5 tips for iOS and Android kiosk device management
IT pros can deploy configurations for kiosk devices with mobile management tools, such as Microsoft Intune. Consider these tips to ensure kiosk devices function as intended.
Mobile device admins must tailor their management practices and policies specifically to meet the needs of all types of endpoints.
For example, BYOD device management allows IT to institute fewer, less complex policies. IT doesn't necessarily need to enroll these devices in a unified endpoint management (UEM) or enterprise mobility management (EMM) tool, and they can focus on managing applications and data.
Kiosk devices, or dedicated devices, which have a single use case, such as checking in patients to a healthcare facility, typically require more specific configurations.
Though the screenshots below show these configurations in Microsoft Intune's UEM, IT can use other UEM or EMM tools to deploy many of these kiosk device configurations.
With these five tips, mobile admins can improve Apple iOS and Google Android kiosk device management.
1. Enroll devices right out of the box
IT professionals must activate the devices they want to run as kiosks with Android Enterprise corporate-owned mode or iOS Supervised Mode for each respective OS. Then, IT can completely lock down the device with stricter configuration policies.
2. Choose user affinity over device only
For iOS devices, IT has the option to activate Supervised Mode via Apple Business Manager or the Apple Configurator, with or without user affinity. When IT pros configure user affinity on devices, they can deploy software and policies based on groups of users in Microsoft Azure Active Directory (AD) instead of groups of devices.
This way, IT can deploy configurations, applications and updates to kiosk devices more quickly than deploying them by device group, as it takes a while to add devices to groups in Azure AD after IT enrolls them.
3. Lock down iOS for one or more apps
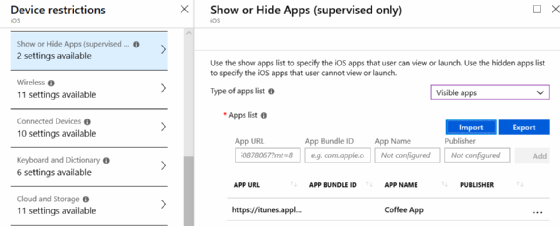
For iOS devices, IT has three options to lock down the device and only allow users to start one application. You can hide certain applications with the Show and Hide Apps configuration in iOS Device Restrictions, which certain UEM or EMM tools include, such as Intune (Figure 1).
When running a device with this configuration, the user only sees the configured app or apps on the iOS device.
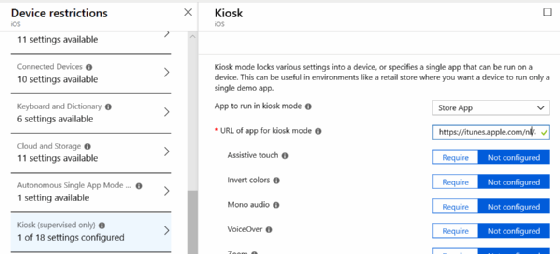
The second option is to use the kiosk Device Restrictions in an EMM or UEM tool to configure the device to only run the app in Kiosk mode (Figure 2). This configuration restricts the entire kiosk's UI to a single chosen application.
4. Update dedicated devices via maintenance windows
It can be a challenge to update kiosk devices, but IT pros should update them as regularly as possible. Ideally, they should deploy the latest versions of the OSes automatically.
In Android Enterprise, IT can automatically update devices based on maintenance windows or preset times. This configuration shown in Intune's interface ensures that updates don't run in the middle of business hours when users need the devices operational so they can log a sale or perform some other work-related task (Figure 3).
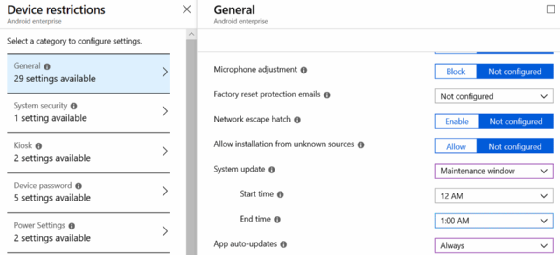
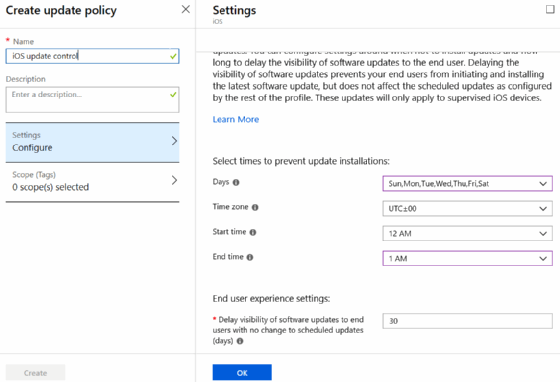
IT can also use maintenance windows to automatically run updates on supervised iOS devices (Figure 4).
5. Set Android devices to single or multi-app mode
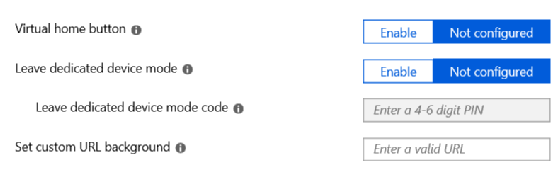
When IT pros enroll kiosk devices in Android Enterprise in the dedicated device scenario, they need to create a configuration profile that locks down the device to Android Kiosk mode. With Intune, for example, IT can lock a particular device to operate as a kiosk device in two ways: in single app mode or in multi-app mode (Figure 5).
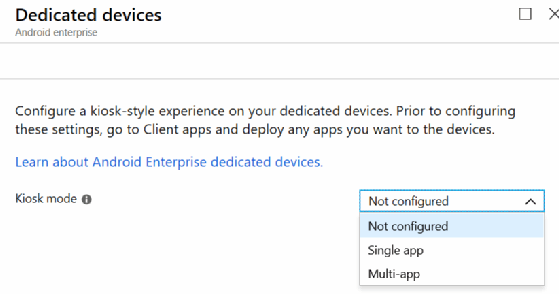
With a dedicated device, IT can configure single app mode and select the Android app it wants to make available in the Intune portal. IT professionals must deploy the app to a static or dynamic Azure AD group containing the objects of the devices.
When configuring the multi-app mode in Intune, IT pros can select multiple Android apps. They can also configure other aspects of the device's restrictions, such as the virtual home button, whether or not users can leave dedicated device mode, and a custom URL for a background (Figure 6).