Wireless Transport Layer Security (WTLS)
What is Wireless Transport Layer Security (WTLS)?
Wireless Transport Layer Security (WTLS) is a security level for the Wireless Application Protocol (WAP), specifically for the applications that use WAP. It is based on Transport Layer Security (TLS) v1.0, which is a security layer used in the internet and is a successor to Secure Sockets Layer (SSL) 3.1.
Wireless Transport Layer Security explained
WTLS was developed to address issues surrounding mobile network devices including limited memory capacity, lower processing power and low bandwidth. It also provides authentication, data integrity and privacy protection mechanisms.
Designed to support datagrams in a high-latency, low-bandwidth environment, WTLS provides an optimized handshake through dynamic key refreshing, which allows encryption keys to be regularly updated during a secure session. The method helps clients and servers communicate over a secure and authenticated connection.
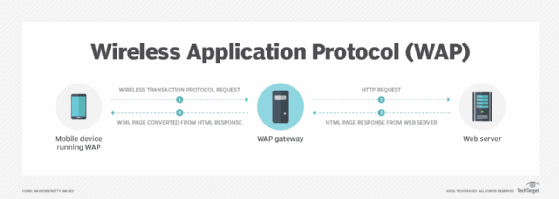
TLS and Wireless Transport Layer Security
The WTLS layer operates above the transport protocol layer. TLS, a standard security protocol used between web browsers and web servers, was modified to develop WTLS. The modification was required because mobile networks could not guarantee end-to-end data security. Consequently, WTLS is optimized for low-bandwidth mobile devices compared to TLS (hence the "wireless").
WTLS is more efficient than TLS, and it requires fewer message exchanges. When a message is in the transport layer, WTLS provides privacy management, as well as data authorization and data integrity.
Here are other differences between WTLS and TLS:
- Compressed certificate format: WTLS follows the 509 v3 certificate structure.
- Compressed data structure: WTLS uses smaller data structures. Packet sizes are reduced by using bit fields and truncating cryptographic
- Packet-based: Unlike TLS, which is stream-based, WTLS is packet-based which allows protocols like Short Message Service (SMS) to be used for data transport.
Despite these differences, WTLS offers similar functionality to TLS.
Features of Wireless Transport Layer Security
There are several important features and benefits of WTLS.
Data integrity
WTLS achieves data integrity by using message authentication to ensure that the data sent between a client and gateway is not modified.
Privacy
WTLS uses encryption to ensure that the data cannot be read by an unauthorized middleman or third party.
Authentication
WTLS uses digital certificates to authenticate the parties involved in a transaction or communication.
Denial-of-service (DoS) protection
WTLS detects and rejects replayed messages and messages that are not successfully verified to prevent DoS attacks.
Wireless Transport Layer Security architecture
WTLS includes two layers of protocols.
The WTLS Record Protocol provides basic security to higher layer protocols. It takes user data from the next higher layer and encapsulates it in a protocol data unit.
The following steps are involved in the protocol:
- Initially, a lossless compression algorithm compresses the payload.
- This is followed by the computation and addition of a Message Authentication Code (MAC) over the compressed data using hash-based MAC (HMAC). Hash algorithms like MD5, SHA-1, etc., can be used with the HMAC, with the length of hash code as 0, 5 or 10 bytes.
- The compressed data with MAC is encrypted using a symmetric encryption algorithm like Data Encryption Standard (DES), triple DES, RC5 or the International Data Encryption Algorithm.
- A header gets prepended to the encrypted payload.
The record protocol header consists of record type, record length field indicator, sequence number field indicator, content type and cipher spec indicator.
WTLS also defines several other important higher layer protocols.
Handshake protocol
This complex WTLS protocol allows the server and client to authenticate each other. It also generates a pre-master secret, which is used to generate a master secret, which in turn is used to generate cryptographic keys. The handshake protocol must be used before application data is transmitted.
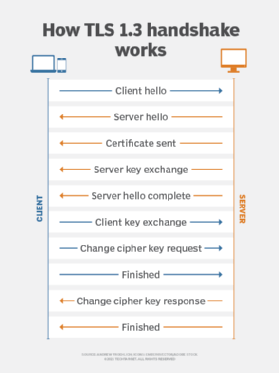
The protocol consists of multiple messages exchanged between client and server. The exchange consists of the following four phases:
- initiating a logical connection and establishing security capabilities;
- server authentication and key exchange;
- client authentication and key exchange; and
- setting up a secure connection to complete a handshake and allow the client and server to exchange application layer data.
Change cipher spec protocol
Considered the simplest WTLS protocol, the change cipher spec protocol consists of a single message of a single byte with a value of 1. The message copies the pending state into the current state, updating the cipher suite to be used on the connection. When the message arrives, the message sender sets the current write state to pending state, while the receiver does the same to the current read state.
Alert protocol
This protocol conveys WTLS-related alerts to the peer entity. These alerts are compressed and encrypted. Each message consists of 2 bytes, with the first byte taking the value -- warning (1), critical (2) or fatal (3), signifying the message severity. The second byte houses the code that indicates the specific alert.
For instance, if the level is fatal, WTLS immediately terminates the current secure connection. Although other connections using the session can continue, no new connections can be established on the session.
Some examples of fatal alerts include the following:
- unexpected_message: The message received is inappropriate.
- session_close_notify: The recipient is notified that the sender will not send further messages using this connection state or secure session.
- bad_certificate: A corrupt certificate was received.
- certificate_expired: The received certificate has expired.
WTLS sessions and connections
WTLS supports secure connections and secure sessions.
Secure connections
A connection is a transport that provides a suitable type of service. In WTLS, connections are transient. Each connection is associated with one session. There may be multiple secure connections between any pair of parties.
Secure sessions
In WTLS, sessions define the cryptographic security parameters that can be shared across multiple connections. A session is an association between a client and a server. A number of parameters are used to define a session state, including session identifier, compression method, protocol version, sequence number and master secret.








