
Dmitri Stalnuhhin - Fotolia
Microsoft Office Trust Center settings that help stop malware
The Trust Center in Microsoft's Office suite has some important and useful settings to prevent users from opening files infected with malware and viruses, but admins need to know about and enable them.
Microsoft Office files such as Excel, Word and PowerPoint are easy vehicles for hackers because workers use them many times a day and often don't think before opening them. Microsoft Office Trust Center settings include security features to help prevent these attacks, but IT professionals must be familiar with them to reap the benefits.
The Trust Center is found in the Options menu of Microsoft Office applications, including Outlook, Word, Excel and PowerPoint. In some cases, the Trust Center's options and features are a little different in Outlook than in the other Office applications, and there are some differences between those in Office 2010 and 2013
To get to the Trust Center, go to the File tab and select Options. This is also where admins can control Add-Ins. Select Trust Center from the left hand menu, then click the Trust Center Settings button to see the Trust Center controls.
Trust Center settings and options
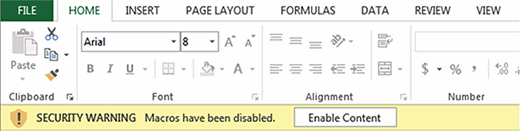
Admins can enable and configure Trust Center settings and features such as Protected View and macro settings for Outlook, Excel, Word, PowerPoint and even OneNote, but tighter security settings are more obnoxious for users. For example, when an admin configures Excel to "disable all macros with notification," users receive a security warning that looks like the example below. This warning lets users know there are macros in the file, which are not always obvious, and users can enable them -- if the file is from a known source -- and proceed.
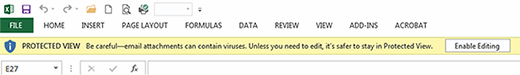
Protected View is a security feature in the Trust Center that allows admins a number of options to prevent users from opening harmful files. Protected View is like an isolated environment where admins can push a file of questionable origin so users can view its contents before editing or saving it. This keeps any malicious content from affecting the rest of the network
Protected View settings in both Office 2010 and 2013 have three options: "enable Protected View for files originating from the Internet," "enable Protected View for files located in potentially unsafe locations," and "enable Protected View for Outlook attachments." When enabled, these settings send users warnings that the files they're trying to open are forced into Protected View:
Office 2010 allowed Data Execution Prevention mode to be disabled, but that feature was removed in Office 2013. There are ways to disable it in Office 2013, but I highly recommend that it not be disabled.
Options for Add-ins
Through the Trust Center, Office security allows administrators to disable certain Add-Ins:
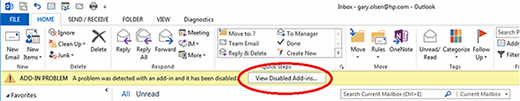
Here, Office detected a problem with an Add-in and disabled it, but users can click the button to enable the Add-in. Administrators can also use this information to determine if the problem Add-in should be disabled permanently.
Select Add-Ins from the Options menu to configure them. The dialog box displays information about Add-ins, including a list of disabled application Add-ins:
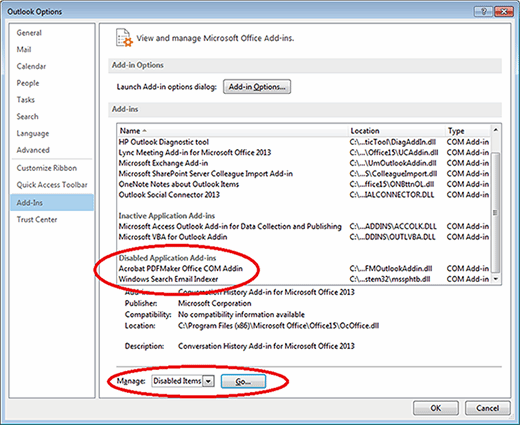
In the Manage section at the bottom of the screen, select Disabled Items from the drop down menu and click Go to bring up a dialog box to enable or disable Add-ins. Note that this does not add the Add-Ins, but merely enables or disables them.
Trusted Locations, Publishers and Documents
Trusted Locations, Trusted Publishers and Trusted Documents let admins customize the permissions for sources that deliver documents to users. This allows files from trusted sites to be excluded from Trust center settings for options such as Protected View, Active-X control, macros and more. For instance, if "Allow documents on a network to be trusted" is enabled under the Trusted Documents option, documents will open without any security prompts.
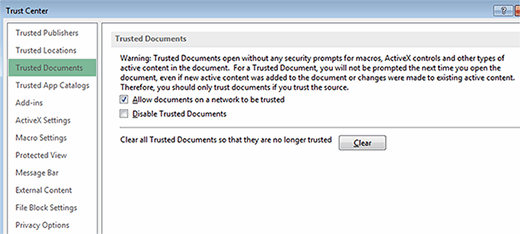
But the key phrase here is "you should only trust documents if you trust the source." Again this is a way to minimize user frustration for files that have little chance of being infected.
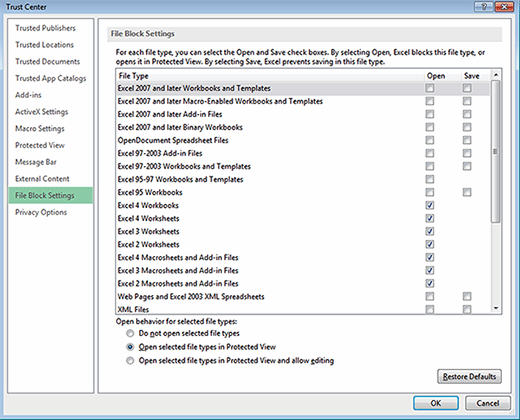
Another option is File Block settings, which allow very granular control over restrictions on the file type, as well as whether users can open it, open it in Protected View, or open and edit it in Protected View. In the example shown here, Excel can open certain versions of Excel files in Protected View, but users cannot edit them. The three options at the bottom of the dialog box provide admins flexibility on how to treat these files: Selecting the Open check box by each file means the file block action takes place when a user opens the file, and selecting the Save box restricts saving the file.
Admins can configure Office features on a company-wide basis using the Group Policy Administrative Template files and Office Customization Tool files for Office 2013 and 2010. These tools -- together with the understanding of what each Trust Center setting can do -- help admins protect the network from Office documents that could endanger corporate and employee assets.







