5 DevSecOps best practices to prioritize
Successful DevSecOps isn't just about secure code -- it's securing the flows of data through code, methods and tools. Review these five security tips to button up your DevOps work.
Organizations embrace DevOps because it pulls the development and operations disciplines closer together. This development model creates a responsive and efficient way to achieve continuous delivery of code to the real world -- while preserving vital checks and balances.
One of the checks that is not always managed effectively is DevOps security. Specifically, organizations often struggle to maintain appropriate levels of security when code moves swiftly from development to operations. One way to counter this vulnerability is to adopt the DevSecOps approach, which ensures that the security burden isn't left to one or two participants. Instead, security is woven into all facets of the process, relying on shared accountability from development through operations, test automation, effective communication and other techniques.
To manage security effectively in the DevOps model, consider these five important DevSecOps best practices.
1. Determine what needs to be secured
It is remarkable how many companies struggle with the basic question of what exactly should be secured. To a certain degree, the security of the code itself may not be what you need to focus on. Code is code -- unless it itself holds specific worth as intellectual property to the company, it is valueless. The data that the code deals with, however, is what differentiates an organization from its competitors. And this is where the value lies.
The focus, therefore, must be to secure the data. A well-coded service should be able to separate different data streams within itself. Any modern service that works as a walled garden in which users, once within the service, can access data that is not their own has already failed. Therefore, it is imperative that the service must isolate each data stream and protect it from other users utilizing the same underlying service. Development should ensure that this is the case through code that maintains data stream security, and operations must continuously monitor all data movements and, if necessary, throttle or block suspicious activity. Where such activity is noted, admins should immediately provide feedback to the development group to substitute secure code, thereby preventing a recurrence.
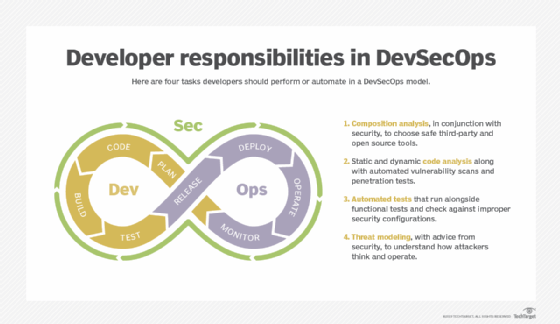
2. Maintain security between services
A microservices-based architecture will be dependent on application programming interfaces (APIs) between the various services involved. The security of the APIs -- both in how the development team writes the service code and in the external services being called -- must be maintained and continuously checked. Developers should include suitable security in all service code. The ops team must ensure that APIs are monitored to maintain secure communications at all times.
Bear in mind that APIs called by a service can change with little or no notice. As such, operations staffers must identify when and where API changes occur and take appropriate steps to maintain data security. The use of API management tools can automate and manage this, often remediating the problem in real time and minimizing the effect on the organization itself.
3. Implement the right tools
Don't assume that existing DevOps tools will manage security for you. Many either have no security functions themselves, or they focus only on the security of the workflows between the development and operations staffs. To adhere to DevSecOps best practices, look for tools that can check the security of code against known issues and, preferably, zero-day issues in real time. Also look for pen testing capabilities; these enable you to largely automate security testing. Pen testing should provide full reports and plug into the feedback loops to development so that problems can be remediated quickly.
4. Ensure security between the access device and back-end services
While the focus in DevSecOps should be on data being created and consumed, be sure to look at how the access device and its client access the back-end services. Simple challenge and response methods of security are no longer strong enough for general use. Instead, do the following:
- Adopt multifactor authentication.
- Use encryption for data streams.
- Tie user identification into a granular directory system based not only on the individual's name and role, but also on where they are, the type of connection being used and the level of defined value as to the data being accessed.
The software development team must take responsibility for putting in place those security controls. The ops team should be able to use the directory system to deny access at any stage through immediate moderation or repudiation of access.
5. Report, report, report
A key element in DevSecOps best practices is the realization that security work is never done. Code will have defects. What was secure yesterday may be insecure today. Put tools in place to monitor security at all levels along the DevOps path, and report on what is found.
Identify tools that provide feedback in a visual traffic-light manner. Also, it can be useful if a tool calculates the business impact of a security problem against a set of policies. When a problem results in a red traffic-light outcome, your process should either automatically remediate and deliver feedback to developers, or it should elevate the matter to the attention of the ops team so that they can take action.
An organization that implements DevOps must accept that it will need continuous, dynamic security in place. A compromised application can easily be replaced by spinning up a new instance, but compromised data is where the problem lies. Development and operations staff must focus on the flows of data between first- and third-party services across a modern hybrid technology platform.








