Infographic: When to use MDM, MAM, and other EMM techniques
A visual guide to how Android Enterprise, iOS MDM, and mobile threat defense apply to BYOD, COPE, embedded devices, and the extended enterprise.
I’m excited to once again update our infographic on enterprise mobility management technologies and use cases. (Previous versions were published in October 2018 and February 2018.)
At BrianMadden.com, we write plenty of articles on all sorts of EMM technologies like MDM, MAM, and BYOD, as well as more recent concepts like conditional access and Apple’s User Enrollment mode. You can find a whole list of recommended articles and websites in our EMM resource guide.
I also like to lay everything out in one handy infographic, shown below.
We can’t quite include everything for reasons of space and practicality, but if you have any feedback, please leave a comment or find me on Twitter.
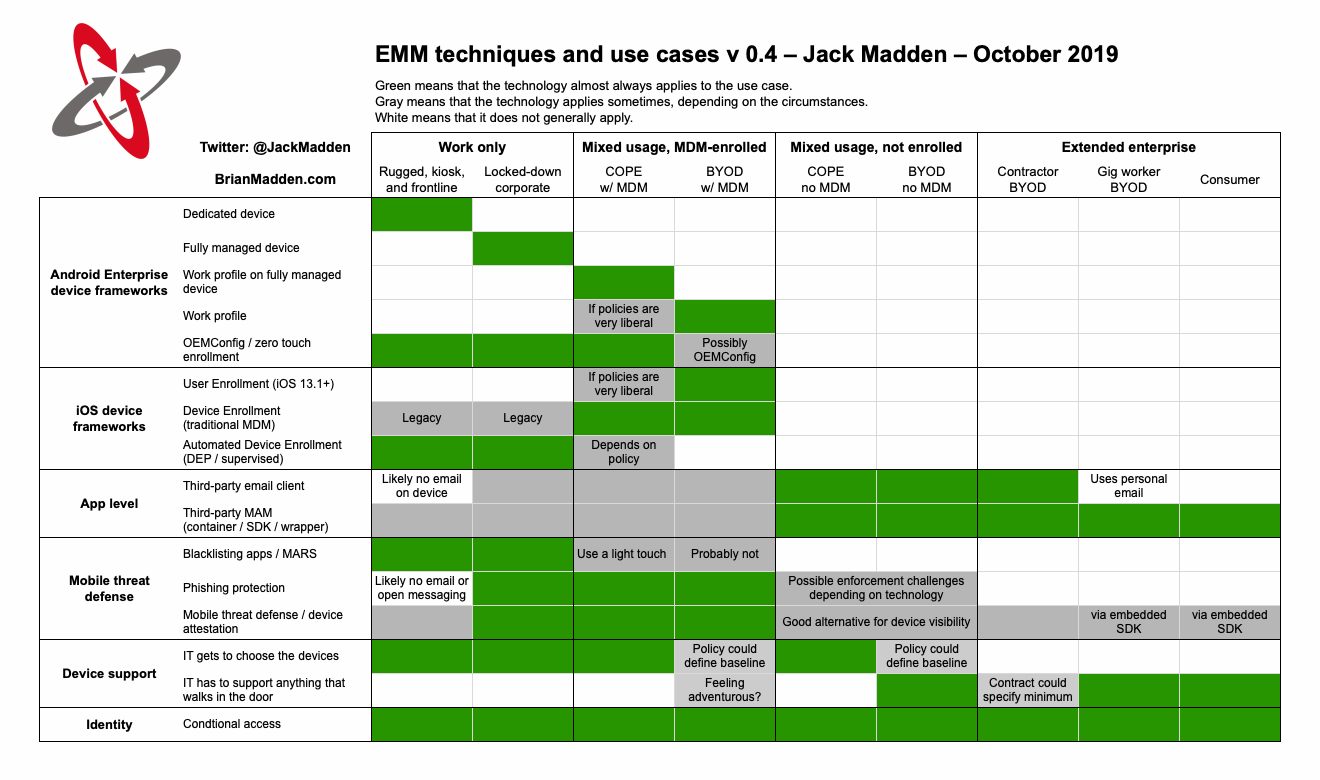
Transcript
The EMM techniques and use cases infographic is a matrix that lists deployment scenarios along the horizontal axis, and EMM technologies and concepts along the vertical axis. The cells in the matrix are marked to indicate whether the technologies are applicable either almost all of the time, or sometimes depending on the circumstances, or that they do not generally apply.
