Group Policy tricks to secure network endpoints
There are thousands of Group Policy settings available -- lock down your network endpoints with these favorites.
Group Policies are the primary mechanism for securing a network. While there are thousands of Group Policy settings, here are some of the best for locking down network endpoints.
Establishing portable storage control
Universal Serial Bus storage devices pose a big threat to endpoint security. These devices make it easy for users to steal data or install unauthorized software onto a network.
Although there isn't a Group Policy solution for controlling USB storage device access, there are several roundabout ways to prevent users from using these devices.
One method involves creating a custom administrative template that contains a Group Policy template, which provides access to a setting that can be used to disable a USB port. Instructions and code for creating this template can be found on Microsoft's website. If you're too intimidated to create a custom administrative template, you can download a template copy from a variety of websites.
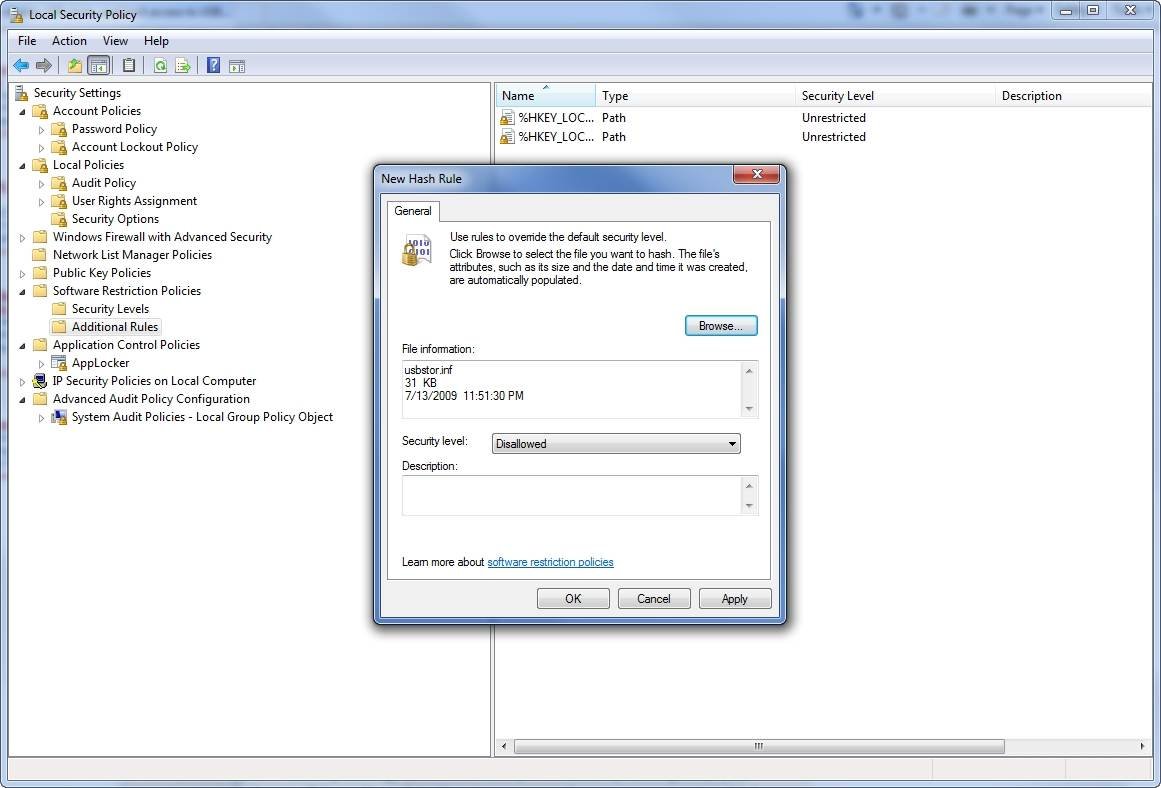
In addition, USB storage devices can be disabled with software restriction policies. When a user inserts a USB flash drive, Windows loads the driver file %SystemRoot%\Inf\USBSTOR.INF. A hash rule can be created to prohibit access to this file, as shown in Figure 1.
Although not a Group Policy-based solution, an easier technique is to use NT file system permissions to deny access to the USBSTOR.INF file.
Furthermore, third-party products such as GFI Endpoint Security can provide more control over removable storage devices than native Windows tools.
Enabling local security policy
Local security policies offer many of the same settings as network-level policies, but they are designed to protect the computer when it is not authenticated into a domain. Therefore, a computer isn't vulnerable if someone figures out how to log in locally.
These security policies are often ignored because they can't be centrally managed, which makes it difficult to keep them up to date.
Regardless, each PC on your network should contain a local security policy with the most important settings enabled. If the policy becomes outdated, the network policy settings will override the local policy settings when the user is online. When a user is not logged into the network, local security policies protect the computer. It is far better for a computer to be protected by an outdated policy than no policy at all.
Windows Mobile
Traditionally, the focus of endpoint security has been on desktops, laptops and servers. Mobile devices were often ignored because they were relatively rare (presumably due to their price) and had extremely limited capabilities. But things are much different today.
Almost everyone has smartphone or a mobile device, and these devices are more powerful than ever. This increase in computing power and device popularity has led to the widespread development of mobile applications.
As a result, an unsecured mobile device can present almost as great of a threat to network security as an unsecured laptop. If a user wants to use a mobile device to hack a network, "there's an app for that."
In addition, there have been reports of viruses being spread by mobile devices.
Group Policy settings can be used to lock down mobile devices in the same way they are used to lock down desktop systems. But the catch is not every mobile device is compatible with Group Policy-based security.
Network-level Group Policy settings can only be applied to domain members. Therefore, only the mobile devices that can be joined to a domain can be secured by group policies. Currently, only those devices running Windows Mobile 6.1 and 6.5 can be joined to a domain.
And joining a device to a domain is only half of the battle.
Group Policy settings for mobile devices are not included with Windows Server. To get the necessary administrative templates, System Center Mobile Device Manager needs to be installed. This adds about 125 group policy settings, which are accessible through the Group Policy Object Editor at Administrative Templates / Windows Mobile Settings.
Overall, given the sheer number of Group Policy settings available, you should be able to lock down endpoints in a way that achieves your security goals.
ABOUT THE AUTHOR:
Brien M. Posey, MCSE, has received Microsoft's Most Valuable Professional Award four times for his work with Windows Server, IIS and Exchange Server. He has served as CIO at a nationwide chain of hospitals and health care facilities and was once a network administrator for Fort Knox. You can visit his personal website at www.brienposey.com.