Handling Intel Management Engine Exploits . . . or Not!
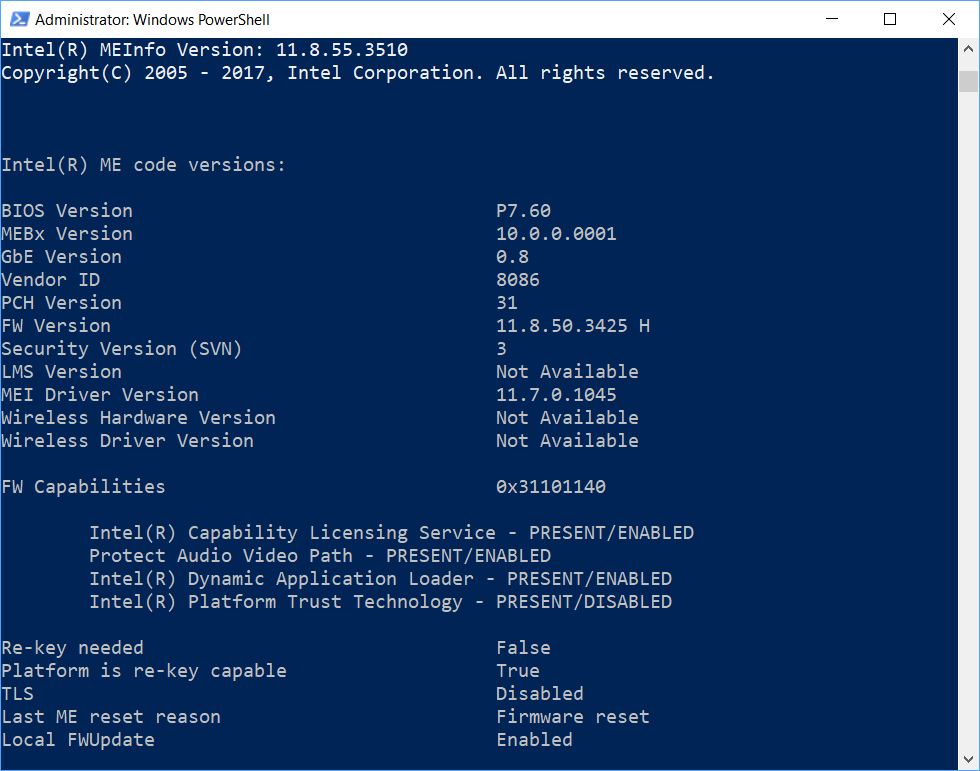
In checking over new posts at TenForums this morning, I came across information about new vulnerabilities in Intel’s Active Management Technology (AMT). The latest advisory is labelled INTEL-SA-00141. Such exploits could “allow arbitrary code execution, a partial denial of service or information disclosure.” Naturally I wanted to see if, by way of handling Intel Management Engine exploits, I could install a new firmware version. It took a while for me to figure things out. But alas, the situation for my Asrock Extreme7+ motherboard, with its Z170 chipset, is “No dice!” Here’s what’s currently resident, courtesy of Intel’s helpful meinfowin64.exe program. (This is part of the Station-Drivers download package, so here’s that package link.)
Important values here are the FW Version and MEI Driver Version.
These are 11.8.50.3425 (FW) and 11.7.0.1045 (MEI), respectively.
[Click image for full-sized view]
Requirements for Handling Intel Management Engine Exploits
Alas, as it turns out there’s an ingredient missing for my motherboard. I was able to find two versions of the CSME 11.8.55 that Intel recommends for my current firmware. Asus offered one for its Z170M-Plus mobo, modder Pacman cobbled the other together for Station-Drivers. Neither worked on my Asrock Extreme7+ motherboard, though. The installers informed me the drivers and firmware weren’t compatible with my mobo. Attempts to install those drivers manually through DevMgr also failed.
What about Asrock and Other Support Pages?
A quick visit to the driver downloads for the Extreme7+ showed no relevant updates since December of 2017 (the version supported there is 11.7.0.1045, which is what I currently have installed). Cruising the support forums there, I found no word of a new round of impending updates for my 4-year-old motherboard. At this point, all I could do was hope. One, Asrock might get off its duff and release a new set of drivers and firmware. Two, some intrepid driver/firmware modder might put something together. Frankly, I put a lot more faith in the latter, and my faith was rewarded fairly quickly, as I’m about to relate.
Naturally, that led me to Win-RAID.com, where such things happen with celerity and grace. And in fact, I found an entry there entitled Intel CSME Firmware v.11.8.55.3510 on the Intel Management Engine Drivers Firmware page. This produces a .bin file that works with the Intel Firmware update utility FWUPdL aka fwupdate.exe. The Asus version of 11.8.55.3510 drivers and firmware includes that tool, in both x86 and x64 versions, which I was able to rescue from my Recyle Bin. So here’s a link to that item, too, for would-be DIY firmware updaters: Version 11.8.55.3510.
Right now, I’m wavering on whether I should install the firmware or not, for fear of bricking my production desktop. I think I’ll do a bit more research, and reach out to the Win-RAID forums to see if anybody has successfully updated my specific Extreme7+ motherboard before proceeding. The last thing I want to do is put my primary PC out of action, in the interest of tightening security. That’s a real tough choice, for sure.
But it do get interesting sometimes, keeping up with these security vulnerabilities. And it always comes with great opportunities for learning, too.