What is hardware security?
Hardware security is vulnerability protection that comes in the form of a physical device rather than software installed on a computer system's hardware. Hardware security can pertain to a device used to scan a system or monitor network traffic. Common examples include hardware firewalls and proxy servers.
Less common examples include hardware security modules (HSM) that provision cryptographic keys for critical functions such as encryption, decryption and authentication for various systems. Hardware systems can provide stronger security than software and include an additional security layer for mission-critical systems.
The term hardware security also refers to the protection of physical systems from harm. For example, equipment destruction attacks focus on computing and networked noncomputing devices, such as those found in machine-to-machine or internet of things (IoT) environments. These environments provide connectivity and communications to large numbers of hardware devices that must be protected through hardware- or software-based security.
Why hardware security matters
Hardware security is critical to modern data protection strategies and offers benefits across several industries and use cases. The most important reasons why hardware security matters are the following:
- Enhanced data security. Hardware security devices can protect sensitive information, such as customer data and a business's intellectual property, from expensive data breaches and cyberattacks. These breaches can be costly, incur substantial penalties and damage a business's reputation.
- Trustworthy protection. Hardware security often combines cryptographic processes and authentication in tamper-resistant hardware. This can create a reliable trust layer on which enterprise software or a cloud system can be built.
- Improved management efficiency. Centralized hardware security tools like HSMs can streamline the management of encryption keys and certificates, reducing complexity and human error.
- Business continuity support. Hardware security enables uninterrupted operations, securing critical systems and transactions. This minimizes downtime risks that could impact earnings and customer trust.
How to assess hardware device security
Hardware security is just as important as software security. To assess the security of a hardware device, it's necessary to consider vulnerabilities existing from its manufacture as well as other potential sources, such as running code and the device's data input/output, or I/O, on a network.
Although any device should be protected if it connects even indirectly to the internet, the stringency of that protection should match the need. For example, a system controlling the color and intensity of lights in Wi-Fi LED for a dwelling might not require much security.
In the case of more significant hardware and critical functions, the added reliability and lower number of vulnerabilities associated with hardware-based security might make it advisable. Critical infrastructure includes systems, networks and assets with continuous functions deemed necessary to ensure the security of a given nation, its economy, and the public's health and safety. Critical infrastructure security is a growing area of concern worldwide.
Types of hardware attacks
Gaining access to physical devices isn't as easy as conducting software-based attacks -- such as malware, phishing and hacking attacks -- but over time, cybercriminals have found ways to target hardware. While using a default password across multiple devices, outdated firmware and a lack of encryption are the biggest threats to hardware security, other tailored attacks are also dangerous.
There are several common types of hardware attacks.
Side-channel attack
This attack is notorious for stealing information indirectly, or via side channels. These attacks analyze the electric emissions from a computer monitor or hard drive for patterns of information and discrepancies in normal emissions. These discrepancies can include the type of information displayed on the monitor or the varying amounts of power that different hardware components use to carry out processes.
Typically, the attack will try to exfiltrate sensitive information, such as cryptographic keys, by measuring coincidental hardware emissions. A side-channel attack is also known as a sidebar or an implementation attack.
Rowhammer attack
This cyberattack exploits a bug inside dynamic RAM (DRAM) modules manufactured in 2010 and later. Repeated accessing or hammering of the memory cells inside the DRAM releases an electrical charge that flips the neighboring bits from zeros to ones and vice versa. This lets untrusted applications gain full system security privileges and even bypass security sandboxes used to mitigate malicious code from entering and infecting operating system resources.
Timing attack
This side-channel cyberattack targets cryptosystems. Cybercriminals use timing attacks to analyze the time it takes to respond to different inputs and execute cryptographic functions and algorithms.
Evil maid attack
Computer researcher Joanna Rutkowska coined the term evil maid in 2009 to signify a malicious maid trying to get her hands on electronic devices left behind in a hotel room. This attack entails obtaining physical access to unattended hardware devices, which the criminals can secretly alter to access the victim's sensitive data.
For example, a criminal might insert a USB device with device modification software into a powered-down computer or install a keylogger to record every keystroke the victim types.
Eavesdropping attack
This subtle data interception attack occurs when sensitive information, such as credit card numbers and passwords, is transferred from one device to another. Eavesdropping attacks succeed because no alerts are generated during transactions over unsecured networks. There are many types of eavesdropping attacks; a common one is a card skimmer inserted into an automated teller machine or a point-of-sale terminal where the attacker accesses the device occasionally to get a copy of its information.
Triggering fault attack
This attack is typically used by attackers who induce faults in the hardware to modify the device's normal behavior. The premise behind this attack is to target system-level security.
Counterfeit hardware attack
This is a type of supply chain attack in which unauthorized or fake devices are sold to organizations, creating opportunities for cybercriminals to use a backdoor to infiltrate these devices. For example, Cisco issued a field notice advising customers to upgrade the software on its Catalyst 2960-X and 2960-XR switches to make sure the devices aren't counterfeit.
