
Getty Images/iStockphoto
Cybersecurity highlights from KubeCon + CloudNativeCon Europe
New AI features took the spotlight at the conference, but security teams must prepare to support AI use with the right policies, controls and access.
Cloud Native Computing Foundation Executive Director Priyanka Sharma kicked off KubeCon + CloudNativeCon Europe by making the case that Kubernetes is the infrastructure to power the future -- with that future being a world of artificial intelligence.
The overall theme at the open source and cloud native conference in Paris last week was AI, specifically how supporting AI workloads will require cost management and interoperability, which can best be served leveraging Kubernetes, open source and the community.
The keynote highlighted updates that should facilitate AI usage. For example, Microsoft Principal Program Manager Jorge Palma provided an overview of the Kubernetes AI toolchain operator, which automates deployment and usage of large language models.
Also, the Cloud Native Computing Foundation (CNCF) AI Working Group released a new cloud-native AI white paper describing how cloud-native technologies support AI and how AI promises to give a boost to cloud-native technologies -- including anticipating load and resource scheduling, increasing resource utilization, reducing latency and, ideally, improving security and resiliency.
Growing use of AI requires security attention
As these improvements enable AI use, security needs to be prepared to support it, including setting the right policies, controls and access. We've already seen security teams struggle to keep up with higher productivity because it can be challenging to gain visibility and control of elements that scale rapidly, including access and permissions, APIs, data, increasing percentages of open source code and data.
Increasing use of AI and production scale will require more effort around data security because AI requires enormous amounts of data and data transfer. Research from TechTarget's Enterprise Strategy Group on data security showed that organizations already struggle in this area: 59% of organizations that have 30% or more of their data in the cloud said they believe it is insufficiently secured. The study showed organizations face the biggest challenges with regulatory compliance, determining risk associated with sensitive data, data governance and the detection/prevention of data exfiltration or misuse. So, this is an area that will need attention with AI usage.
KubeCon + CloudNativeCon sessions and activities also covered other important security topics, such as software supply chain security, privileged access management, zero-trust security and managing security for cloud-native infrastructure and applications. This included hosting a Security Hub session with the CNCF Security Technical Advisory Group to help attendees and share tips on these topics.
The good news is that attendance and interest in those topics demonstrated that developers care about security. The session "I'll Let Myself In: Kubernetes Privilege Escalation Tactics" with Iain Smart from Control Plane assembled a large crowd of attendees who wanted to learn how to keep attackers out of their clusters by understanding adversary methods. The room was too full for many to join.
I was lucky enough to get a seat in the jam-packed room for the session "An Acronym Free Intro to Software Supply Chain Security" by Joshua Lock, an open source and software supply chain security architect with Verizon.
He described the importance of software supply chain security in the context of why developers should care and what they can do, including how to ensure their software quality and protect against unintended software modification. His session highlighted practical tips and guidelines, including practicing good security hygiene, sourcing from trusted suppliers and keeping them up to date, and using only what you need.
DevSecOps across the software development lifecycle
It was also good to see a theme of incorporating security processes for software development across the entire lifecycle. I've written before about shifting security left to developers and how it is often applied by focusing on security tools and processes for developers earlier in the software development lifecycle (SDLC), before applications are deployed. This helps to mitigate risk on the proactive side by catching misconfigurations and security issues before the applications are deployed live to production in the cloud.
However, effective security also depends on IT security working with developers in runtime for efficiency with detection and response once the applications are running. This requires a close partnership between security teams with developers throughout the SDLC.
When you mitigate risk early in development and address preventable issues such as mistakes and misconfigurations, there are fewer issues in deployed applications for attackers to exploit, so you can reduce security incidents and the burden on the reactive side. If and when vulnerabilities are discovered or an incident occurs in runtime, security teams can focus their efforts to respond faster when they can collaborate with development teams to remediate issues.
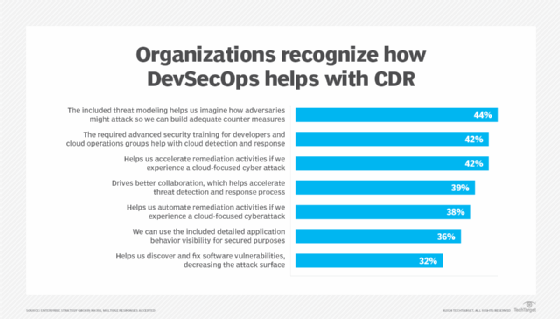
Our research on cloud detection and response showed how organizations recognize the benefits of DevSecOps for faster threat detection and response. For example, it helps with threat modeling to understand how adversaries might attack, and security training for developers and cloud operations groups provide better coordination and responses. It also accelerates remediation in the case of a security incident and drives better collaboration to accelerate threat detection and response processes.
Monitoring and observability also play a key role in driving the efficiency needed for security to scale. Availability and updates for widely used open source software, including Falco and Cilium, and security use cases from application performance monitoring can provide better context. It's also important to understand application behavior to help prioritize remediation efforts in ways that mitigate risks while ensuring application performance and resiliency.
Community efforts to secure Kubernetes
The conference also included an update from the Kubernetes Security special interest group, a group which works to keep Kubernetes secure. Coming to these conferences, I'm always impressed by how many people with full-time jobs make time to contribute to projects while also helping others who want to learn and be more involved.
The group shared updates across areas including security documents; security tooling, which includes maintaining the Common Vulnerabilities and Exposures feed and Kubernetes image-scanning projects; security self-assessments, which performs lightweight threat modeling; and security audits.
All in all, another great KubeCon + CloudNativeCon event. I'm looking forward to more security content this June at SecurityCon.
Melinda Marks is a practice director with TechTarget's Enterprise Strategy Group. She covers technologies that help organizations scale safely while adopting faster cloud-native development cycles.
Enterprise Strategy Group is a division of TechTarget. Its analysts have business relationships with technology vendors.





