Comparing mobile operating systems' manageability and security
Each of the popular mobile operating systems has different security and management features. Compare them to see which ones might fit in your company.
Today, few employers can insist that employees use just one kind of smartphone, but comparing the manageability and security of today's top mobile operating systems is useful for establishing platform preferences and acceptance criteria.
In some ways, the popular mobile operating systems are very similar. They all support some kind of mobile device management (MDM), but the way each OS supports MDM is different. Some have device-native capabilities and others require third-party MDM agents. The same can be said for security settings: All four of the mobile OSes have password, encryption and access control options, but those options differ from one OS to another.
Whether a certain OS will work for you depends on what you want it to do. But knowing what you're getting from each OS can make supporting them easier.
Decide what to compare
The first step is to establish scope: Which mobile operating systems should you compare? According to IDC's December 2012 global market share report, Google's Android OS leads the smartphone market with 68%, followed by Apple's iOS at 19%, Research In Motion's (RIM's) BlackBerry OS with 5%, and Microsoft's Windows Phone with 3%. Furthermore, IDC expects these four OSes to represent 98% of the market through 2016, with just one spike -- a 10% increase in Windows Phone sales as Microsoft original equipment manufacturers (OEMs) get back into the race.
More on mobile operating systems
Comparing mobile OSes' application environments
Why mobile OS fragmentation is a problem
Consumer mobile operating system features: An IT guide
As a result, almost every smartphone or tablet that members of your workforce use is likely to run a version of one of these four OSes, although you never know when the next game-changer will arrive. Unless your company has unusual needs, you can put niche OSes such as Symbian and Linux/Bada out of scope, and focus on managing and securing Android, iOS, Windows Phone and BlackBerry devices.
Assess MDM fit
Smartphone and tablet manageability depend on the capabilities of the mobile OS and its ability to interface with your MDM platform. Today, there are three common approaches to over-the-air MDM.
- Single-OS MDM: This historically popular approach was championed by RIM's BlackBerry Enterprise Server (BES). RIM and Microsoft still offer single-OS management, which gives IT administrators deeper control and visibility, but requires that IT pros understand and adapt to each mobile operating system.
- Multi-OS MDM: This approach was boosted by Apple's iPhone but has since become readily available for recent versions of all four mobile OSes. Multi-OS managers deliver a unified, "single-pane-of-glass" experience, but are constantly scrambling to hide underlying differences and support new devices and versions.
- Exchange ActiveSync (EAS)-based management: This "MDM lite" approach is a common way to obtain unified, but limited, control over different kinds of mobile devices. Microsoft's broadly-licensed mailbox sync protocol lets admins get and set related device features and security policies, such as requiring passcodes or remotely wiping lost devices.
The following table summarizes the extent to which each of the most popular mobile operating systems and versions supports these management approaches, as of January 2013.
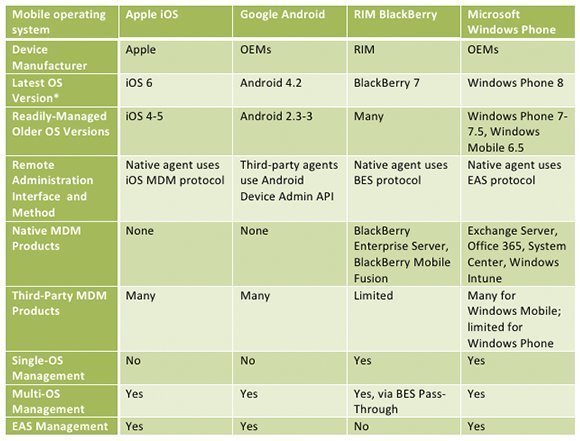
If EAS meets your management needs, then all contemporary devices except BlackBerry can connect to your enterprise mail server. For deeper visibility and control over all devices, go with multi-OS MDM from vendors such as AirWatch, Fiberlink, Microsoft, Mobile Iron, RIM and Zenprise. For BlackBerry management, you'll need BES, either alone or with a multi-OS MDM product.
Your degree of visibility and control of devices depends on your management approach, device make/model and mobile operating system version. The BlackBerry OS supports the richest set of remotely manageable policies, followed by Windows Mobile 6.5. Apple iOS has more than 150 MDM-configurable policies, but Android 4 and Windows Phone 7 support significantly fewer policies. Windows Phone 8 and Windows RT offer greater manageability with Microsoft System Center and Windows Intune, but third-party MDM support is still emerging for these latest OSes.
Drill into security capabilities
Mobile security capabilities can be a critical factor in determining enterprise suitability. Ultimately, security depends on device make and model and the mobile operating system and version. For example, a mobile operating system may allow full-device encryption, but individual smartphones and tablets running that OS are not all capable of performing that encryption. Nonetheless, it can be helpful to compare the security posture of mobile operating systems:
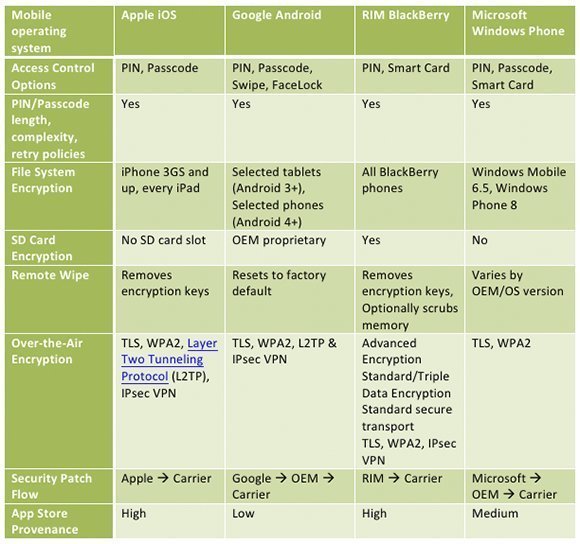
As you can see, the top four mobile OSes are largely the same when it comes to numeric PIN or alphanumeric passcode support. Organizations that require smart card authentication have fewer choices.
Similarly, the latest versions of all four mobile operating systems support encrypted file systems that protect every bit of user and application data stored on a mobile device. But organizations that mandate full-device encryption will need to be a bit more selective, avoiding Windows Phone 7 and Android devices that are physically unable to support this policy. (Alternatively, data stored on those devices can be software-encrypted.)
All four mobile operating systems can use Transport layer security (TLS) to protect over-the-air Web and email traffic and/or Wi-Fi Protected Access 2 (WPA2) to protect Wi-Fi traffic. However, virtual private network (VPN) support varies in sometimes-subtle ways. For example, Android 4 is the only OS that supports third-party Internet Protocol Security (IPsec) VPN clients, but iOS offers far better MDM control over VPN policies. If your company requires VPN support for mobile devices, consult your VPN gateway vendor to determine known interoperable mobile operating systems and versions.
Finally, mobile operating system malware resistance depends on many factors, including public app store provenance, users' ability to install apps sideloaded from less trustworthy sites, and permissions granted to installed apps. For example, Apple exerts tight control over the iTunes App Store and prevents users from sideloading public apps not reviewed and signed by Apple. This has proven a reasonably effective malware deterrent, compared to the more relaxed Google Play Store oversight, which has allowed Android malware to blossom. When malware does exploit a new vulnerability, the shorter patch flows associated with Apple and RIM manufactured devices reduce risk.
Although it is difficult to roll all of these security capabilities into a single "grade" for simple comparison of mobile operating system security, BlackBerry phones are widely regarded as the most secure devices, followed by Apple iPhones and iPads. Android device security is improving but still depends heavily on device make and model.








