
kras99 - stock.adobe.com
Secure Kubernetes with this Kubescape tutorial
Kubescape can help discover misconfigurations in a Kubernetes cluster by scanning various resource types. Learn how to use the platform to scan clusters.
Every organization that uses Kubernetes must prioritize keeping it secure, but Kubernetes does not have built-in security scanning features. Tools such as Kubescape help automate the process of identifying risks associated with components and configurations in a Kubernetes cluster.
Kubescape is an open source security platform for Kubernetes. It works by scanning various types of resources -- such as the YAML files that configure clusters and Helm charts -- to detect known security flaws. The platform automatically compares configurations against security best practices as defined by the National Security Agency and the Cybersecurity and Infrastructure Security Agency, CIS Benchmark and MITRE ATT&CK frameworks. Then, it reports settings that deviate from those that the frameworks recommend.
Auditing configurations and resources in Kubernetes by hand is possible but requires time and is not feasible in large-scale clusters. The IT administrator in charge of securing Kubernetes must know the key types of scans to perform to help secure Kubernetes. Using Kubescape can help detect risks in an easy and efficient manner.
Kubescape limitations
Kubescape's main functionality is limited to security scanning. It is not a security monitoring tool for Kubernetes.
Kubescape won't help detect signs of ongoing attacks, such as malicious requests against applications running in Kubernetes. For that use case, use a security monitoring tool that can ingest data from a Kubernetes cluster and detect anomalies or unusual behavior that may result from a security breach.
How to install Kubescape
You can install Kubescape in most environments with a curl command.
curl -s https://raw.githubusercontent.com/kubescape/kubescape/master/install.sh | /bin/bashThis command downloads and runs the Kubescape installation script from GitHub. The process should take two or three minutes.
Scanning with Kubescape
The two main ways to use Kubescape for scanning are scanning an entire cluster or scanning specific resources.
Cluster scanning
Cluster scanning tells Kubescape to scan all parts of the cluster that it can analyze.
To run a cluster scan, type the following:
kubescape scanRefine the scan by specifying a namespace using the --include-namespaces flag.
kubescape scan --include-namespaces devExclude certain namespaces with --exclude-namespaces.
kubescape scan --exclude-namespaces prodResource scanning
To scan a particular YAML file or Helm chart rather than scanning an entire cluster or namespace, run the kubescape scan command followed by the path to the resource, as in the following example:
kubescape scan /path/to/file.yamlTo specify a path to a directory, Kubescape will scan everything in that directory. Kubescape supports scanning URLs to scan remote files.
Interpreting scan results
After scanning, Kubescape generates a report that describes any risks it detects. For example, it can provide a security posture overview for a cluster.
In this overview, Kubescape shows a summary of cluster security posture, including the number of users who can perform administrative actions. For each result greater than 0, evaluate its need and then define an exception to allow it. This baseline can be used to detect drift in future.
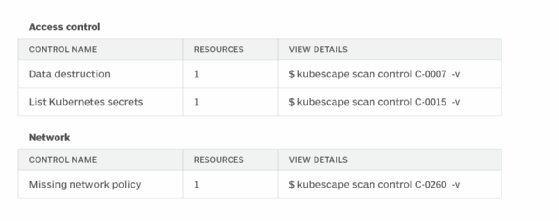
In this example, Kubescape identifies three risks across two configuration categories -- Access control and Network. Each risk is accompanied by a command, such as kubescape scan control C-0007 -v, that can run to collect details about why Kubescape identified the risk and how to correct it.
By default, Kubescape prints scan output to the command line. It is possible to save it in various other formats (such as HTML and PDF) using the --format and --output flags when initiating a scan.
For example, to save the output as HTML to a file named output-file.html, run the following:
kubescape scan --format html --output output-file.htmlGetting the most from Kubescape
Consider these best practices when using Kubescape:
- Run granular scans. Scanning an entire cluster takes time and may result in more potential risks. For that reason, break down scans by namespace or scan individual resources.
- Scan before deploying. Detect risky configurations before you apply them. Run Kubescape scans on YAML files and Helm charts when they are still local files before you deploy them into a cluster.
- Don't blindly trust Kubescape output. Kubescape detects risks based on popular security frameworks. But cluster configurations may deviate from standard setups in ways that make Kubescape's findings less relevant. While it makes sense to use Kubescape as a starting point to identify risks, don't assume that every risk it finds is valid, or that just because Kubescape deems a resource secure that it is optimally configured for your setup.
- Keep Kubescape up to date. If you install Kubescape using curl as previously specified, it won't automatically update when a newer version becomes available. An older version of Kubescape could result in an outdated scan and vulnerability of data. Avoid this risk by re-running the installation command to ensure you're using the latest version of Kubescape. You can also install Kubescape on some Linux distributions using a package manager that will automatically update the installation when a newer package is released.
Chris Tozzi is a freelance writer, research adviser, and professor of IT and society who has previously worked as a journalist and Linux systems administrator.








