token ring
What is a token ring?
A token ring is a data link for a local area network (LAN) in which all devices are connected in a ring or star topology and pass one or more tokens from host to host. A token is a frame of data transmitted between network points. Only a host that holds a token can send data, and tokens are released when receipt of the data is confirmed. IBM developed token ring technology in the 1980s as an alternative to Ethernet.
What is a token ring network?
Also known as IEEE (Institute of Electrical and Electronics Engineers) 802.5, a token ring network connects all devices, including computers, in a circular or closed-loop manner. In this scenario, the word token describes a segment of data sent through the network.
Token ring networks prevent data packets from colliding on a network segment because only a token holder can send data, and the number of tokens available is also controlled. When a device on the network successfully decodes that token, it receives the encoded data.
Token ring history
Attached Resource Computer Network, Fiber Distributed Data Interface (FDDI) and the token bus used the token ring. But the most broadly deployed token ring protocols were those of IBM, released in the mid-1980s, and the standardized version of it known as IEEE 802.5, which appeared in the late 1980s.
The use of token rings and 802.5 started declining in the 1990s. Today, they are considered inactive and obsolete. Enterprise organizations gradually phased out the token ring and adopted Ethernet technology, which dominates LAN designs today. The IEEE 802.5 working group is now listed as disbanded.
Token rings were popular because they worked well with large amounts of traffic, but they were not well suited to large networks, particularly if those networks were spread widely or had physically remote nodes. To overcome some of these limitations, multistation access units (MSAUs), which are like hubs on Ethernet, were added. MSAUs are centralized wiring hubs and are also known as concentrators.
What is token ring star topology?
In a star topology, token ring access could connect up to 225 nodes at 4 million, 16 million or 100 million bits per second, conforming to the IEEE 802.5 standard. An MSAU connects all stations using a twisted pair cable. For example, users could connect six nodes to an MSAU in one office and connect that MSAU to an MSAU in another office that served eight other nodes. In turn, that MSAU could connect to another MSAU that connected to the first MSAU.
Such a physical configuration is called a star topology. However, the actual configuration is a ring topology because every message passes through every computer, one at a time, until it forms a ring.
An advantage of an MSAU is that, if one computer fails in the ring, the MSAU can bypass it, and the ring will remain intact. Typically, each node connection cannot exceed 382 feet, depending on the cable type. However, you can increase this distance by up to a mile and a half using token ring repeaters.
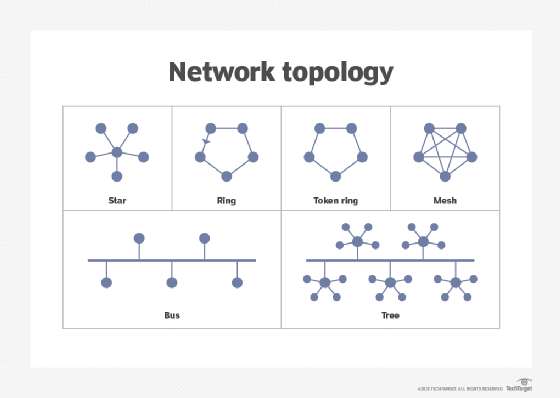
What are Type 1 and Type 3 token ring networks?
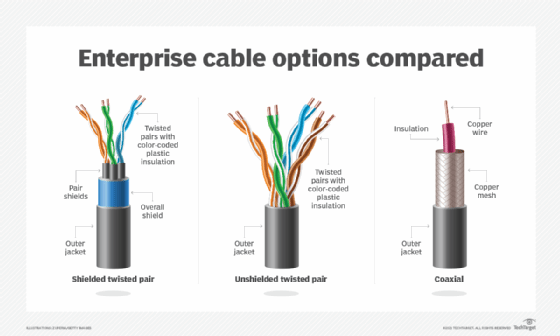
Token ring networks are generally considered either Type 1 or Type 3 configurations. Type 1 networks can support up to 255 stations per network ring and use shielded twisted pair wires with IBM-style Type 1 connectors.
Type 3 networks can support up to 72 stations per network and use unshielded twisted pair wires with Cat3, Cat4 or Cat5 with RJ-45 connectors. Like Ethernet, the token ring functions at Layers 1 and 2 of the Open Systems Interconnection (OSI) model.
What is a full-duplex token ring?
In a dedicated token ring, also called full-duplex token ring, switching hubs enable stations to send and receive data simultaneously on the network. In this case, a token ring switching hub divides the network into smaller segments. When a data packet is transmitted, the token ring switch reads the packet's destination address and forwards the information directly to the receiving station.
The switch establishes a dedicated connection between the two stations. This enables data to be transmitted and received simultaneously. But, in a full-duplex token ring, the token-passing protocol is suspended, making the network a "tokenless" token ring. Full-duplex token rings are designed to improve network performance by increasing the sending and receiving bandwidth for connected stations.