Here’s a list of the use cases and which technologies apply:
Rugged, kiosk, and frontline devices:
- Generally applies: Android Enterprise dedicated device mode; Android Enterprise OEMConfig and zero touch enrollment; iOS Automated Device Enrollment (DEP); mobile app reputation services; IT gets to choose the devices; identity management with conditional access;
- Sometimes applies: iOS Device Enrollment (i.e. traditional MDM) for legacy deployments or devices in countries without all Apple services; third-party mobile app management (container, SDK, or wrapper); mobile threat defense (the device may be so locked down that it is not viewed as necessary);
Locked-down corporate devices, with no personally installed applications:
- Generally applies: Android Enterprise fully managed device; Android Enterprise OEMConfig and zero touch enrollment; iOS Automated Device Enrollment (DEP); mobile app reputation services; mobile threat defense; IT gets to choose the devices; identity management with conditional access; phishing protection;
- Sometimes: iOS Device Enrollment (i.e. traditional MDM) for legacy deployments or devices in countries without all Apple services; third-party mobile app management (container, SDK, or wrapper); third-party email client;
Corporate-owned, personally enabled (COPE) devices that are enrolled in MDM:
- Generally applies: Android Enterprise work profile on fully managed device mode; Android Enterprise OEMConfig and zero touch enrollment; mobile threat defense; IT gets to choose the devices; identity management with conditional access; iOS Device Enrollment (traditional MDM); phishing protection;
- Sometimes: iOS Automated Device Enrollment (DEP), depending on the interpretation of COPE; mobile app reputation services; Android Enterprise work profile only, depending on interpretation of COPE policy; iOS User Enrollment, also depending on COPE policy; third-party mobile app management (container, SDK, or wrapper); third-party email client;
BYOD devices that are enrolled in MDM:
- Generally applies: mobile threat defense; identity management with conditional access; iOS User Enrollment; iOS Device Enrollment (traditional MDM); phishing protection; Android Enterprise work profile only;
- Sometimes: Android Enterprise OEMConfig; third-party mobile app management (container, SDK, or wrapper); mobile app reputation services, if app blacklisting is used with a very light touch; IT may set baseline device support list, or may attempt to support anything that walks in the door; third-party email client;
Corporate-owned, personally enabled (COPE) devices that are not enrolled in MDM:
- Generally applies: third-party mobile app management (container, SDK, or wrapper); IT gets to choose the devices; identity management with conditional access; third-party email client;
- Sometimes: phishing protection, however there are possible enforcement challenges depending on the technology; mobile threat defense (this is a good alternative to MDM for device visibility);
BYOD devices that are not enrolled in MDM:
- Generally applies: third-party mobile app management (container, SDK, or wrapper); identity management with conditional access; third-party email client;
- Sometimes: mobile threat defense (this is a good alternative to MDM for device visibility); phishing protection, however there are possible enforcement challenges depending on the technology; IT may set baseline device support list, or may attempt to support anything that walks in the door;
Contractor BYOD:
- Generally applies: third-party mobile app management (container, SDK, or wrapper); identity management with conditional access; third-party email client;
- Sometimes: mobile threat defense (this is a good alternative to MDM for device visibility); IT may set baseline device support list, or may attempt to support anything that walks in the door;
Gig worker or “app-based” worker BYOD:
- Generally applies: third-party mobile app management (container, SDK, or wrapper); identity management with conditional access; IT has to support anything that walks in the door;
- Sometimes: mobile threat defense via SDK integrated into app;
Consumer devices:
- Generally applies: third-party mobile app management (container, SDK, or wrapper); identity management with conditional access; IT has to support anything that walks in the door;
- Sometimes: mobile threat defense via SDK integrated into app;








