carloscastilla - Fotolia
What does a VPN concentrator do?
As more employees work remotely and VPN use rises, VPN concentrators have become trendy. But what does a VPN concentrator do exactly, and how do you deploy one?
Virtual private networks are encrypted tunnels that protect network communications from unauthorized access when the communications must cross untrusted networks, like the internet. VPN concentrators are one component that can enhance VPN connections and remote access. But what does a VPN concentrator do, and what type does your organization need?
VPN concentrators are used to connect many remote networks and clients to a central corporate network. They are used to protect the communications between remote branches or remote clients -- such as workstations, tablets, phones and IoT devices -- to corporate networks. You can think of it as extending the corporate network's security boundary out to remote branches or remote computers.
VPN clients, VPN routers and VPN concentrators at each end of the connection perform key negotiation, authentication, encryption and decryption. Encryption has two modes. The first, called transport mode, encrypts only the data payload, leaving the original packet headers intact. The second method, called tunnel mode, encrypts the entire packet and encapsulates it in a new IP datagram. Therefore, your VPN security design must start with understanding the transport vs. tunnel modes.
VPN concentrator benefits and costs
VPN concentrators are deployed at the corporate network edge, either just inside the border firewall using a single interface or in parallel with the firewall configured in passthrough mode with an inside and outside interface. Your design details, including network address translation and vendor recommendations, will provide direction in selecting the preferred topology.
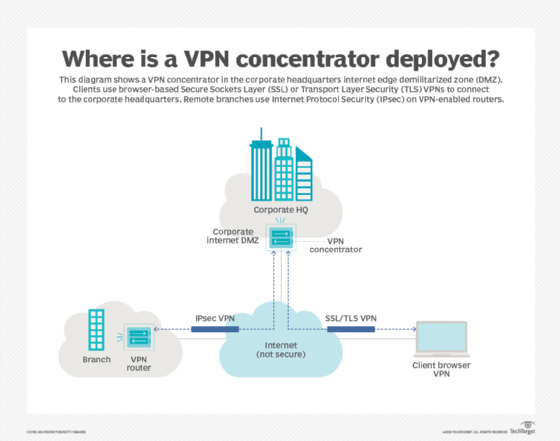
You should include a VPN if your organization needs to protect communications between sites or with remote users. Dedicated VPN concentrators become more attractive as the number of VPN connections increases or the aggregate bandwidth grows.
Vendors offer VPN concentrators at a variety of price-performance points. Smaller models may be software-based VMs or container implementations, while the larger models with dedicated encryption hardware can support thousands of VPN tunnels. Your design should incorporate other requirements, like redundancy and load balancing, which will determine how many concentrators are needed, their capacity and their feature sets.
Types of VPN concentrators
Most VPN concentrators are based on a dedicated hardware appliance that is sized for a specified number of VPN connections. You can also find appliances that include dedicated hardware for performing encryption and decryption of large numbers of VPN tunnels.
Configurating large numbers of site-to-site IPsec VPNs is tedious and complex but is simplified by using dynamic multipoint VPN (DMVPN), a mechanism pioneered by Cisco. Cloud deployments are supported by software-only VPN concentrators that run within VM or container environments.
Organizations with especially tight budgets, multiple remote offices and a motivated staff can take advantage of an open source project to assemble their own VPN concentrator. Some examples include OpenVPN, pfSense, native Linux implementations and VyOS, which includes DMVPN support.
Which VPN protocol is best?
Two primary protocols are used for VPNs: IPsec and Secure Sockets Layer/Transport Layer Security (SSL/TLS). Secure Shell (SSH) tunneling is also used -- but rarely. IPsec relies on an OS extension to create the VPN tunnel. It is the preferred mechanism to connect networks between branches and corporate networks.
SSL/TLS is incorporated into the web browser, providing wider availability across more devices than IPsec. It is often preferred for connecting a single host to a corporate network.
You should understand the protocol differences and the speed, security risks and technology when choosing among protocols. Avoid the security mistake of using split tunneling unless additional protection measures are taken.
Maintaining good security
A good network security system is constructed from many components -- and VPNs are just one component in the overall system. With the prevalence of malware and data loss, such as credit card theft or intellectual property disclosure, you should consider a periodic review of your organization's security systems. New security threats emerge on a regular basis, and only good diligence protects your critical assets.
When was the last time you had a security assessment?








