
kras99 - stock.adobe.com
What to keep in mind when securing virtual environments
Virtual environments can contain numerous vulnerabilities for attackers to exploit -- with potentially devastating results. Use these tips to select security tools and strategies.
Cybersecurity concerns are on the rise, and virtual environments are no exception.
Because successful attacks can be disastrous, it's essential to know where vulnerabilities can occur and compare options for securing virtual environments. Explore potential threats to VMs and learn how to select a security tool.
What are the security threats to VMs?
Consolidating hardware and software for servers is often considered a benefit of virtualization, but this isn't the full picture.
While having fewer hardware platforms might seem beneficial for security management, the number of installed server instances has most likely gone up. Now that hardware isn't a stopping point, server sprawl has -- and will continue to -- run wild in the data center.
Some say the attack surface has shrunk and some say it has grown, but the truth is likely somewhere in the middle. Although hardware vulnerability has decreased, OS vulnerability still exists and now includes hypervisors.
Hypervisor security
The hypervisor is the golden goose when it comes to cyber attacks. Hypervisors represent both a benefit to the data center and a choke point if compromised.
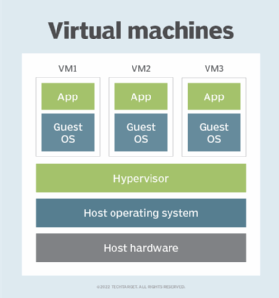
Gaining system access at the hypervisor level can give an attacker ownership of any virtualized component of an organization's environment, which includes the majority of modern data centers. Vulnerabilities such as the Venom security flaw, discovered in 2015, prove that breaches at this level are possible.
Normally, IT teams should approach the hypervisor with a layered security strategy -- but in this case, security layers also affect performance. Hypervisors require white-glove treatment to avoid negatively affecting VM operations while providing the greatest defense possible. Tools designed to secure hypervisors must find a balance between performance and protection.
Selecting a tool for securing virtual environments
The strategy for choosing a security tool depends on your organization's needs and previous investments.
Choosing a vendor
If you already have a robust security system that encompasses antivirus and antimalware software and firewalls, consider specialized virtualization security software to augment your existing setup. Because adopting a new product can add management and operations overhead, choosing among options from vendors you already work with can make the decision easier.
If you prefer a single vendor or use a larger security package, then you'll already understand that vendor's potential limitations. On the other hand, if your existing security products are all from different vendors, adding one more to that collection shouldn't be an issue.
Cloud vs. on-premises
The same goes for SaaS vs. on-premises options. If you're currently running workloads in the cloud, it makes sense to look only at SaaS tools. But if your infrastructure is still on site or your cloud migration is only in the planning stages, you can look at either on-premises or SaaS options.
While on-premises options still exist, most vendors are increasingly focusing on SaaS due to the efficiency and scalability of the cloud. On-premises isn't going away tomorrow, but it is likely that on-premises options have a sunset date already set as more companies adopt a subscription-based model.
Virtualization security requires a comprehensive strategy
Backups, firewalls, antivirus and antimalware software, and now hypervisor security can't be treated as individual parts of the environment to secure. Instead, today's security tools and systems should provide a complete picture for customers.
Many security vendors are moving in that direction, and maybe they're onto something. Look at what hypervisor vendors themselves are doing with internal products: Both Microsoft and VMware have purchased virtualization security products or built them internally.
The threats that can occur during a breach -- even a small one -- can have a massive impact. And with the continued rise of ransomware, there's now serious money to be made from cyber attacks and data breaches. Because any gaps in coverage can be devastating, piecemeal approaches to security aren't advisable today.







