What is an intrusion detection system (IDS)?
An intrusion detection system monitors (IDS) network traffic for suspicious activity and sends alerts when such activity is discovered. Anomaly detection and reporting are the primary functions of an IDS, but some systems also take action when malicious activity or anomalous traffic is detected. Such actions include blocking traffic sent from suspicious Internet Protocol addresses.
An IDS can be contrasted with an intrusion prevention system (IPS), which also monitors network packets for potentially damaging network traffic, much like an IDS. However, an IPS has the primary goal of preventing threats once detected instead of primarily detecting and recording threats.
How IDS works
IDSes are used to detect anomalies with the aim of catching hackers before they do damage to a network. Intrusion detection systems can be either network- or host-based. The system looks for the signatures of known attacks as well as deviations from normal activity. Deviations or anomalies are pushed up the stack as well as examined at the protocol and application layers. IDSes effectively detect events such as Christmas tree scans and Domain Name System poisonings.
A host-based IDS is installed as a software application on the client computer. A network-based IDS resides on the network as a network security appliance. Cloud-based intrusion detection systems are also available to protect data and systems in cloud deployments.
Different types of intrusion detection systems
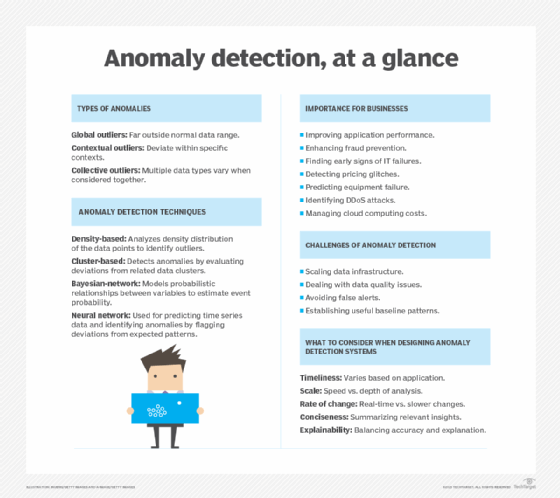
Various types of IDSes are available that use different methods to detect suspicious activities:
- Network-based intrusion detection systems. A NIDS is deployed at a strategic point or points within the network. It monitors inbound and outbound traffic to and from all the devices on the network.
- Host-based intrusion detection systems. A HIDS runs on all computers or devices in a network that have direct access to both the internet and the enterprise's internal network. In some cases, these systems are better able to detect anomalies than a NIDS. They can detect anomalous network packets and other malicious packets that originate from inside the organization or malicious traffic that a NIDS might fail to detect. A HIDS might also identify malicious traffic that originates from the host itself, for example when the host has been infected with any form of malware that could spread to other systems.
- Signature-based intrusion detection systems. A SIDS monitors all packets traversing the network and compares them against a database of attack signatures or attributes of known malicious threats, much like antivirus software.
- Anomaly-based intrusion detection systems. Anomaly-based IDS monitors network traffic and compares it with an established baseline to determine what's considered normal for the network with respect to bandwidth, protocols, ports and other devices. This type of IDS often uses machine learning to establish a baseline and accompanying security policy. It then alerts IT teams to suspicious activity and policy violations. By detecting threats using a broad model instead of specific signatures and attributes, the anomaly-based detection method improves the limitations of signature-based detection methods, especially when identifying novel security threats.
Historically, intrusion detection systems were categorized as passive or active. A passive IDS that detected malicious activity would generate alert or log entries but would not act. An active IDS, sometimes called an intrusion detection and prevention system, would generate alerts and log entries but could also be configured to take actions, such as blocking IP addresses and shutting down access to restricted resources.
Snort is one of the most widely used IDSes. It's an open source, free, lightweight NIDS that's used to detect emerging threats. Snort can be compiled on most Unix or Linux operating systems (OSes), with a version available for Windows as well.
Capabilities of intrusion detection systems
Intrusion detection systems monitor network traffic to detect when an attack is being carried out and identify any unauthorized access. They do this by providing some or all of the following functions to security professionals:
- Monitoring the operation of routers, firewalls, key management servers and files that other security controls aimed at detecting, preventing or recovering from cyberattacks need.
- Providing administrators a way to tune, organize and understand relevant OS audit trails and other logs that are otherwise difficult to track or parse.
- Providing a user-friendly interface so nonexpert staff members can assist with managing system security.
- Including an extensive attack signature database against which information from the system can be matched.
- Recognizing and reporting when the IDS detects that system files have been altered.
- Generating an alarm and notifying that security has been breached.
- Reacting to intruders by blocking them or blocking the server.
