
What is mobile device management (MDM)?
Mobile device management (MDM) software enables IT administrators to control, secure and enforce policies on smartphones, tablets and other endpoints.
MDM is a core component of enterprise mobility management (EMM) and unified endpoint management, which aims to manage all endpoint devices with a single console. These platforms include mobile application management tools, identity and access management (IAM), and enterprise file sync and share. MDM intends to optimize the functionality and security of mobile devices within the enterprise while protecting the corporate network.
Modern enterprise mobility products support major cloud platforms, including Amazon Web Services, Google Cloud and Microsoft Azure. They enable IT administrators to remotely manage and secure smartphones, tablets, laptops and desktop devices across multiple platforms, including Android, ChromeOS, iOS, Linux, macOS and Windows. MDM tools also support some connected internet of things (IoT) devices.
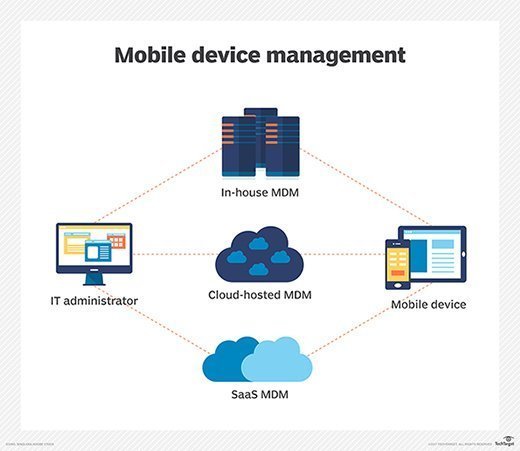
Although many MDM products can be deployed on-premises or as appliances, numerous vendors also offer their products as software as a service because of its flexibility and pay-as-you-go cloud-based services model. This makes it easier for organizations to onboard and offboard devices.
MDM software can manage devices in any industry where employees use their own mobile devices for work-related activities, commonly referred to as bring your own device (BYOD). This includes healthcare, finance, manufacturing, telecommunications, education, retail and government.
How mobile device management works
MDM relies on endpoint software called an MDM agent and an MDM server in the cloud. IT administrators configure policies through the MDM server's management console, pushing those policies over the air to the MDM agent on the device. The agent applies the policies to the device by communicating with application programming interfaces (APIs) built directly into the device's operating system (OS). Similarly, IT administrators can deploy applications to managed devices through the MDM server.
BYOD mobile device management
BYOD refers to corporate IT policies allowing employees to perform work-related activities on their personal smartphones and computers. It has been widely embraced since the late 2000s, gaining traction during COVID-19 and maintaining its appeal today.
MDM is a crucial part of BYOD, enabling organizations to enforce security policies on these user devices. It protects sensitive corporate data and allows companies to enforce compliance with company regulations. Organizations can isolate corporate data from personal data and track all employee devices connected to their network.
However, deploying MDM in a BYOD environmentintroduces some challenges. Organizations must balance IT's need to secure corporate apps and data with the end user's need to maintain privacy. Users are often concerned with IT's ability to monitor their actions on a mobile device, but privacy settings can help alleviate those concerns.
Organizations can use other methods to maintain user privacy while deploying MDM for BYOD environments. Some MDM platforms offer app wrapping, which provides a secure wrapper on mobile apps. It enables IT to manage different providers' apps from a central location and enforce strong mobile security controls such as data encryption and usage monitoring. For example, Android Enterprise, Google's open source framework of APIs for Android devices, integrates with leading EMM providers. Android Enterprise offers containerization, which separates work and personal profiles so end users can keep their personal data away from IT's control. This enables IT administrators to secure corporate data and apps as needed.
The components of MDM tools and software
MDM's primary jobs are security management and enforcement on mobile devices. To do this, most MDM software provides the following components:
- Configuration management. MDM contains an over-the-air transmission capability that enables IT to configure and administer security and firmware updates to mobile devices, no matter where they are located in the enterprise.