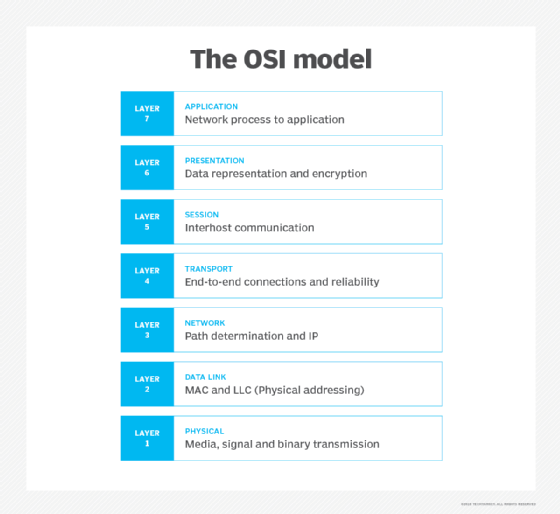
How does token ring compare to Ethernet?
Devices within a token ring network can share the same media access control address without conflict. This is not possible within an Ethernet network. Administrators can also ensure that specific nodes take priority over others by configuring token ring networks in ways not permitted with unswitched Ethernet.
The token ring topology was once widely used on LANs in the 1980s and 1990s. However, it was almost entirely displaced by Ethernet, due to Ethernet's lower cost. At the time, cabling for token ring networks cost much more than Ethernet Cat3/Cat5e cables. Token ring network cards and ports were also expensive.
After the development of Ethernet switching and full-duplex links, Ethernet overtook token ring technology as it minimized the practical concern of collisions.
Carrier Sense Multiple Access with Collision Detection (CSMA/CD), specified in the IEEE 802.3 standard, is the protocol for carrier transmission access in Ethernet networks. On Ethernet, any device can try to send a frame at any time. Each device senses whether the line is idle and, therefore, available for use. If it is available, the device begins to transmit its first frame. If another device tries to send data simultaneously, a collision is said to occur, with frames being discarded. CSMA/CD was designed to prevent such collisions.
The token ring, specified in the IEEE 802.5 standard, is the original token-passing (access method) standard for twisted pair shielded copper cables. Support for copper and fiber cabling enabled capacity to rise from 4 megabits per second to 100 Mbps. It's sometimes called IBM Token-Ring.
What is token passing?
The token ring topology uses an access method called token passing. For any station on the ring to transmit, it must first possess a token. Sent as a unit complete with address and necessary protocol control information, it consists of three fields circulating on the ring until a station captures and removes it.
The first field in the token frame is called the starting delimiter and contains a pattern of bits indicating the start of the frame.
The second field is the access control field. The bits within this field control the priority of the bits awaiting transmission. Stations are given priority for every token on a scale from 0 to 7. When the frame passes what is known as the active monitor, the bit is set to 1 and is used to detect a continuously circulating frame on the ring.
Every station in a token ring network is either an active monitor or a standby monitor. There can be only one active monitor on a ring at a time. The active monitor performs several ring administration functions. For example, it operates as the master clock for the ring to provide synchronization of the signal. It inserts a 24-bit delay into the ring to ensure sufficient buffering.
Furthermore, it also makes sure that one token circulates whenever there is no frame transmission. It also detects a broken ring and removes circulating frames from the ring. The third field in the token frame is the ending delimiter.
What is FDDI?
FDDI is a set of American National Standards Institute and International Organization for Standardization standards for data transmission on fiber optic lines. The basis for FDDI protocols is the token ring protocol. You can extend its range up to 200 kilometers or 124 miles.
In addition to being geographically extensive, an FDDI LAN can support thousands of users. As such, FDDI often forms the backbone for a wide area network.
What is a token bus?
As defined above, the token ring is an IEEE 802.5 standard and is passed over a physical token ring network and not a virtual ring. The token bus network standard passes tokens along a virtual ring.
The virtual ring is made up of stations that pass tokens during a sequence in a virtual ring. Each node or station in a token bus network knows both the predecessor station's and successor station's addresses. In this scenario, a node transmits the data only if it has a token. Although it is a virtual ring, its working rule is analogous.
Token ring pluses and minuses
There are advantages and disadvantages of token rings.
Advantages of token rings
- Token rings reduce the chances of data collision.
- Token passing performs better than bus topology under heavy traffic.
- A server is not needed to control connectivity among the nodes.
Disadvantages of token rings
- Data packets must pass through all the nodes, slowing routing.
- Token ring networks have suffered from network management problems and poor network fault tolerance.
- Token ring is considered obsolete, with the dominance of Ethernet and the IEEE working group having been disbanded.







