Patch management vs. vulnerability management: Key differences
Although patch and vulnerability management are intertwined, they differ in critical ways. It's important to have distinct tools and processes to execute both effectively.
You might think if your IT organization is doing patch management, you're covering the bases when it comes to good security hygiene. But there is more at stake, and experts say it is important for IT to go a step further and implement vulnerability management.
Why? Data breaches continue to increase, and it takes an average of 277 days for security teams to identify and contain one, according to the "Cost of a Data Breach Report 2023" from IBM and Ponemon Institute.
Further, most vulnerability management strategies are not mature, according to another Ponemon report titled "Cost and Consequences of Gaps in Vulnerability Response." Nearly 60% of cyberattack victims said installing an available patch would have prevented their breach, and 39% said they knew about a vulnerability before an attack occurred -- but never fixed it.
Also troubling is that 37% of the victims of cyberattacks said they never scan their networks and systems to see what they need to patch, according to the report.
Patch management is just one part of vulnerability management. It is intended to fix bugs and security holes in software by installing patches that are typically issued by software vendors. In contrast, vulnerability management provides the big picture through a comprehensive process for identifying vulnerabilities.
Here's a deep dive into their differences, the important places they overlap, and software options for automating them.
What is vulnerability management?
Vulnerability management is the process of managing the full, end-to-end lifecycle of security vulnerabilities from discovery to prioritization to remediation -- where a vulnerability is eliminated or mitigated to such a point that it poses minimal risk, said Mehul Revankar, former vice president of vulnerability management, detection and response (VMDR) at Qualys, a provider of security and compliance software.
One Qualys customer, insurance powerhouse Aflac, operates in a highly regulated industry, which means it has more than 50,000 global assets that must be scanned for vulnerabilities every week. Aflac officials have to demonstrate to regulators that remediation work has been completed correctly.
By using Qualys's VMDR software to scan its assets for vulnerabilities, Aflac met regulatory requirements, cut key reporting tasks from weeks to minutes and identified hidden vulnerabilities, according to Revankar. It also reduced vulnerabilities by more than 55% to 80,000.
With vulnerability management software, IT can scan all the machines on a network, whether desktops, servers or endpoint devices, and get back a report listing the known vulnerabilities, typically in order of criticality from high to low, according to Joshua Skeens, chief operating officer at Logically, a managed service provider (MSP).
From there, IT can perform discovery on those vulnerabilities and determine what they mean to the organization's environment. "You may have a machine with a vulnerability, but because of where you have it on the network it doesn't necessarily pertain to you," he said.
Many of today's vulnerability assessment tools offer sufficient coverage and detection capabilities, but those are no longer the biggest challenges, according to Sandeep Potdar, senior director of product management, VMDR at Qualys.
"Smart prioritization is," he said. "So many vulnerabilities are disclosed daily that no one can patch all of them."
What is patch management?
Often executed in specialized software, patch management is the process of identifying, acquiring, testing and installing software patches, or code changes, on a computing device. A patch is meant to fix bugs, address security issues or add new features.
Patching is about plugging a security hole or applying a fix to software, said Matthew Hodson, co-founder and CIO of Valeo Networks, another MSP. In contrast, he said, "vulnerability management is the continual process of discovering, prioritizing, and then reporting and remediating a security vulnerability."
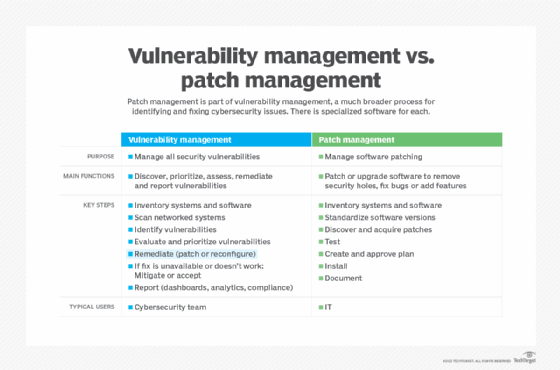
Similarities between patch management and vulnerability management
Vulnerability management and patch management are similar in that they are deeply intertwined and require IT and security teams to closely collaborate to achieve their respective goals, said Dave Gruber, a senior analyst at TechTarget's Enterprise Strategy Group. Both require a comprehensive inventory of the hardware assets being used, the software running on them and their configuration details.
While vulnerability assessment tools and patch management tools typically operate independently and are deployed and managed by different people, they support common workflows, notably in risk assessment, prioritization, and mitigation of vulnerabilities, Gruber said.
Timely patch management is critically important because more than 90% of exploitations occur after the patch for a vulnerability has been released, Skeens said.
"If you're not quickly and frequently patching, you remain highly exposed," he said, adding that in today's landscape, he wouldn't run a business without both patch and vulnerability management.
With both approaches at their disposal, IT professionals sometimes have to decide which one is best for solving a given problem. For example, they could go to the software vendor to download and apply a patch to close a security gap, or they could close or limit access to the system using network access control or role-based access control (RBAC) -- a vulnerability management approach.