Benefits of intrusion detection systems
IDSes offer organizations several benefits, starting with the ability to identify security incidents. An IDS can analyze the quantity and types of attacks. Organizations use this information to change their security systems and implement more effective controls. In addition, an IDS can help companies identify bugs and problems with their network device configurations. IDS metrics are also used to assess future risks.
These types of threat detection systems assist with regulatory compliance. An IDS provides greater visibility across an organization's networks, making it easier to meet security regulations. Additionally, businesses can use IDS logs as part of the documentation to show they're meeting certain compliance requirements.
IDSes can also improve incident responses. System sensors can detect network hosts and devices. They can also be used to inspect data within network packets as well as identify the OSes of services being used. Using an IDS to collect this information can be much more efficient than manual censuses of connected systems.
Challenges of intrusion detection systems
IDSes are prone to false alarms or false positives. Consequently, organizations must fine-tune their intrusion detection products when they first install them. This includes properly configuring them to recognize what normal traffic on their network looks like compared with potentially malicious activity.
However, despite the inefficiencies they cause, false positives don't usually result in serious damage to the network. They can lead to configuration improvements.
A much more serious IDS issue is a false negative, which is when the IDS misses a threat or mistakes it for legitimate traffic. In a false negative scenario, IT teams have no indication that an attack is taking place and often don't discover it until after the network has been affected in some way. It's better for an IDS to be oversensitive to abnormal behaviors and generate false positives than to be under sensitive and generating false negatives.
False negatives are becoming a bigger issue for IDSes, especially signature-based IDSes, since malware is evolving and becoming more sophisticated. It's hard to detect a suspected intrusion because new malware might not display the previously detected patterns of suspicious behavior that IDSes are designed to detect. As a result, there's an increasing need for IDSes to detect new behavior and proactively identify novel threats and their evasion techniques.
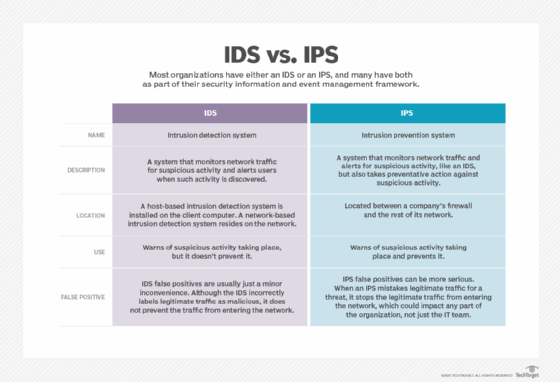
IDS versus IPS
An IPS is similar to an intrusion detection system but differs in that an IPS can be configured to block potential threats. Like intrusion detection systems, IPSes are used to monitor, log and report activities, but they can also be configured to stop advanced threats without the involvement of a system administrator. An IDS typically simply warns of suspicious activity taking place but doesn't prevent it.
An IPS is located between a company's firewall and the rest of its network. It may have the ability to stop any suspected traffic from getting to the rest of the network. These systems execute responses to active attacks in real time and can actively catch intruders that firewalls or antivirus software miss.
However, organizations must be careful with IPSes, because they're prone to false positives. An IPS false positive is likely to be more serious than an IDS false positive because the IPS prevents the legitimate traffic from getting through, whereas the IDS simply flags it as potentially malicious.
It has become a necessity for most organizations to have either an IDS or an IPS -- usually both -- as part of their security information and event management security information and event management framework.
Several vendors integrate an IDS and an IPS capabilities into one product known as unified threat management. UTM lets organizations implement both simultaneously alongside next-generation firewalls in their security infrastructure.
IDS best practices
A range of best practices exist to ensure effective IDS systems and protection against new threats, including the following:
- Establish benchmarks. Identifying what constitutes normal network activity and traffic as well as establishing benchmarks helps network administrators determine what abnormal behavior is and protect against it.
- Update systems. All systems should have the latest updates as cybersecurity measures continuously improve and standards change over time. This is part of system optimization.
- Fine-tune network access. An organization should determine an acceptable amount of network traffic and put controls on it. This approach helps identify cyberthreats; an amount traffic that's too high can lead to undetected threats.
- Enforce adequate security measures. A comprehensive security strategy can help reduce vulnerabilities. It should include user authentication technology, protect communications with encryption and take intranetwork threats, such as phishing, into consideration.
- Be attentive to configuration settings. Organizations must have their network configuration settings fine-tuned to always suit their needs. This should be verified before any upgrades are carried out.
Security threats take many different forms. Learn about the various types of incidents and how to prevent them.