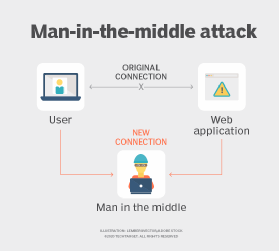
Modification attack
Cybercriminals override the restrictions on a hardware device to carry out a man-in-the-middle attack. They either inject the hardware component with malicious software or exploit existing vulnerabilities to receive and modify the data packets before sending them to the intended recipients.
Hardware security best practices
Any hardware -- from outdated computers to modern IoT devices -- can pose concerns if organizations don't follow security best practices. The following are mitigation techniques and countermeasures to follow when setting up and installing hardware:
- Investigate vendors and suppliers. The risk to hardware security starts from its inception. The production of faulty hardware components can expose vulnerable devices to outside threats. To minimize the risk of counterfeit devices, it's essential to thoroughly investigate hardware suppliers before selecting them. This can include checking the vendor's suppliers and examining the parties responsible for manufacturing and integrating individual parts. Detailed inspections regarding the security measures vendors use during all stages of hardware development are also crucial.
- Encrypt all devices. All hardware devices, including external flash storage and DRAM interfaces, should be encrypted. Hardware encryption is essential for portable devices, such as laptops and USB flash drives, to protect sensitive data stored on them. Most modern processors have built-in components to facilitate hardware encryption and decryption with little overhead on the central processing unit, but it's best to verify. Since encryption offers multiple layers of security, even if attackers get their hands on encrypted hardware, such as a hard drive, they won't be able to access data without having the credentials.
- Minimize the attack surface. Safe and proper decommissioning of unused hardware can help prevent unwanted hardware attacks. All decommissioned hardware and components, such as debug ports, should be disabled and disposed of properly. This can include disabling any universal asynchronous receiver/transmitters not used in the final hardware design process, unused Ethernet ports, programming and debugging interfaces such as Joint Test Action Group, or JTAG, ports, and unused wireless interfaces. For those components that can't be removed, companies should consider enforcing restrictions based on media access control, or MAC, address or other challenges to mitigate attacks.
- Enforce strong physical security. Companies should enforce strong access control policies in areas where hardware and physical equipment are housed. Hardware devices and peripherals shouldn't be left unattended in open areas, and devices should be secured with locked cables attached to a computer's security cable slot. Anti-tamper housing designs that make a device difficult to open without damage should also be considered.
- Use electronic security. A comprehensive hardware security plan is incomplete without proper electronic security. This can include using a secure area to store the master key to avoid tampering and key extraction. Connected devices should be protected using authenticator devices that only authorize mutual authentication based on strong cryptography to reduce the risk of counterfeit hardware. Companies should consider using tamper and trigger switches and environmental monitoring for hardware that's prone to tampering. For example, a master key uploaded to a battery-powered static RAM unit will be wiped if a tamper switch is triggered. Trigger switches can also detect light inside dark units. This locks the device whenever an attempt is made to open it.
- Provide real-time monitoring. Hardware and operating systems need real-time monitoring using cloud-based tools. These notify the security teams immediately in response to an event, minimizing the incident response time. Integrated platforms and IoT automation can also help provide an extensive overview of a company's hardware security status.
- Update firmware and upgrade old hardware. Hardware devices should be upgraded to the latest firmware to get the newest security patches. Companies should also invest in new hardware, because older hardware isn't always able to run modern software optimally and can have compatibility issues, allowing for intrusions.
- Audit regularly. Regular hardware inspections identify changes across the network and spot operational risks. Companies should conduct regular vulnerability assessments and system monitoring. For example, if a company observes a suspicious module, it should conduct an electrical analysis of the inputs and outputs after consulting with the manufacturer and in-house security experts.
Hardware security device examples
There are several examples of hardware security devices. The most common include the following:
- Secure element. An SE is a tamper-resistant chip embedded in devices like smartphones or smart cards that store data such as cryptographic keys and payment information. SEs are used in business applications requiring high trust, like mobile payments or identity verification.
- Trusted platform module. The TPM is a small chip integrated into computers or servers. It ensures secure management of encryption keys and system integrity checks. Many enterprises rely on TPMs to protect sensitive operations and maintain trust in hardware environments.
- Hardware security module. An HSM is a dedicated device that manages cryptographic keys and performs secure computations. HSMs are used by businesses to safeguard transactions, digital signatures and data security in high-stakes environments like banking or cloud services.
- Smart card. These portable devices contain embedded chips that securely store credentials or authentication data. They're commonly used for employee access control or secure logins in enterprise settings.
- USB security token. These physical devices plug into systems to authenticate users or enable secure access. USB security tokens provide an extra layer of protection for business networks and sensitive data.
IoT hardware security should be taken just as seriously as other threats in the network. Learn about various security measures to bolster IoT hardware.






