Microsoft Office 2013 crackable, so look to Office password recovery
Microsoft Office 2013 may have improved protection, but third-party tools have already cracked passwords. See how to use Office password recovery.
You've probably heard the analogy likening IT security to an arms race. Hackers always seem to be a few steps ahead of enterprise administrators when it comes to security. Well, bad guys aren't the only entrants in this race. There are legitimate researchers and vendors with the same abilities. Case in point: Microsoft Office 2013 passwords were broken by the long-time password pros at Elcomsoft -- before the product even shipped. If you're in charge of enterprise security for Windows desktops and related systems, this needs to be on your radar.
What's the big deal, you say? Well, Microsoft Office 2013 has a revamped password-protection scheme presumably employing stronger hashes and encryption keys. But Elcomsoft has found flaws in the implementation that allows its Advanced Office Password Recovery and Elcomsoft Distributed Password Recovery tools to "crack" these passwords instantly (for write-protected files) or via brute force in a relatively short period of time (for opening-protected files).
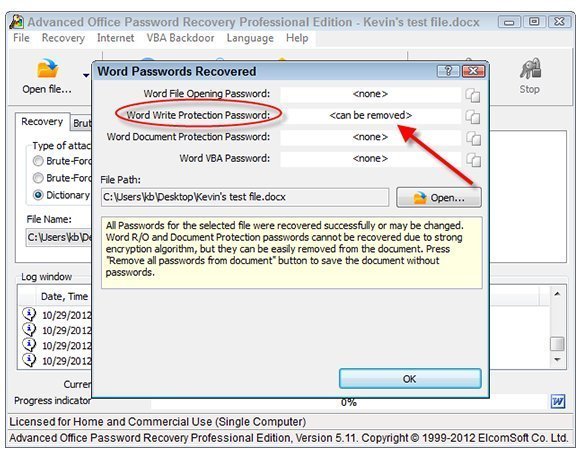
Figure 1. Using Elcomsoft's Advanced Office Password Recovery to crack a password-protected Office 2013 Word document.
No Office 2013-generated file is immune. Passwords in business applications such as Access, Excel, PowerPoint, Project and Word are all fair game. Advanced Office Password Recovery is shown in Figure 1.
In other words, if an executive or someone in marketing or legal is touting how they're doing their part to protect sensitive information by adding passwords to their Office 2013 files, it's merely for show. OK, not everyone who comes across a password-protected Office 2013 file is going to have the means to crack it immediately.
Regardless, it's like the unencrypted laptop that gets lost or stolen -- you'll never really know if the data is safe. In many cases, your organization may be held liable by breach-notification laws if you cannot prove that sensitive information was adequately protected.
There's certainly an upside to password flaws in Microsoft Office. We've all been there. Someone sends us a Word document or Excel spreadsheet that they're expecting us to open and edit, but one of those pesky (and often inadvertent) passwords is getting in the way. The original person who sent it is not available or can't remember the password, and you need to move forward. Either way, these are the perfect scenarios for using password-cracking tools such as these from Elcomsoft.
These tools can be used in another positive way -- for security testing. Cracking sensitive Office files can certainly help build the case that better security is needed at the desktop. For example, a human resources manager's unencrypted laptop housing sensitive Word documents with password "protection" creates the prime opportunity to demonstrate that business information is at risk. All it takes is an unencrypted laptop or physically unsecured desktop to create a data-breach scenario.
More on Microsoft Office
What we currently know about Office 2013
Microsoft to release Office 2013 early, but does IT care?
Office Web Apps becoming more like desktop apps
How to crack passwords in Windows 7
Microsoft Office 365: One size doesn't fit all IT shops
Consider these third-party Windows desktop management tools
It does appear that Microsoft has made good strides in providing security controls for Office 2013. For example, its file password key escrow and digital signature capabilities look like solid, enterprise-grade solutions. For now, though, I suspect that we'll continue down the business-as-usual path of putting weak passwords on documents and continuing to store them on unsecured workstations. The cycle of hacking and breaches will continue.
Given all the complexity in any given enterprise network, I still believe that if you want to protect sensitive files, then start doing so at a higher level. The vendors will say, "Protect the data," but talk is cheap.
All you may need for now are two basic controls: Full disk encryption on workstations and proper network share and file permissions may be all you need for now.
Familiarizing users with the proper approaches for handling sensitive files is also good, but it only goes so far. It's certainly easier said than done -- especially when you're on my side of the equation -- but we're going to have to get past our current "just slap a password on it" mentality if we're ever going to truly secure the Windows enterprise.







