
James Thew - Fotolia
Passwordless authentication options and best practices
Organizations that want to move away from passwords for authentication should learn the best practices for implementing passwordless authentication and which factors fit them best.
Sometimes the best security offers the worst user experience and vice versa, but a corporate security policy must account for both factors.
The struggle between these two competing factors is exemplified perfectly by passwords. Strong passwords are necessary to protect data and resources, but users may have a hard time remembering all of them, they have to be changed often and there is an army of hackers working hard to steal them. Restoring forgotten passwords can take up the time of IT staff and lead to frustration for users and administrators.
A Verizon 2017 Data Breach Investigation Report stated that 81% of hacking related breaches used either stolen or weak passwords. Passwords are often better in theory than they are in practice, and enterprise organizations should consider going beyond the simple password for securing their users' devices and data.
Recent authentication technologies, including fingerprint and retina scans, and facial recognition, make it harder for thieves and more convenient for users. Gartner estimates that by 2022, about 60% of large companies and 90% of mid-size ones will be using passwordless authentication, so IT admins should be familiar with this approach to authentication. Organizations should learn what this technology does and the different passwordless authentication best practices necessary for a smooth rollout.
Passwordless authentication deployment and best practices
The central idea of passwordless authentication is to use other forms of user identification without relying on users' ability to use safe and unique passwords. Passwordless authentication is a type of multifactor authentication (MFA) that replaces the password with a different factor -- a PIN, a fingerprint, a code or something else -- that users enter in real time rather than a traditional stored PIN or password. Passwordless authentication also relies on the same cryptographic principles that the password-based authentication uses: a cryptographic public and private key pair.
Certain actions such as changing passwords, modifying account info or even requesting technical support, require a confirmation email to a trusted and verified account.
For example, a user needs to access medical records online. That user is presented with an option: Either enter a username and password or have a verification code sent to a phone number that is registered with the account.
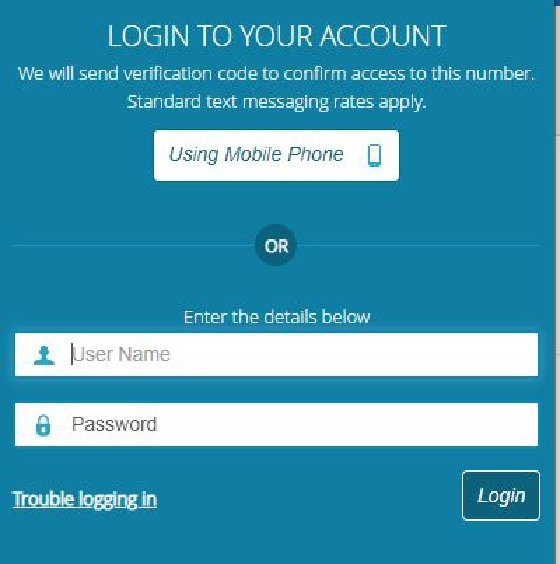
When a user selects the mobile phone option, the medical system sends an SMS text to the phone and then the user enters the code and can access the system of records.
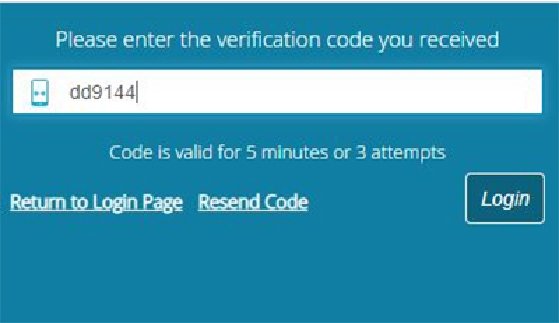
Most systems, however, will allow users to log in to their account and change the phone number if it is out of date. Note that this code has a short lifetime and can be resent if the user doesn't receive it. This way, the authentication method ensures security and the user doesn't need to remember a password.
Best practices and authentication methods for a passwordless approach
There are several options to implementing a passwordless strategy, including the following three methods.
This is a mature authentication method and is commonly used when a user forgets a password. The security platform sends a secure link via email to the user that functions as the authentication.
This is a backdoor passwordless authentication strategy, in that the user doesn't need a password -- just the link to set a new one. Thus, a user doesn't need to remember the password. Users only need to click a link with each login, essentially bypassing the password. This option is a good strategy for users that access certain applications infrequently.
