ITGC audit checklist: 6 controls you need to address
Assess the risks to your IT operations and company infrastructure with an IT general controls audit. Download our checklist to help you remember what to include in the audit.
Audits are a regular part of corporate life, especially in the IT field. Considering the importance of IT resources for business continuity, audits ensure those resources are performing as they should. Among the audit metrics used to measure IT performance are the Control Objectives for Information and Related Technologies framework developed by ISACA, NIST Special Publication 800-34 Contingency Planning Guide for Federal Information Systems, and ITIL standards and practices for IT service management.
What does IT general controls (ITGC) mean?
Numerous systems, applications, utilities and networks constitute a typical IT infrastructure, so there are a variety of audit attributes to address. However, before embarking on a detailed integrated audit -- auditing servers or cybersecurity, for example -- an ITGC audit is a good place to start, as it provides a baseline measurement of IT infrastructure operations and capabilities. The audit should also examine the alignment between the IT organization and the business, specifically how IT supports the business and enables its many activities.
What is the purpose of an ITGC audit?
Audits are often performed with a focus on risk. Specifically, identifying potential risks, threats and vulnerabilities to IT operations, integrity of data, internal controls, automated controls and application controls are key objectives of an ITGC audit. Whether performed by internal auditors or an external audit firm, IT audit procedures are specific in their design, execution and focus on risk and operating effectiveness of the controls.
Most of the controls listed in the following sections can prevent situations that threaten data center operations and identify areas for improvement. Results of the ITGC audit, whether performed internally or by an external auditor, provide a useful risk assessment of the IT infrastructure and how it supports business operations.
ITGC audit checklist
The table below provides a sample checklist that can serve as a starting point for planning, scheduling and conducting an ITGC audit. Identifying controls to examine are among the first items to prepare in an audit.
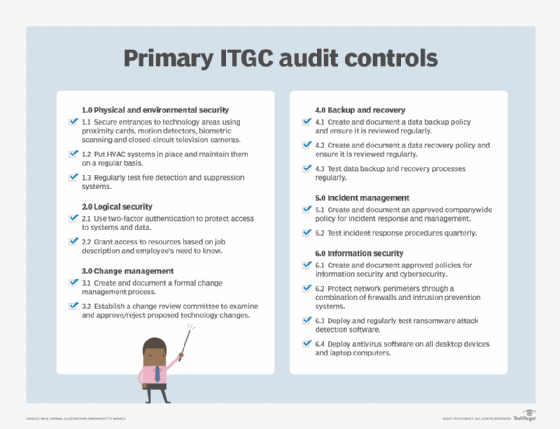
The following sections provide additional details on the ITGC audit checklist above.
Control 1. Physical and environmental security
Data centers, whether large, free-standing buildings or small rooms, must be protected from unauthorized access and unplanned environmental events that could compromise their operations. Data center access is often controlled by proximity cards, keypad access or biometric access technologies. These approaches provide single-factor and -- in more cases -- two-factor authentication to minimize the likelihood of unauthorized personnel entering the data center. Closed-circuit television cameras, typically part of a companywide physical security monitoring system, provide another layer of protection from unauthorized access.
HVAC systems provide a suitable environment for employees working in a data center. They prevent damage to electronic components by controlling the temperature and relative humidity in the data center. Any significant changes in either of these two metrics should be identified and reported to data center managers.
Fire protection systems that detect smoke, excessive heat and fire can activate audible, visual and electronic alerts of the situation and activate chemical-based fire suppression systems, such as FM-200. Overhead sprinkler systems, typically using dry pipe or wet pipe technologies, can also be activated by fire protection systems.
Examples of additional data center controls are the following:
- limiting the number of employees with card access to the server room;
- having raised floors and installing water detectors under the floors; and
- checking server room fire extinguishers quarterly.
Control 2. Logical security
Access to IT systems and services is generally provided to all employees, but not all employees need access to all resources. Access privileges are usually coordinated by HR and IT based on job responsibilities.
System resource access is granted using single-factor -- an employee ID -- or, in most cases, two-factor authentication, such as an ID and unique password. Biometric authentication -- using a thumbprint reader, for example -- is another effective way to authenticate users. Windows Active Directory is often used to authenticate users. Administrators can also use techniques such as single sign-on to provide access to multiple applications and platforms.