Key differences between patch management and vulnerability management
Vulnerability management is designed to unveil risks and prioritize them based on the level of severity, whereas patch management assists in remediating risks by upgrading software to the most recent versions, according to Eran Livne, director of product management for endpoint remediation at Qualys.
"In some cases, the upgrade will solve the security risk, but in other cases, it will only be partially solved, with constant monitoring or additional security measures needed," Livne said.
A patch management system will not be able to tell you if there's a vulnerability in a piece of software, but the vulnerability management system will, according to Skeens. A patch management system will also notify IT that it is running three versions behind on a software system and needs to update it, he said.
Where they overlap is in using a patch management system to implement patches to address issues that the vulnerability management tool identified, he said.
"You're not typically going to find a vulnerability management system that's all-in-one, meaning it won't patch the systems for you, only report on what it found," he said. "Then you need to leverage a patch management system to apply the patches."
This is why it is important to have a strong patch management process. "If you find 40 vulnerabilities, you need to have a process to determine which you apply first and then what machines do you apply [the patches] to," Skeens said.
The role of AI in patch management and vulnerability management
As is true of almost every segment of IT, AI is bringing significant changes to both disciplines.
AI is helping, or ready to help with detection, automation, prioritization, and remediation, according to Gabe Knuth, a senior analyst at Enterprise Strategy Group.
"For example, AI can help determine the relative priorities of each vulnerability or patch due to factors like severity, exploitability and potential impact on a specific organization," Knuth said. "Many customers have used AI to develop or enhance risk-scoring features that use incoming information on vulnerabilities combined with real-time data from the customer environment that indicates overall risk of a given vulnerability."
AI will also make it easier for multiple data sources to be used to detect vulnerabilities and anomalies more effectively, he added. "This is a challenge for organizations that operate the security and endpoint management teams separately. Each has different tools that monitor for different things, and the teams don't necessarily share information with one another."
The good news is these teams are being consolidated and AI can help accelerate that, Knuth said. In fact, 55% of organizations have completely consolidated the teams responsible for endpoint management and security, and another 36% have consolidated to some degree, according to Enterprise Strategy Group research.
Despite this convergence, Knuth said customers aren't likely to hand over the keys and let AI features automatically fix everything. "But there are areas like super-critical patches that must be deployed, or low-touch, low-impact patches that can be automatically deployed with low risk of disrupting the end-user experience."
For its part, Qualys is bullish on incorporating AI in vulnerability management for more informed decision-making, responding to threats more effectively, and ultimately, strengthening an organization's overall security posture.
"AI can significantly enhance risk-based vulnerability management by introducing predictive, prescriptive and behavioral analytics to forecast potential future vulnerabilities based on current trends, threat intelligence and historical data," Potdar said. "By anticipating upcoming risks, organizations can proactively implement preventive measures to mitigate these vulnerabilities before they can be exploited by attackers."
AI can also add more contextual insights on vulnerabilities by monitoring them continuously, correlating them with other security events, such as intrusion attempts, malware infections, and data breaches, and intelligently routing and responding in real time by automating the deployment of patches, he said.
Best practices for vulnerability and patch management
There is no silver bullet when it comes to vulnerability management and patch management. "However, with significant product innovations and workflows, organizations can now follow modern best practices to significantly reduce security risk across their environment," Livne said.
They include the following:
- Implement patch management in tandem with vulnerability management. The two must work together.
- Understand that vulnerability and patch management are very much intertwined. Both must be overseen by the security team that is responsible for end-to-end remediation of vulnerabilities.
- Use the same product to detect, prioritize and remediate a vulnerability. This reduces the manual work required and allows both the IT and security teams to focus on the fix itself, Livne said.
- Scan daily. Ideally, the process will employ automated software agents to enable real-time visibility into an organization's vulnerabilities.
- Perform remote unauthenticated vulnerability scans. Doing so will help an organization understand an attacker's view of the network.
- Prioritize vulnerabilities. When pulling reports, first list the vulnerabilities that are known to be actively exploited by malware, ransomware groups, threat actors, etc.
- Patch high-risk vulnerabilities. Address high-risk and severe vulnerabilities first, especially on the perimeter, and in 48 hours or less.
- Optimize patch deployment. Automate patching of applications that introduce the most vulnerabilities to an environment and those that are not mission-critical.
- Work with security teams to create smart automation. Security teams should give their IT counterparts a list of top products that are constantly introducing new vulnerabilities. IT's role is to identify the products on the list that will introduce minimal operational risk if patched automatically. Together, the two teams should create a policy that ensures that every time a new patch is released to those selected products, it will be deployed automatically and fix the vulnerability proactively -- even before a vulnerability scan has been run, Livne said.
For organizations to achieve success in their security posture, they must recognize that vulnerability management and patch management practices have similarities and complement one another, but ultimately, are different, Livne said. "One cannot and does not supplement the other. They are two pieces to a whole process."
Esther Shein is a veteran freelance writer specializing in technology and business. A former senior writer at eWeek, she writes news, features, case studies and custom content.