SMS or phone call
This method sends a one-time code to a mobile phone via SMS (Figures 1 and 2), although most applications will also offer to send it via a phone call as well. The code is a one-time code that expires in a few minutes and can be resent if the user didn't receive it. The phone number is usually registered as a trusted part of the user's profile and would need to be updated if the phone number changes, which could cause a negative user experience.
Logged in users (Apple only)
Apple goes a step above these methods, likely because of a famous security breach years ago, when hackers were able to hack into Apple users' accounts and steal their credit card information. Apple requires users to log in with traditional credentials and then requires users to enter a code that Apple sends to a trusted Apple device. One example of a situation that requires this authentication method is Apple's technical support.
As a logged-in user, the support staff will send a code that will appear on the screen of another trusted Apple device. They could also provide the code via a phone call to a preregistered phone. If the user doesn't have another trusted Apple device (Figure 3), or if the phone number changed and it was not recorded by Apple, the reset process may take several days.
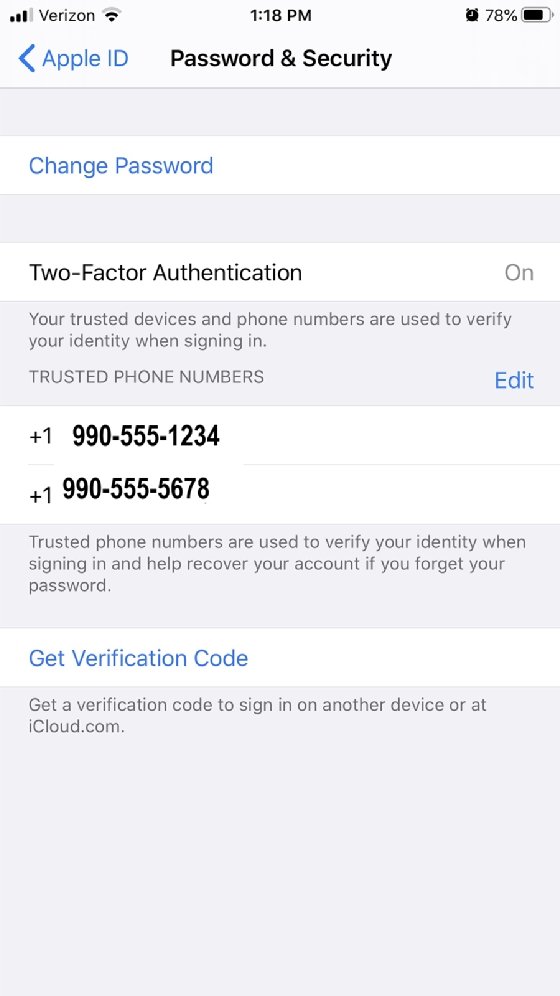
Note: Make sure users have at least two Apple devices that trust each other. Otherwise, password support issues will be difficult to resolve.
The easiest method to implement that still provides excellent security and user convenience is the SMS text strategy. The user doesn't need to enter or remember a password, no password is stored on a client device or server, and it only has a single-use lifetime of a few minutes. This option is virtually hack proof, as long as the user is the only one with access to the phone number.
Password replacement technologies
IT administrators can implement passwordless authentication for a web browser, a mobile app or physical device. There are several viable commercial products available for password replacement implementation, including the following options:
- OneLogin, which provides a suite of MFA products including customer identity and access management.
- Auth0, which is a drop-in service that allows admins to add authorization and authentication services to applications. This is a good option for organizations that develop and deploy lots of custom business applications.
- HYPR, which has products that cover mobile apps, desktop clients, cloud applications and an SDK.
- Microsoft, which offers three technologies in Windows 10 for passwordless authentication: Windows Hello for Business, the Microsoft Authenticator App and FIDO2 Security keys.
Passwordless authentication is not just another security fad; it is a simple yet powerful technology that will bridge the gap between IT's demand for secure access and the users' need for simplicity.
Organizations should consider implementing passwordless authentication as part of an MFA strategy to enhance security further. Mature passwordless authentication technologies can satisfy the needs of enterprise organizations and small to medium organizations alike.








