
Getty Images/iStockphoto
How to fix Windows 11 when Secure Boot and TPM don't work
When organizations consider upgrading to Windows 11, they'll encounter several unique requirements, including TPM 2.0, UEFI and Secure Boot. Learn how to handle these requirements.
Some of the most common causes for Windows 11 upgrade failure are incompatible hardware, most likely CPU -- or firmware -- Unified Extensible Firmware Interface (UEFI), Secure Boot or Trusted Platform Module (TPM).
As a desktop administrator, you need to know what UEFI is and understand the importance of Secure Boot and TPM. This will help you support Windows 11 desktops better, understand why these components cause Windows 11 installation to fail and learn workarounds to install Windows 11.
Windows 11 and Secure Boot requirements
For important context, you should keep Windows 11 requirements in mind, including but not limited to TPM and UEFI requirements.
You can use the PC Health Check tool included in Windows 10 to determine Windows 11 compatibility for existing devices. Failure to install Windows 11 is probably due to incompatibility with system requirements, which include the following:
- approved CPU
- TPM 2.0 enabled
- 4 GB of RAM
- 64 GB of storage or hard disk
- UEFI firmware
- internet connectivity
- Windows 10 version 2004 or later
Some of these requirements are very straightforward, such as internet connectivity and the specified version of Windows 10, but the requirements for UEFI and TPM come with more questions.
What's the difference between BIOS and UEFI
The Windows desktop BIOS provides a low-level ability for OSes and applications to communicate with hardware such as the CPU, disk drives and network adapters. BIOS provides hardware initialization during boot and was created with the first IBM compatible PCs in the 1970s. While BIOS was originally stored in ROM chips, it eventually moved to flash memory to enable updates and features required for new hardware.
Pressing F1, F2 or F12 -- depending on the manufacturer -- will bring up a management program that administrators still refer to as "The BIOS." This will happen before Windows starts up. The BIOS program lets users configure hardware by enabling certain boot features, virtualization, security features, hard drive testing and more (see Figure 1).
BIOS only has 1 MB executable space to start devices such as hard disks, USB drives, displays, ports and other controllers. New hardware devices are beyond the scope of the original BIOS design, making booting slow and inefficient. In addition, BIOS allowed any software with a bootloader to boot up the PC. Any skilled engineer could write this so it could take over the PC.
While these limitations were known for decades, it took until 2007 for OEMs to agree to use UEFI as a replacement for BIOS. While Microsoft supported the specification as early as Windows 8, it wasn't required until Windows 11, even though peripherals such as disk drives might require UEFI.
UEFI has several significant features, including the following:
- UEFI stores code in non-volatile memory, which could be RAM, a file on a hard drive or even a network share. Note that the EFI folder on a Windows PC, located in the \Windows\Boot\EFI directory structure, contains .efi and .dll files, among others required by the hardware.
- UEFI supports the Global Partition Table, which supports up to an 18 exabyte hard disk for 64-bit systems. BIOS, on the other hand, only supports disk size up to 2.2 TB, which is also a function of a 32-bit system. Windows now only runs on 64-bit systems to take advantage of UEFI and larger capacity storage devices and has a practical limit of 16 TB disks.
- UEFI contains a feature called Secure Boot. Secure Boot limits a PC to boot only a specific OS.
What are Secure Boot and the Trusted Platform Module used for?
Secure Boot and TPM are frequently used interchangeably, especially when viewing diagnostic tools and BIOS menu settings. TPM is the hardware or firmware enablement of Secure Boot features.
What is Secure Boot
Secure Boot is a security standard supported by UEFI which, through firmware enablement, an OEM or an administrator can configure to boot a trusted OS. It first became available as a feature in UEFI in 2016, about the time of Windows 8. Thus, all PCs built since then most likely support Secure Boot.
This limits the OS a PC can boot and prevents rogue boot loaders from booting to an unapproved or malicious OS to take over the machine. It also effectively lets an organization restrict PCs to only boot a desired OS. For example, one organization may restrict some PCs to running Linux and others to Windows based on applications used. Microsoft enforces Secure Boot on Windows 11 machines to enable this security feature.
To determine if a Windows installation has Secure Boot enabled, open the MSInfo32.exe or enter System Information in the Windows search bar. Look for Secure Boot State and note the status (see Figure 2).
