PKI authentication explained: The basics for IT administrators
Public key infrastructure is part and parcel of modern digital business, from secure communications to data transmission and beyond. Admins must understand PKI to optimize its benefits.
Public key infrastructure is used in every part of our daily online lives, so IT operations professionals should take a moment to understand what it is and how it works.
PKI authentication is not encryption, though they are often mentioned in the same breath. PKI is based around the notion of verification functions between two parties. PKI authentication underlies modern IT infrastructure.
PKI authentication benefits and use cases
Public key infrastructure authentication enables secure messaging, verification, privacy, nonrepudiation and tamper resistance.
Secure end-to-end messaging. PKI authentication commonly adds security when users visit webpages, but it also can be used with email and messaging in the traditional sense. It is a way to prove the actors' identities.
Verification. Verification is increasingly important to businesses. For example, an attacker could release a fake press release, having massive consequences on a company's share price.
With a way to verify the sender's authenticity over email, recipients can be assured of -- or question -- the validity of the message.
Privacy. A private/public key combination means that the two parties in an interaction can negotiate a shared key to securely transmit data.
Nonrepudiation. Similar to the verification angle on PKI use, if someone signs a message with his or her key, PKI provides irrefutable proof that he or she has signed it.
Tamper resistance. If a stream of data is encrypted, it is not generally possible to inject content into the encrypted data, as the encryption key is not known to the third party.
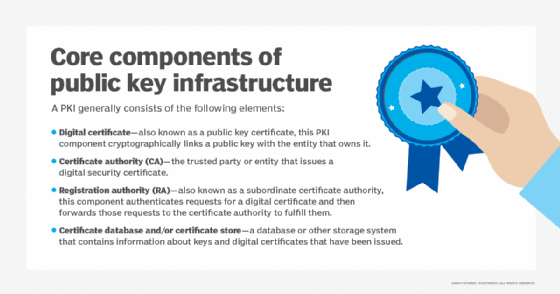
How PKI authentication works: The players and keys
At the heart of PKI authentication is a certificate authority (CA). These CAs provide certificates that irreversibly glue a user to a digital certificate that proves an identity.
To understand certificates, think of them like passports. Passports are provided by an authority that is generally trusted: a country's government. All passports share an agreed-upon format. They serve as proof that individuals are who they say they are. They are trusted all over the world, because the border guard trusts the government that signed the passport. Every passport is signed by the owner and the authorized government department. Also like passports, certificates have a finite lifespan. Web browsers, for example, check web server certificates to ensure they are currently valid. An invalid certificate will display a warning to the user about the site's trustworthiness.
Certificates can be much more secure than passwords. They can be used to decrypt and encrypt keys or provide the owner's identity. The real value in public/private key encryption is that there is no one single password to distribute. Until this point, secure distribution of passwords had been difficult to guarantee. You don't have to worry about sharing a password across an insecure network when using public key infrastructure.
Trust in a certificate -- supplied by governments in the passport metaphor -- comes from certificate providers, such as Verisign and GoDaddy, or an internal corporate provider, depending on the setup. Some certificate authorities have had their certificates revoked, which caused disruption around the internet. The certificate authorities are essentially the arbiter of truth; once that trust is broken, it can wreak havoc on operations.
A party can use these trusted certificate authorities, the PKI providers, to verify the other party in a given interaction is who it claims to be. To prevent forgeries or certificate alterations, the user (system administrator) and the certificate authority digitally sign each one. By signing, the certificate authority essentially says that any user should trust the originator of the certificate.
Public key encryption -- developed by Whitfield Diffie in the 1970s -- is still the encryption foundation of the web today. In the simplest terms: A user generates a cryptographic key with two parts: a public key and a private key. Key generation relies on a trapdoor function, which, essentially, makes the encryption easy to generate but complicated to reverse-engineer.
Key cryptography enables the parties to digitally sign the certificate. The user creates a key pair that consists of a private and a public key. The private key is the important one. It is the master key that digitally signs the certificate.
Once created, the certificate is signed with the public key and countersigned by the PKI provider. The public key can be distributed to anyone. The certificate was encrypted with the private key when signed. The public key must match this private key to verify the certificate, but alone, the public key can't be used to sign anything. That said, public keys are used to establish secure encrypted communications for a web browser. PKI providers offer a public key repository so that people and infrastructure can verify the signed certificate. Microsoft provides a look at the full process on how certificates are used to encrypt web traffic.





