
Getty Images
How to edit a Domain Group Policy for a Windows desktop
When IT administrators need to edit a Group Policy at the domain level, they can download the RSAT management tool and change policies from the local Windows desktop.
In a Windows environment, administrators will occasionally need to modify group policy settings in response to evolving security or compliance requirements.
While administrators can create or modify group policy settings directly on a domain controller, best practices state that they should make such modifications from a Windows desktop instead.
Why use a Windows desktop to edit Group Policy?
There are several reasons why it is usually better to edit domain group policy from a Windows desktop rather than performing the operation directly on a domain controller.
One of the most important reasons is that domain controllers are among the most sensitive assets on a network. As such, Microsoft discourages the practice of logging onto a domain controller directly. Instead, Microsoft recommends creating secure administrative hosts.
A secure administrative host is essentially a Windows desktop that has been provisioned specifically for the purpose of performing sensitive administrative tasks. Although there is an entire laundry list of best practices surrounding secure administrative hosts, there are three best practices that are far more important than the rest.
- Administrators should never sign on to a standard desktop using a privileged account. That's because cybercriminals often seek to compromise a desktop -- usually through malware -- and use it as an initial point of entry into a network. They can then use a pass the hash attack to move from desktop to desktop until they find one on which a privileged account has been used at some point in time. From there, the attacker can harvest the credentials for the privileged account and take over the network.
- A secure administrative host should only be used for performing privileged operations -- nothing else. Casual activities such as checking email or browsing the internet could expose the desktop to online threats.
- IT admins should harden the secure administrative host to the same level as the domain controllers themselves. It makes no sense to harden a domain controller and then manage it from a less secure administrative host.
In addition to the fact that Microsoft discourages the practice of interacting with domain controllers directly, there are other reasons why editing a group policy directly on a domain controller might be impractical.
IT departments also usually configure domain controllers to run a server core configuration. This means that the domain controller does not contain a Windows GUI and therefore IT needs to manage it using PowerShell. While you can make group policy modifications through PowerShell, using a GUI-based management tool tends to be a lot easier.
Another reason why it's more practical to use a secure administrative host rather than modifying a domain controller directly is that domain controllers are often located in a data center among rows of other servers. An admin might not have physical access to the data center, or it might be difficult to locate the desired domain controller among all the other servers. Ultimately, it's just easier for an administrator to edit a group policy setting from the comfort of their own desk rather than looking for a domain controller.
Common Group Policy Object modifications
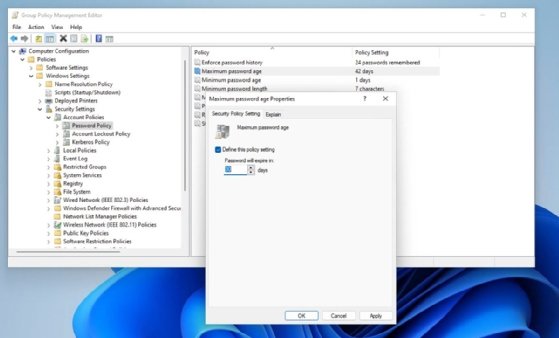
Every organization's needs are unique, and so are their Group Policy Object (GPO) requirements. However, nearly every organization modifies the Password Policy to match its internal security and authentication standards. Admins can find the password-related policy settings at Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policies. The Password Policy folder, seen in Figure 4, contains settings related to the minimum password length, complexity requirements, change frequency, and more.
How to edit Group Policies from a Windows desktop
Editing a group policy setting from a Windows desktop is a relatively easy process, though the actual steps vary slightly based on the version of Windows that is in use. The instructions presented here are based on using a domain-joined Windows 11 system.
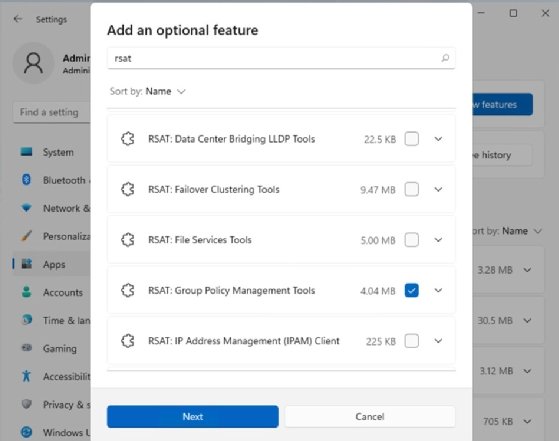
Begin by logging in using a privileged account. Before an admin can modify group policy settings, they will need to install the Remote Server Administration Tools (RSAT). To do so, open Settings, and then click on Apps, followed by Optional Features. Click the View Features button and then type RSAT into the search box. Select the checkbox corresponding to RSAT: Group Policy Management Tools, shown in Figure 1. Click Next, followed by Install to complete the installation process.
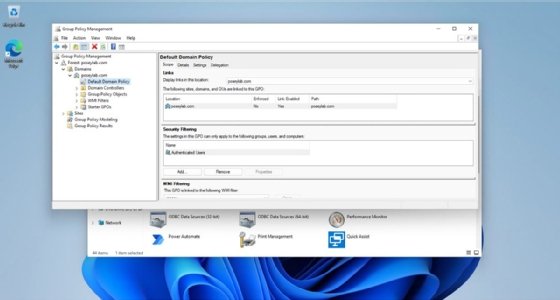
When the installation process is complete, open the Group Policy Management Tools. They are located within the Start menu's Windows Tools folder. When the console opens, navigate through the console tree to Group Policy Management | <your forest> | Domains | <your domain> | <the policy that you want to edit>. As an example, Figure 2 shows the location of the Default Domain Policy within my domain.
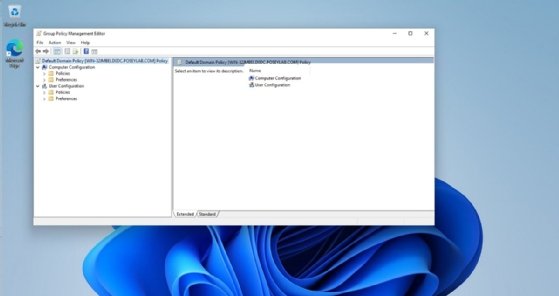
Right-click on the desired GPO and then select the Edit command from the shortcut menu. This will open the Group Policy Management Editor, which is shown in Figure 3.
Now, navigate through the console to locate the policy setting that you want to modify. Double-click on the desired policy setting, make any desired changes, and then click Apply, as shown in Figure 4.
How to apply Group Policy changes immediately
When IT modifies a group policy setting, Group Policy applies the policy changes automatically the next time a user logs in. Windows is also designed to periodically check for any available group policy updates. Windows performs this update check every 90 minutes.
However, Windows adds a random amount of time of up to 30 minutes to the 90-minute threshold. This prevents all the computers on a network from checking for policy updates at the same time. As such, domain joined systems will automatically check for GPO updates every hour and a half to two hours.
It is possible to force a PC to immediately apply any updated group policy settings. To do so, open an elevated Command Prompt window and enter the following command as shown in Figure 5:
Gpupdate /force
This will apply these policies and settings for both the desktop and the user account associated with the desktop.
Brien Posey is a 22-time Microsoft MVP and a commercial astronaut candidate. In his over 30 years in IT, he has served as a lead network engineer for the U.S. Department of Defense and as a network administrator for some of the largest insurance companies in America.