- Compliance and governance management. Because companies must ensure compliance and governance policies are uniformly applied across all mobile devices, MDM enables IT to set these requirements without having to configure each device physically. The MDM software also gives IT visibility across all mobile devices to ensure they remain secure and compliant.
- Security. IAM enables an enterprise to manage user identities associated with a specific device and regulate user access through single sign-on, multifactor authentication or role-based access.
- Risk management. MDM enables IT to track lost or misplaced devices or, in a worst-case scenario, to wipe all data clean from a device. These capabilities protect the company from data loss and intellectual property theft.
- Remote troubleshooting. With MDM, devices can be updated remotely. This enables IT to remain onsite without traveling to remote locations to perform troubleshooting and repairs.
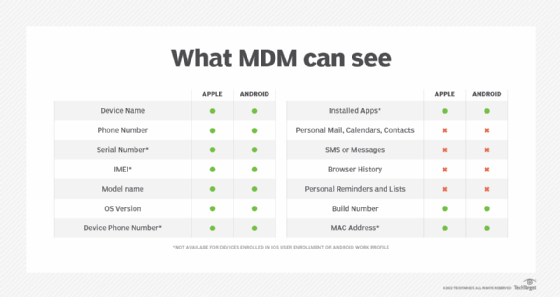
What information MDM tracks
MDM enables IT administrators to monitor and manage user devices while prioritizing privacy by tracking the following information:
- Device details. The 15-digit International Mobile Equipment Identity (IMEI) number acts as a fingerprint, enabling it to be tracked if lost or stolen. The IMEI also provides the phone's brand and carrier information and enables features like location tracking and device blocking. The IMEI can retrieve information, including the device's model, serial number, manufacturer, battery life and storage capacity.
- User information. This information includes the user's name to whom the phone is assigned and their details.
- Software details. This includes the OS version, installed applications, updates and security patches.
- Location. This provides the device's GPS location so it can be tracked in case of loss or theft.
- Network connectivity. This includes cellular and Wi-Fi networks to which the device is connected.
- Security status. This includes security policies, passcode compliance and device encryption status.
- Usage data. This includes data usage statistics and application usage patterns.
Certain MDM privacy constraints also apply. For example, when MDM tracks a user's smartphone, it can't see the user's history, contacts, calendar, password or photos.
Benefits of MDM tools
MDM software offers the following benefits:
- Contributes to corporate risk management. MDM's ability to track and wipe lost or misplaced devices is a significant deterrent against cybertheft.
- Provides remote device control. MDM enables IT to troubleshoot and fix user devices and install software remotely, saving time and money.
- Reduces administrative overhead. MDM can manage all devices and endpoints from a single software platform.
- Provides policy enforcement. MDM monitors security policies across all managed devices, promoting the enforcement of uniform standards.
- Reduces costs. MDM provides automated patching and updates, minimizing the need for IT support.
Mobile device management features
The developers of mobile OSes and manufacturers of mobile devices control what MDM software can and can't do on their devices through their APIs. As a result, MDM has become a commodity, with most vendors offering a similar set of core capabilities. MDM vendor differentiation comes by integrating mobile device management servers with other enterprise software.
Common MDM product features include the following:
- Device enrollment for onboarding new devices and setting security policies.
- Predefined user profiles set by an MDM administrator for quicker onboarding.
- Device inventory and tracking with reporting throughout the entire mobile device lifecycle.
- Self-service features that enable end users to resolve common IT issues, such as security updates, without having to put in a help desk ticket.
- App management, including distributing new apps, updating apps, removing unwanted apps or using an enterprise app store.
- Integration with mobile threat defense or mobile threat intelligence offerings to prevent malware and other attacks that target mobile devices.
- Device hardware feature controls that enable administrators to restrict camera usage and access to insecure public Wi-Fi networks.
- Content management to govern and secure organizational content, such as sales enablement content on mobile devices.
- Device location management using GPS andremote wipeto protect lost, stolen or otherwise compromised mobile devices.
- Password enforcement that IT administrators can manage through policies.
- Reporting and analytics for tracking and reporting on device data and cellular usage, compliance and security.
