Andrea Danti - Fotolia
SaltStack Enterprise GUI features outreach Salt Open territory
For enterprise IT shops that require a mix of reports on systems, and audit compliance, SaltStack Enterprise offers more than the pure open source version of Salt.
IT organizations often have a choice between pure open source and paid enterprise versions of management and monitoring tools. Here we look at SaltStack Enterprise versus the free version, Salt Open. SaltStack Enterprise has certain advantages and exclusive features, but does it make systems management easier for DevOps and IT orchestration by means of its GUI?
SaltStack Enterprise builds on top of upstream Salt Open. Both versions of the technology perform IT configuration management, enforcing configurations on resources such as servers. Salt Open manages systems entirely via a command-line interface (CLI).
Salt Open and SaltStack Enterprise require the same effort and expertise from the user to execute jobs. GUI or no GUI, the admin must master the concepts of execution modules, highstate, masters and minions. The user writes state files that describe system policy for a configuration by hand, without the help of a wizard.
CLI gurus have reasons to prefer the command line. Via the CLI, Salt enables the user to target minions in various ways, including wildcards, regular expression, OS properties and subnet.
Benefits of SaltStack Enterprise
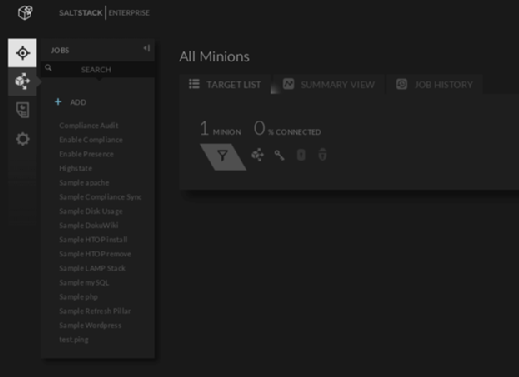
The enterprise version of Salt includes a bevy of sample configs, i.e., top.sls files that delineate the machines on a network and the configuration roles for them (see Figure 1). The SaltStack GUI makes it easier to browse minions and use grains to gather information about targeted systems. Custom outputters are a graphical format for some modules' information, such as disk.usage and network.routes. The most important custom outputter, and perhaps the main reason for the SaltStack GUI, is the one that runs jobs and shows job information.
Beyond these benefits, the paid, supported version of Salt also provides:
- a small set of reports and customizable dashboards in the GUI;
- access to some enterprise functions via REST web services and the Enterprise API (eAPI);
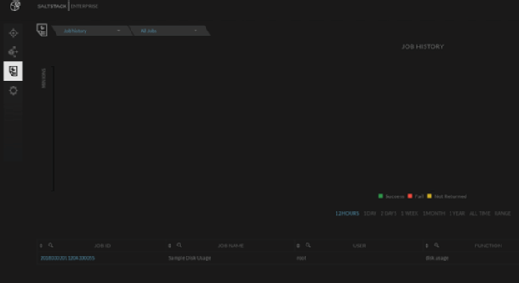
- the ability to persist job history permanently (see Figure 2), which can aid in IT compliance management and auditing;
- easier, and perhaps more reliable, configuration and scaling of multiple masters; and
- Lightweight Directory Access Protocol (LDAP) for authentication, which is crucial in certain regulated industries.
Jobs in the GUI and CLI
You can run jobs or apply highstate from the CLI or GUI in Salt. The principles and even the way you run them are basically the same. To accomplish the task, you must know some details about the module in use.
A job can return a system to its highstate, i.e., use state.apply to invoke the configuration given in top.sls. Or the user can run specific module functions, such as send certain commands to a given software system. For example, the admin might want to create a document in ElasticSearch with the ElasticSearch execution module: salt.modules.elasticsearch.document_create().
Salt Open stores job data in a cache, where it remains until the cache is purged. An open source user can alternatively configure Salt to save this information to an external data store. For customers, SaltStack Enterprise persists job data automatically to a PostgreSQL database, and integrates that job data into the dashboard.
Similarly, a system audit sample top file is available with SaltStack Enterprise, although a savvy user could make one with Salt Open. The SaltStack Enterprise audit functionality is based on Hubble Stack, which is an open source security compliance tool. The user tells SaltStack to push out the tools needed to the targeted minions, such as the Python program hubble.py. Then they enter what metrics should be checked in a YAML file, and kick off the job.
Additional differences between open source and paid Salt
Enterprise API. Users can write programs and retrieve information about Salt or perform administrative procedures via the SaltStack eAPI. For example, you can return a list of audit log records for the current user; delete records from various database tables like events, jobs and schedule; and look up user information.
File server. The SaltStack Enterprise file server is akin to a network file system mount point. Minions access it to retrieve data.
LDAP. The addition of LDAP integration to Salt authenticates users and provides role-based access control: granular control over who can do what. RBAC is required for certain regulated industries. SaltStack Enterprise does not have its own LDAP, but organizations probably already have an LDAP in place, such as Microsoft Active Directory, for Salt to connect to.
Reports. The enterprise version of Salt saves users the time and effort to write reports on highstate status, job history, key state, minion version, OS version and other areas. However, there's no reason why a user cannot create the same reports using Salt Open and the grains API.
While command line gurus will still prefer to use the CLI even if they had the Saltstack GUI available, IT organizations that value reports and RBAC, as well as compliance features such as permanent job histories, should select the SaltStack Enterprise version of the configuration management tool. The enterprise offering includes product support, as well as professional services.
Speak the language
Master: The central command server that issues orders to minions is the Salt Master.
Minion: The clients of the Salt Master, minions enforce configurations on managed systems.
Grain: Grains are data about the systems managed by Salt, and can cover many properties.
Execution module: These packages perform systems management tasks within Salt.
Highstate: Highstate puts into context the state information sent to the minion for configuration.
Installation of SaltStack Enterprise
The Salt server should run on one of these supported Linux distributions: Red Hat Enterprise Linux 7, CentOS 7, SUSE Linux Enterprise Server 12 SP3 or openSUSE Leap 42.3.
Minions, which sit on managed systems to enforce configurations, can run almost anywhere with SaltStack Enterprise: See the full list for masters and minions in Salt's supported OS matrix. Salt Open favors Linux, although the project is aiming for feature parity for managed Windows systems.
To try Salt, take advantage of SaltStack's 14-day trial -- the company will send a download link -- and follow the installation steps below. The author used CentOS 7 for the installation.
Install the master and a minion on the master:
curl -L https://bootstrap.saltstack.com -o install_salt.sh
sh install_salt.sh -P -M
Download SaltStack Enterprise, unzip it and copy two folders to /srv/salt:
sudo su -
unzip SaltStackEnterpriseStates5.3.0.zip
cd SaltStackEnterpriseStates5.3.0
mkdir /srv/salt/
mv eAPI /srv/salt/
mv eAPIMaster/ /srv/salt/
Install the supported, GUI-based tool, and enable the minions plug-ins:
salt-call --local state.apply eAPI
sudo salt-call --local state.apply eAPIMaster
On CentOS 7, the installation might require you to open firewall port 443:
sudo firewall-cmd --zone=public --add-port=443/tcp
Open the console with user ID "root" and password "salt":
https://(local host)
root, salt