Configuration management vs. asset management simplified
Configuration management and asset management are sometimes used interchangeably. While similar in certain ways, they are not the same thing. Discover where the two diverge and where they overlap.
Configuration management and asset management move in the same orbit -- the management of an organization's systems and services -- but they have different purposes and goals.
One focuses on managing the dependencies of resources and services in IT systems. The other tracks the lifecycle, ownership and value of physical and digital assets.
Despite key differences, asset management and configuration management (CM) often have significant overlap. Learn the differences between these processes, where they overlap and how to implement each.
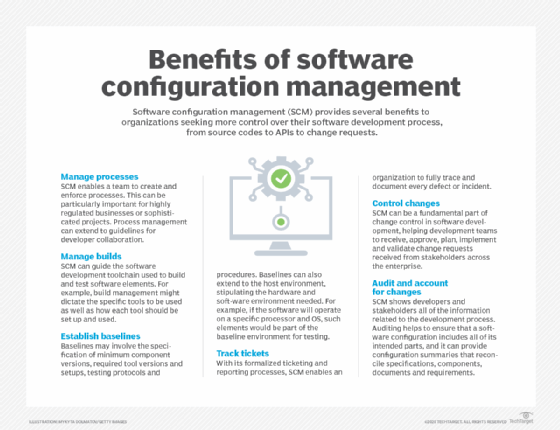
What is configuration management?
In configuration management, an item's utility, function and availability matter. Its value, brand and physical characteristics do not.
Configuration management helps administrators understand how a change to one service or resource affects other items in the enterprise. CM is concerned with what configuration items do, how they interact with each other and how they affect the broader system.
A proper change management system oversees the services and systems that support business operations throughout their lifecycle. It consists of a centralized database of configuration items and interdependencies between them, known as the configuration management database (CMDB).
Configuration items are highly controlled resources, whether they're physical or virtual. Changes made to those resources must be well-defined, documented and managed, and tightly coupled to the service they provide.
What is asset management?
Asset management is the process of monitoring, evaluating and optimizing an organization's assets, which can be tangible and physical -- laptops and servers, for example -- or digital, such as software licenses and applications.
In contrast to configuration management, the goal of IT asset management is to track and administer the asset lifecycle, not the service it provides. Asset management is not concerned with service onboarding and how an item is pushed into service.
Asset management is concerned with the value, brand and characteristics of individual items. It helps organizations maximize the use of assets over their lifecycle; understand where each asset belongs in the system; and track the cost of acquiring, maintaining and disposing of assets. Organizations place different importance on IT assets depending on the role an asset plays in the ongoing operation of the business. There is no hard-and-fast rule.
Key differences between configuration management and asset management
Configuration management ensures that every subsequent change made to an IT resource is approved, measured and managed. Asset management is more concerned with the cost of the resource and its lifespan.
Consider a scenario where IT staff must update a group of servers. A configuration management system holds records of the changes, and it documents useful information, such as the agreed length of downtime and patching schedules so that the service-level agreements are accurately maintained and measured. It also lists key contact groups and handles alert suppression on the configuration items.
IT asset management systems record details such as purchase value, vendor, purchase date, invoice number, serial number and phone number. Configuration management is rarely concerned about that asset data because it does not further the resource's intended purpose.
Another key difference between asset management and configuration management is how products and services are brought into the environment. IT administrators manage an IT service into existence through a well-defined service implementation framework. The service is fully managed throughout its life and subsequent decommission. The same cannot be said of a desktop PC. If it breaks, it goes through an asset disposal process but is not subject to change review. Its status is, however, updated in the asset management system.
An individual asset can be part of a group that provides a defined service, such as desktop or mobile services. But the loss or removal of an individual physical item from a potentially vast pool of items doesn't damage or hinder the overarching service or configuration. Conversely, a failed software upgrade that was under change control could affect the entire service.
When do configuration items and assets overlap?
Configuration management and asset management can apply to most items at the same time.
Assets can be configuration items and come under the purview of configuration management. For example, a physical server is an asset; it has a useful lifespan and is subject to accounting rules. It is also a configuration item. The IT team applies changes to it, and it is subject to the change management process. Therefore, the server comes under the purview of both asset management and configuration management.
Other items, such as certificate entries in a load balancing system, have value even though they do not physically exist. Since they have no tangible value, they are not factored into an asset management program. Yet they are important and must be documented, managed and controlled via configuration management.
Controlling configuration and asset management
Services and systems configuration items have owners. This enforces the RACI model, which stipulates that every key item has a person or group that is responsible, accountable, consulted and informed. Doing so ensures the appropriate people know what's going on and are involved in the change management process when it pertains to items under their ownership. These people can approve or deny the changes.
As an example, a newly implemented disaster recovery service has several components involving tangible items, such as the switches and network links, as well as the service. The virtual machines get asset management entries and properties. The whole system and its dependencies are configuration items. Assets can be configuration items.
With these configurations properly mapped, later system upgrades are less complicated. The IT team knows that all the dependencies are included as part of the change. As part of an upgrade, the change order will include all the configuration items and approvals.
Editor's note: This article was republished in October 2024 to improve the reader experience.
Stuart Burns is an enterprise Linux administrator at a leading company that specializes in catastrophe and disaster modeling.







