How to integrate mobile threat defense and UEM such as Intune
Mobile admins can use mobile threat defense integrations with UEM to provide deeper visibility into the threat level of mobile devices and additional security controls.
Many organizations adopt a unified endpoint management platform to help with various critical device management tasks that range from patch deployment, asset tracking, software installs and device security controls.
However, the growing need for security and advanced threat protection on all assets, including mobile devices, is causing mobile threat defense (MTD) tools to be a higher priority within unified endpoint management (UEM) platforms.
By integrating MTD into a management platform, IT administrators can employ a new level of protection that goes beyond traditional virus and malware detection via signatures. MTD allows them to view the risk of each device based on the analysis of activities, using AI to detect and flag any abnormal behavior. IT administrators should learn how the MTD and UEM integration process works to ensure this process goes smoothly.
Review existing UEM integration capabilities
For some popular platforms, such as Microsoft Intune, Citrix Workspace, MobileIron UEM, Ivanti and ManageEngine, introducing an MTD platform can be straightforward. Vendors require the selection of the MTD platform from available integrations in those UEM consoles, which enables the UEM to exchange all relevant information such as alert levels and app details with the MTD.
The following MTD platforms include a variety of UEM integrations:
How MTD and UEM work together
While UEM can provide visibility for an enrolled device's general health, it also provides details on the security score once administrators integrate an MTD product with the UEM. The use of MTD and UEM means that IT administrators can implement conditional access where devices must meet a set of compliance criteria before they can access networks and corporate data. The criteria may include the following:
- running the latest or a minimum version of the OS;
- having the latest updates for all installed critical apps;
- having an MTD product deployed and running on the device;
- requiring a passcode to access the device;
- an MTD report that verifies the device is safe and free of threats; and
- device enrollment in UEM.
It's fair to say that UEM and MTD need each other and do a great job complementing each other. IT and security administrators must recognize that to manage their security and mobile assets efficiently.
How to integrate MTD with UEM
IT administrators tasked with connecting UEM platforms with an MTD product will need to follow different steps depending on which platform they use. However, there is a general process that any MTD integration setup follows. This article will use Microsoft Intune -- now Microsoft Endpoint Manager -- as the example platform to integrate with.
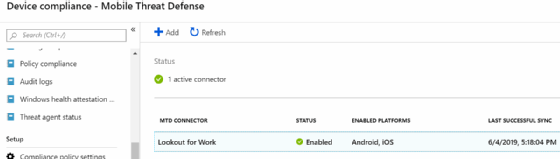
IT administrators must configure a mobile threat defense connector for each third-party vendor for device management. Once IT configures the connector and Intune validates the tool, the mobile threat defense tool will be enabled (Figure 1).
With the connection between Intune and the mobile threat defense tool in place, IT can detect a potentially malicious app on a user's mobile device. The mobile threat defense tool assesses the app and calculates a Device Threat Level, which appears in Intune (Figure 2).
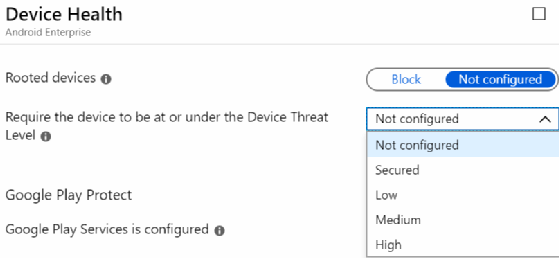
Based on the compliance state of the flagged device, the mobile threat defense tool may automatically block a user's access to internal services that require Azure Active Directory's (AD) conditional access. IT can determine the threshold for blocking access in Intune's compliance policies. The table below explains the Device Threat Levels.
| Level | Description |
| Secured | No threat allowed |
| Low | Only low threats allowed |
| Medium | Only low and medium threats allowed |
| High | All threat levels allowed |
When the mobile threat defense tool detects a threat on a mobile device, Intune automatically blocks access based on the maximum Device Threat Level allowed in IT's preset compliance policy (Figure 3).
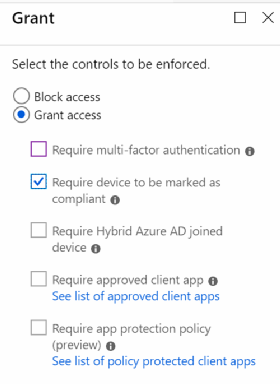
Suppose there is suspicious activity that the mobile threat defense tool didn't pick up. IT can manually block a device, require multifactor authentication for the next time the mobile user accesses services behind Azure AD's conditional access or perform several other commands.
The Intune mobile threat defense integrations are great for organizations with legacy Android and iOS devices to check for the latest security updates. When IT pros use Android Enterprise for BYOD management, they may need to put in extra work because the work profile is separate from the user's personal profile. IT should focus more on securing the personal side of the device because Intune already secures the work profile.







