
Getty Images
How to disable the Windows Hello feature with Intune
While Windows Hello for Business can be a helpful feature, sometimes IT will need to disable it. Learn two approaches to disabling this authentication service and when to do each.
Windows Hello provides organizations with a convenient method to authenticate in Windows, as it enables users to verify their identity by using biometric authentication or a PIN.
On top of that, Windows Hello for Business provides additional security and management capabilities, including device authentication, device configuration, certificate-based authentication and Conditional Access integration.
Maybe the best part of Windows Hello for Business is that it is seen as a phish-resistant two-factor authentication. That is, however, not always acknowledged as such. Besides that, it integrates well within a Microsoft ecosystem with a single sign-on experience for nearly all applications that are used within the organization. That includes Cloud applications and on-premises hosted applications.
Windows Hello for Business as multifactor authentication
According to the definition of multifactor cryptographic device authenticators by NIST, Windows Hello for Business can be seen as a true multifactor authentication (MFA) technology. This is because it combines "something that you have" -- such as a device with a hardware Trusted Platform Module (TPM) that contains the private key -- with "something that you know" -- a PIN to unlock the private key -- or with "something that you are" -- a fingerprint match to unlock the private key. Of course, it is important that it is configured correctly to fully comply with that definition. And all of that is pretty similar to using smart cards.
The big difference, however, is that the second factor is not portable with Windows Hello for Business. And even though portability is not part of the definition of MFA, organizations may still consider portability as an important aspect of the authentication platform. The fact that Windows Hello for Business is bound to a specific device with its own hardware TPM is not sufficient in those cases. For enhanced security, organizations could deploy a different offering that is not directly bound to the user's device. Alternatives can be based on smart cards or a secondary approval such as Cisco Duo.
Using Microsoft Intune to disable Windows Hello for Business
When organizations have determined that they don't want to use Windows Hello for Business to authenticate, it's important for IT administrators to shut this service off for their endpoints. IT can do this by disabling the Windows Hello functionality on the devices used within the organization. By doing this, IT administrators can make sure that users won't be able to set up Windows Hello for Business on their own, and the organization can use its own alternative for MFA on their devices.
No matter what the actual reason is for disabling Windows Hello for Business, when looking at Microsoft Intune, there are two different methods available to achieve that goal. The first method is to disable Windows Hello for Business by default for all Windows devices that enroll in Microsoft Intune, and the second method is to disable it only for assigned Windows devices.
Method 1: Disable Windows Hello for Business via enrollment options
The first method to disable the use of Windows Hello for Business is by using the enrollment options in Microsoft Intune. These options allow IT administrators to disable Windows Hello for Business immediately during the Intune enrollment process for Windows devices.
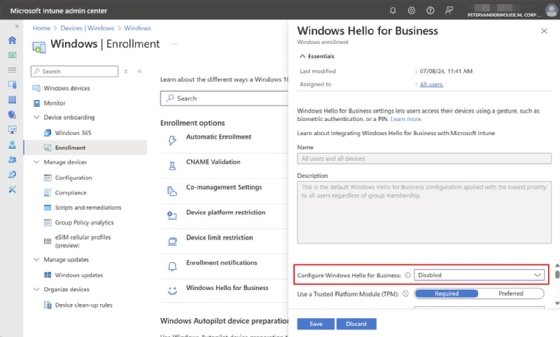
- Open the Microsoft Intune admin center portal and navigate to Devices > Windows > Enrollment > Windows Hello for Business.
- On the Windows Hello for Business blade that slides over the screen, as shown in Figure 1, select Disabled with Configure Windows Hello for Business to disable Windows Hello for Business by default and click Save.
Method 2: Disable Windows Hello for Business via an account protection policy
The second method to disable the use of Windows Hello for Business is by using an account protection profile. These account protection profiles allow IT to disable Windows Hello for Business for assigned Windows devices only. That profile contains a template with configuration settings that currently are related to Device Guard and Windows Hello for Business. All of the settings within that profile are coming straight from the Settings Catalog in Microsoft Intune. IT can also create a custom Settings Catalog profile to achieve a similar technology.
- Open the Microsoft Intune admin center portal and navigate to Endpoint security > Account protection.
- On the Endpoint security | Account protection page, click Create Profile > Windows > Account protection.
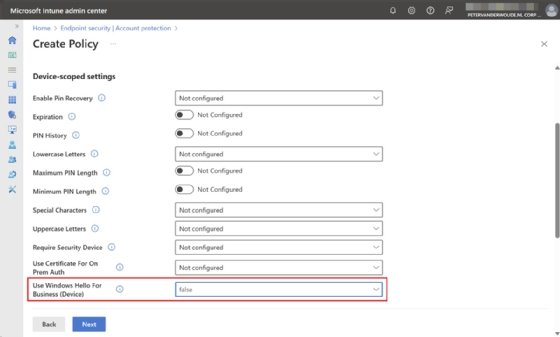
- On the Basics page, provide a unique name to distinguish the account protection profile from other similar profiles and click Next.
- On the Configuration settings page, as shown in Figure 2, scroll down to the Device-scoped settings, select false for the Use Windows Hello for Business (Device) setting to disable Windows Hello for Business for all assigned Windows devices and click Next.
- On the Scope tags page, configure the applicable scope tags and click Next.
- On the Assignments page, configure the devices that should be assigned with this Account Protection profile and click Next.
- On the Review + create page, review the configuration of the Account Protection profile and click Create.
Peter van der Woude works as a mobility consultant and knows the ins and outs of the ConfigMgr and Microsoft Intune tools. He is a Microsoft MVP and a Windows expert as well.