- Application allowlisting and blocklisting.
- Data encryption enforcement to help protect against malware and other data compromise.
Best practices for mobile device management
An organization should consider the following four best practices when implementing MDM:
- Develop a comprehensive mobile device policy. As part of an overall cybersecurity strategy, develop a policy that outlines the organization's acceptable use of mobile devices, including device security, data protection and app usage guidelines. This policy should be regularly reviewed with IT, security and business stakeholders and communicated to employees.
- Vet MDM vendors for their strength of training and technical support. Be sure the vendor provides in-depth training on the functionality and features of its product and offers the level of technical support the organization needs.
- Develop a secure configuration standard for corporate devices. This should include setting devices to receive security updates over the air. The device standard should also include strong passwords, encrypted storage for data security and automated device locking.
- Train employees. Educate employees onmobile device security, starting with best practices for securing their personal devices. The training should also cover the security of corporate-owned devices and the importance of securing corporate data, especially if the organization must meet industry compliance programs such as HIPAA, Payment Card Industry Data Security Standard or the Sarbanes-Oxley Act. Training must also cover the consequences of noncompliance for the organization and its employees.
How to implement MDM in the enterprise
The following are six essential steps for implementing mobile device management:
1. Obtain management approval. Initiating an MDM project makes no sense if enterprise management doesn't understand why it is needed and where it fits in the overall enterprise security and risk management scheme. To secure their approval, the case for MDM should be presented to management before the project starts.
2. Determine the enterprise's MDM needs. The following questions can serve as a starting point to help assess the organization's needs:
- Does the organization have a BYOD policy currently in place?
- What types of enterprise mobile devices and applications must be managed? Are they centered around smartphones, laptops and other standard IT types, or are there many IoT sensors and specialized devices that must be managed?
- What types of applications are on these devices and what integration will be needed for MDM to work with other IT systems?
3. Develop MDM policies. Policy considerations should include the following:
- Will the MDM be used only for enterprise-owned equipment or does the enterprise also use employee devices?
- Who will be responsible for managing and administering the MDM?
- What are the respective roles and responsibilities of users, department heads, human resources (HR), IT and possibly an internal regulatory or audit group?
- What types of applications and data will be allowed on devices?
- For privacy purposes, what information will the MDM collect and track on devices, and what information will remain personal for users?
These policy considerations should be defined, drafted, presented, reviewed and approved by upper management, user department heads, HR, IT and possibly an audit group. Obtaining advice from an outside audit firm with experience with the MDM policy-setting process is also helpful.
4. Evaluate MDM software and select a tool. Develop a request for proposal for prospective vendors that states the enterprise's monitoring, tracking and management requirements. List the types of mobile and IoT devices the enterprise uses and the applications they use.
Ideally, a pilot program should be conducted so IT can determine how effective and user-friendly the MDM software is and whether it will easily integrate with other security and monitoring software.
5. Configure devices and train users. Once an MDM offering is selected and IT is trained, the process of configuring MDM on individual devices and IoT begins. A recommended approach is to roll out MDM in phases, starting with one department. Once the MDM is properly configured and all department users are trained on policies and procedures, roll out the MDM tool to the next group of users.
6. Use MDM to monitor, track and manage devices. Begin using the tool to monitor, track and manage mobile devices and periodically audit and report on device management, security and compliance.
MDM vendor landscape and trends
The MDM vendor landscape has changed significantly since its inception due to larger firms acquiring startups to add mobile device management functionality to their product portfolios.
According to market research firm Fortune Business Insights, the mobile device management market was valued at $12.15 billion in 2024. It's expected to grow to $81.72 billion by 2032.
The following are examples of some of the MDM vendors in the market:
- Applivery.
- Cisco.
- Hexnode.
- IBM.
- Jamf.
- LogMeIn.
- ManageEngine.
- Microsoft.
- NinjaOne.
- Rippling.
- Scalefusion.
- VMware.
Are open source MDM products as effective as commercial products? Weigh the pros and cons and learn what open source products options exist.





