature-based attack, but machine learning can apply rules that differentiate legitimate operations from attacks. A new form of malware can be detected based on its actions, so previous observation and analysis are unnecessary.
Organizations can prepare machine learning software for operation in several ways. The software can be presented with a set of inputs labeled as attacks and other inputs labeled as legitimate. The software can then learn by analyzing a set of characteristics that differentiate between the attacks and the legitimate activity.
Spam filtering is a simple example. With spam filtering, admins create a list of words that typically show up in spam. Another approach is to supply a set of emails with some identified as spam and some as legitimate. The software can then develop a set of rules based on words that showed up in each email category. As it operates, the software continues to extend its rules based on other words and email addresses often associated with spam.
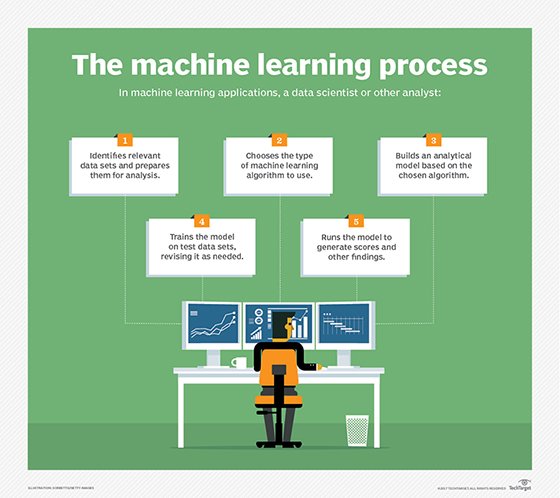
Machine learning software can also build a set of rules based on observed network and application operations. For example, the software can monitor a transaction-based application and recognize how it accesses a critical database. Actions that do not follow the same pattern, such as multiple attempts to access a database, would be blocked.
Unfortunately, academic and corporate research on techniques for machine learning in network security cannot be hidden from attackers. Attackers have begun to use the technology to repetitively probe network defenses to determine the rules that antimalware software uses to identify attacks.
Typically, attackers gain value from a successful attack, so they will undoubtedly continue to develop ways to deceive defenses. As they do, researchers will need to continually improve defenses.







