Cisco Unified Communications Manager - Hardware, Software and Clustering
This chapter excerpt covers the compatible hardware and software for Cisco Unified Communications Manager, as well as its clustering capabilities.
By: Dennis Hartmann
Service provider takeaway: Cisco Unified Communications Manager (CUCM) is the call routing and signaling component of the Cisco Unified Communications solution. This section of the chapter excerpt from the book Implementing Cisco Unified Communications Manager, Part 1 will cover the hardware, software and clustering requirements and aspects of CUCM.
Download the .pdf of the chapter here.
CUCM Release 6.0 is a complete hardware and software solution that works as a network appliance. A network appliance is a closed system that supports only Cisco-authorized applications and utilities. Goals of the appliance model are to simplify the installation and upgrade of the system and to hide the underlying operating system. An appliance-based model makes it possible for an administrator to install, implement, and manage a CUCM server without requiring knowledge of or having access to the underlying operating system.
The CUCM appliance has these features:
- Complete hardware and software solution. CUCM servers are preinstalled with all software that is required to operate, maintain, secure, and manage a server or cluster of servers (including Cisco Security Agent). CUCM is also provided as a software-only product, which may be installed on supported Cisco Media Convergence Servers (MCS) or Cisco-approved third-party server platforms.
- Appliance operating system provides ease of installation and upgrade, while also providing security and reliability.
- You can upgrade CUCM servers while they continue to process calls.
- System administration is performed via graphical user interface (GUI), command-line interface (CLI), and through documented APIs for third-party access.
- Outputs a variety of management parameters via a published interface to provide information to approved management applications, such as NetIQ Vivinet Manager, HP OpenView, and Integrated Research PROGNOSIS.
- Appliance operates with or without keyboard, mouse, and monitor (also known as headed or headless). Third-party access is allowed via documented APIs only.
- CUCM supports clustering of servers for the purpose of redundancy and load sharing. Database redundancy is provided by sharing a common database across multiple servers. Call-processing redundancy is achieved through the Call Manager Group setting, in which multiple servers are assigned to a device for the purposes of providing fault tolerance.
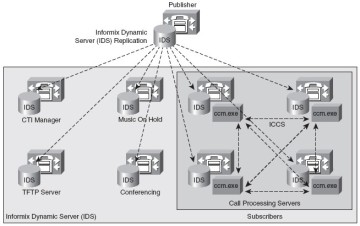
A CUCM cluster can have up to 20 servers in it. Only one publisher server is allowed in the cluster. The publisher houses the read/write copy of the database. Up to eight subscriber servers can be in the cluster, with the restriction that only four of the subscriber servers can perform active call processing. If more than four subscriber servers are used in a cluster, the additional servers are dedicated standby servers in case the active subscriber server is not available. The other 11 servers in the cluster can be responsible for various services, including TFTP and media resources (conferencing, music on hold, transcoding).
CUCM Cluster
Clustering allows the network to scale to several thousands of endpoints, provides redundancy in case of network or server failure, and provides a central point of administration. Figure 1-5 displays a Publisher database synchronizing database components to all the other servers in the cluster. The servers running the CCM.exe process are performing call processing, and the other servers are taking on special roles described in later chapters of this book. CUCM clustering creates scalability by segregating processes to other machines, which increases performance.
Device settings are stored in the IBM IDS database. The database is the repository for service parameters, features, device configurations, and dial plan configurations.
The database replicates nearly all configuration information in a hub-and-spoke topology (one publisher, many subscribers). CUCM nodes also use a second communication method to replicate runtime data using a mesh topology. (Every node updates every other node.) A mesh topology of information sharing provides dynamic registration and active call information that changes much more frequently than database changes. Real-time mesh replication is used to communicate newly registered phones, gateways, and digital signal processor (DSP) resources, guaranteeing optimum call routing.
Cisco 7800 Series Media Convergence Servers
Although it is possible for CUCM to run on most computers, Cisco supports CUCM running only on Cisco-approved hardware that they will support. The minimum hardware requirements for CUCM Release 6.0 are as follows:
- 2-GHz processor
- 2 GB RAM
- 72-GB hard disk
Minimum requirements for CUCM 6 are the same as for Cisco Unified CallManager
Version 5, but only specific MCS models are approved.
The 7800 series servers are available in the --H or --I variants. --H stands for Hewlett-Packard, and --I stands for IBM server platforms. The 7825 server is a 19-inch or 23-inch rackmountable server that provides a single SATA hard drive and one power supply. The 7835 server improves reliability and performance by including hot-swappable SCSI hard drives, hardware RAID 1 disc duplexing, and redundant power supplies. The 7845 improves reliability and performance by providing a second CPU and a backup fan assembly.
You can find the most detailed, current Cisco hardware specifications at
https://www.cisco.com/en/US/products/hw/voiceapp/ps378/prod_brochure0900aecd8062a4f9.html.
CUCM must be installed on a server that meets Cisco configuration standards. Cisco actively collaborates with two server hardware manufacturers to meet this requirement: Hewlett-Packard (HP) and IBM. You can find additional information at the following sites:
- Cisco-approved IBM server solutions: https://www.cisco.com/en/US/products/hw/voiceapp/ps378/prod_brochure0900aecd80091615.html
- Cisco-approved HP server solutions: https://www.cisco.com/en/US/products/hw/voiceapp/ps378/prod_brochure09186a0080107d79.html
Cisco UC Operating System
The CUCM operating system is based on Red Hat Linux. Operating system and application updates are provided by Cisco through patches that are digitally signed by Cisco. Unsupported software and applications (not digitally signed by Cisco) cannot be uploaded or installed into the system.