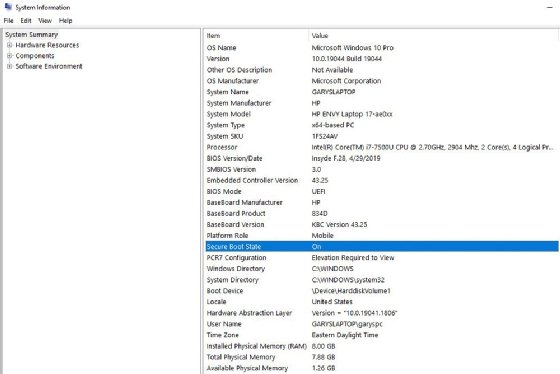
The status may be as follows:
- Unsupported. This means Secure Boot is unsupported on the PC, probably due to the PC being too old.
- On. Secure Boot is supported and enabled.
- Off. Secure Boot is supported but not enabled.

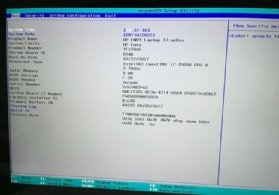
Secure Boot is enabled or disabled within the BIOS program. Depending on the OEM, this may be called Secure Boot or TPM. Consider this example on an HP Envy laptop (see Figure 3).
What is Trusted Platform Module
TPM is a chip -- or a function built into more modern CPU chips and graphics cards -- installed in the motherboards of computers to provide cryptographic services. The UEFI makes Secure Boot through TPM possible. The TPM performs functions such as managing, storing and creating the cryptographic keys that generate device signatures.
The PC checks these signatures during boot to validate that the devices, any drives and even OS software are allowed. If not, TPM prevents them from loading. This is done using public and private encryption keys stored in the hardware, and the process protects PCs from malware because an attacker can't modify those keys.
TPM 2.0 is the latest version of this technology and a requirement for Windows 11. You can verify its presence on any Windows PC by opening TPM.msc to see if it's enabled (see Figure 4).
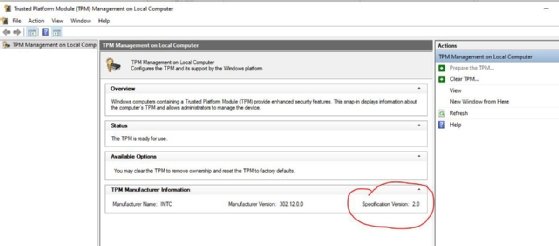
If the tool shows TPM 1.2, it won't pass Windows 11 requirements for installation. If the tool doesn't open, then TPM isn't enabled.
To enable TPM, boot the machine into the BIOS tool, navigate to the TPM option and ensure the field is enabled. This is typically under the Security settings but can be called different things by different OEMs, so look carefully and don't be afraid to research this topic.
Tricking Windows 11 into installing on an old, unsupported machine
The internet is full of well-meaning hackers who show how to install Windows 11 on an older machine. However, some of these methods are extremely unreliable because the Windows 11 OS will run via a method that Microsoft doesn't endorse or support.
Microsoft provides the ability to install Windows 11 outside the Windows Upgrade utility. You can even perform an install from Media using the Windows 11 file. However, these methods still depend on conforming to system requirements and could present continuity and security risks.
Should you bypass Windows 11 install requirements?
Bypassing the requirements isn't a big risk if you're only an enthusiast who enjoys getting an old device to load Windows when it isn't supposed to. However, this can have significant consequences if you're a desktop administrator for an enterprise or small business for the following reasons.
- Disabling secure boot in the UEFI reverts the system to the old BIOS, putting the system at risk for a malware attack.
- Ignoring Windows 11 updates and running old OS versions eliminates the Secure Boot requirement needed to run specific hardware and might leave your fleet of PCs open to malware attacks.
- Manipulating the installation, such as editing dynamic link libraries, creates significant challenges for anyone attempting to provide support for those PCs. Making these changes and supporting these hacked PCs isn't practical, even if it works. And eliminating the security protection provided by Secure Boot will result in additional security challenges.
- Adding TPM chips or updated CPUs to motherboards that don't have them might not work. This requires special skills and isn't practical to do on a large amount of PCs.
- Even if you can trick Windows 11 to run on a machine that doesn't meet system requirements, it might not provide the expected performance.
Windows 11 has important enterprise features, and you would be better off committing time and budget to install it sooner through supported means rather than bypassing the requirements. With Windows 10 mainstream end of life set for October 2025, that's plenty of time to refresh desktop hardware within a typical PC lifecycle before migrating to Windows 11.







