policy engine
What is a policy engine?
A policy engine is a software component that allows an organization to create, monitor and enforce rules about how network resources and the organization's data can be accessed.
The policy engine relies on a combination of network analytics and programmed rules to grant role-based permissions that take into account multiple factors, such as device type, workload label or hierarchy of need. For example, an organization might permit individuals in a user group to access specific network resources. When a user in the group tries to log onto the network, the policy engine authorizes the individual to connect to the network and access the permitted resources but denies access to anything else.
A policy engine can control various types of access behavior. For example, it might allow or exclude a range of IP addresses, specify the ports and protocols that network traffic can use, or apply rules that are specific to inbound or outbound traffic.
The criteria that the policy engine uses when evaluating access requests depends on how the network policies have been defined. Policy definitions are based on the organization's specific circumstances, constraints and resource types. However, the policy engine might also consider other information, such as threat intelligence or analytics performed from historical data.
How does a policy engine work?
A policy engine is implemented in conjunction with other components to provide a coordinated approach to protecting network resources. The exact topology depends on the type of network and its design. That said, a policy-based network commonly includes certain basic components in addition to the policy engine.
First, the network incorporates a mechanism at each access point that enforces the policies. The network might also include local storage for policy-related data or provide access to external data sources that support the policy engine. Some systems also incorporate a trust engine or comparable technology for evaluating access risks. The following figure provides an example of what such a topology might look like.
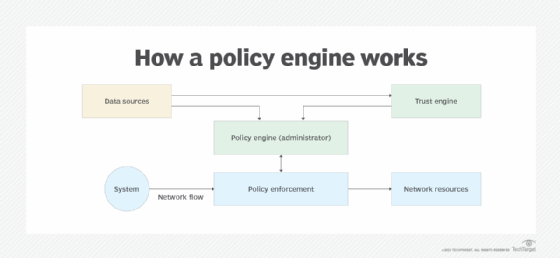
Policy enforcement occurs at the point where an outside system first attempts to access a policy-protected network. For example, an employee on a laptop might try to access a resource on the company's network. The point of entry is typically a network component such as a firewall or load balancer, which serves as the policy enforcer. The enforcer determines whether to allow or deny access based on input from the policy engine.
The policy engine lies at the heart of this topology, making all decisions about whether to permit or deny access to the network. When a request for access comes in from a network entry point, the policy engine compares that request to the defined network policies. The policy engine might also use other sources of data to determine whether to permit access, such as a trust engine or a security information and event management (SIEM) system.
When evaluating an access request, the policy engine takes into account a variety factors, such as the user requesting access, the user's device, the device's IP address, the network protocol or the target resource. From all this information, the policy engine determines whether to grant network access to that user for the specific resource.
A policy engine often incorporates an administrative component that communicates directly with the policy enforcer, executing the engine's access decisions and handling session information. In some networks, the policy administrator is a separate component from the policy engine, acting as an interface between the policy engine and policy enforcer. Like other aspects of a policy-based network, the exact topology depends on the specific implementation.
The policy engine also relies on one or more data sources to provide the information it needs to determine when to allow access to network resources. The data might be stored locally or remotely and can include a wide range of information. Not only does this include a copy of the policies themselves, but it also includes resources such as system logs, SIEM data, inventory data about users and devices, historical data for performing risk analysis, threat intelligence data, and much more.
Some networks also incorporate a trust engine or similar component for evaluating risk. The trust engine analyzes the available data and determines the riskiness of a particular connection. Some trust engines incorporate AI and other technologies to perform advanced analytics on the available data. For this reason, a trust engine must be able to access the necessary data sources to carry out its evaluations. The trust engine must also be able to communicate directly with the policy engine.
Learn about the top 3 network analytics use cases and how to reap the benefits of applying policy-as-code best practices.