Root access to the file system is not permitted. The operating system has been hardened by disabling all unnecessary accounts and services. There is also no access to native operating system debug interfaces. Traces, alarms, and performance counters can be enabled and monitored through the CUCM GUI. Some files and directories are accessible through the Cisco CLI and GUI for maintenance purposes.
Remote-access support allows Cisco Technical Assistance Center (TAC) engineers to remotely access the CUCM server for a restricted time interval. Remote-access support can be enabled in CUCM serviceability tools.
The IBM IDS is the database for the Cisco UC applications. The IDS database installation and configuration is scripted into the CUCM installation DVDs. No UNIX or IBM IDS database knowledge is required to configure and operate CUCM.
Cisco Secure Agent is included with the appliance to provide protection against known and unknown attacks. Cisco Secure Agent is a host-based intrusion prevention system (HIPS).
A DHCP server is integrated into CUCM to provide IP telephony devices with their IP addressing requirements.
The Cisco UC operating system is also used for these Cisco UC applications:
- Cisco Emergency Responder 2.0
- Unity Connection 2.0
- Cisco Unified Presence 6.0
Cisco UC Database
The data in the CUCM database is divided into two types, as described in the sections that follow.
Static Configuration Data
Static configuration data is created as part of the configuration of the CUCM cluster. Read/ write access to this data is provided for the publisher only. Subscribers provide only readonly access to this data. If the publisher becomes unavailable, the subscriber data can be used to process calls, but it cannot be modified. Database replication is unidirectional, from the publisher to the subscribers. Only CDRs and CMRs are replicated from the subscriber servers to the publisher. All other configuration information is downloaded from the publisher.
User-Facing Features
You have learned that the publisher is the only server with a read-write copy of the database, and all configuration changes should be made on the publisher. These changes are then replicated downstream to the subscribers. This model represents a single point of failure from the perspective of moves, adds, and changes (MAC). The problem is further exacerbated because the publisher was the only server in the cluster responsible for call-forwarding changes, extension mobility logins, and message-waiting indicators before CUCM 6.0.
CUCM 6.0 treats a portion of the database as dynamic configuration data. Read/write access to dynamic configuration data is provided on all servers, allowing certain information to be modified if the publisher server is unavailable. The dynamic information that can be changed during a publisher outage is known as user-facing features (UFF). UFF data is replicated from the subscriber servers where the change was initiated to all other subscriber servers in the CUCM cluster.
Examples of UFFs include the following:
- Call Forward All (CFA)
- Message Waiting Indication (MWI)
- Privacy, Enable/Disable
- Do Not Disturb, Enable/Disable (DND)
- Extension Mobility Login (EM)
- Hunt Group Login Status
- Monitor (future use)
- Device Mobility
- CTI CAPF Status (Computer Telephony Integration, Certificate Authority Proxy Function)
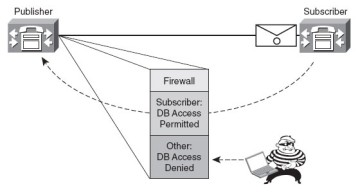
Database Access Control
Database access is secured using the embedded Red Hat, iptables dynamic firewall and a database security password. The procedure to allow new subscribers to access the database on the publisher is as follows:
Step 1 Add the subscriber to the publisher database using CUCM Administration.
Step 2 During installation of the subscriber, enter the same database security password that was entered during installation of the publisher. After this configuration, the following process occurs to replicate the database from the publisher to the newly added subscriber:
After this configuration, the following process occurs to replicate the database from the publisher to the newly added subscriber:
1. The subscriber attempts to establish a connection to the publisher database using the database management channel.
2. The publisher verifies the subscriber's authenticity and adds the subscriber's IP address to its dynamic firewall (iptables).
3. The subscriber is allowed to access the publisher database.
4. The database content is replicated from the publisher to the subscriber.
Figure 1-6 illustrates the iptables firewall allowing subscriber access to the publisher database.
You can find CUCM 6.0 TCP and UDP port usage information at https://www.cisco.com/en/
US/docs/voice_ip_comm/cucm/port/6_0/60plrev1.pdf.
![]()
![]() Implementing Cisco Unified Communications Manager, Part 1
Implementing Cisco Unified Communications Manager, Part 1
![]() Cisco Unified Communications Manager Architecture Introduction
Cisco Unified Communications Manager Architecture Introduction
![]() CUCM Overview
CUCM Overview
![]() CUCM Hardware, Software, and Clustering
CUCM Hardware, Software, and Clustering
![]() CUCM Licensing
CUCM Licensing
![]() Summary
Summary
![]() CUCM Review Quiz
CUCM Review Quiz
Reproduced from the book Implementing Cisco Unified Communications Manager, Part 1. Copyright 2008, Cisco Systems, Inc.. Reproduced by permission of Pearson Education, Inc., 800 East 96th Street, Indianapolis, IN 46240.