Examples of additional logical security controls are the following:
- providing access to system resources for new employees after they are approved by HR and an email noting that approval is received by IT;
- deleting access credentials for terminated employees within 15 minutes of notification by HR; and
- changing passwords every 90 days.
Control 3. Change management
Having a well-structured change management function, which often includes a change review committee, ensures all IT infrastructure changes are examined, tested, documented and approved before entering production. Lack of a change management function can mean deploying a system that damages the firm's reputation and potentially puts the entire organization at risk. This is especially true with patch management, which must be carefully controlled so patches perform as expected and are monitored and regularly reviewed.
Examples of additional change management controls are the following:
- segregating test and production environments, with the test environment used to validate changes and patches; and
- establishing a change management committee that reviews and approves/denies all change requests.
Control 4. Backup and recovery
Considering the amount of data that is created daily, backup and recovery have become increasingly important as they protect business processes, data, databases, applications and VMs. Options for backing up and recovering data are numerous and can be locally managed using storage servers and SANs, as well as remotely configured using managed services or a hybrid of the two. Specialized technologies, such as data deduplication, ensure that vast quantities of data can be effectively stored. Backup and recovery are key components of technology disaster recovery (DR) plans, which are essential for business continuity (BC) management and achieving organizational resilience. Admins can use numerous audit controls for backup and recovery, such as type of data backed up, frequency of backups, speed of backups, recovery point objectives and speed of recovery in an emergency.
Examples of additional backup and recovery controls are the following:
- testing data backup procedures monthly;
- testing recovery procedures quarterly; and
- testing DR plans annually.
Control 5. Incident management
Rarely does a day go by without an event that affects IT operations. Whenever such events occur, a process must identify the event, assess it and make decisions as to its mitigation and resolution. Incident response procedures are especially important with the growing threat from cybersecurity events. Regardless of the event -- be it environmental, such as a fire; physical security, such as unauthorized access; or cybersecurity, such as a ransomware attack -- incident response procedures and incident management plans must be documented and regularly exercised so that incidents can be quickly addressed and remediated.
Examples of additional incident management controls are the following:
- creating an incident management team that provides the first response to an incident;
- training on incident response for the team regularly; and
- producing daily incident activity reports for IT management.
Control 6. Information security
Information security is perhaps the most important IT general control because there are so many ways security can be breached. The media regularly reports on significant cybersecurity events, particularly involving theft of individual data records or ransomware attacks that block access to systems. The challenge is that, as new security remedies appear on the market, threat actors introduce yet more powerful attack vectors. Among the control areas most often addressed are an organization's network perimeter, desktop systems and nontechnology security issues, such as social engineering. Cybersecurity events can evolve into BC events, with the attacked firm fighting to protect its customers, business operations and reputation.
Examples of additional information security controls are the following:
- using intrusion detection and intrusion prevention systems to protect the network perimeter;
- regularly reviewing and updating firewall rules;
- deploying antivirus software on all desktop devices and company laptops;
- performing penetration testing twice a year to check for vulnerabilities; and
- prohibiting the use of personal laptop devices, unless suitably modified by IT.
Performing the ITGC audit
ITGC audits follow typical audit procedures, such as the following:
- Determine the need for an audit; review with management.
- Secure management approval for the audit.
- Gather an audit team using internal and/or external auditors.
- Prepare an audit plan, and secure its approval.
- Identify controls to be audited.
- Obtain evidence -- such as policies, procedures and screenshots of specific activities -- for examination.
- Identify interview candidates; schedule and conduct interviews.
- Schedule and conduct physical examinations of IT activities, such as a data center walkabout.
- Prepare and conduct tests of the identified controls.
- Analyze the evidence, and conduct follow-up research, if needed.
- Document audit findings and recommendations in a report.
- Present the audit report to management.
In addition to the above list, prepare an audit schedule, and have it reviewed and approved by management. Conduct a kickoff meeting to establish the ground rules and a schedule of activities. Access to key subject matter experts is often the biggest challenge in any audit, so discuss that issue with senior management when reviewing the audit plan and schedule.
Schedule periodic checkpoints with audit sponsors to brief them on the audit's growth and to identify issues that might be hampering progress. Carefully document all audit findings from interviews, physical examinations and review of evidence. Report any unusual and potentially negative findings to the sponsors as soon as possible.
Auditors should have a specific work area to conduct interviews, examine evidence and write their reports. Guest access to internet services and a telephone should also be made available to the audit team.
Most reports have a list of recommended actions to address audit findings and time frames for remediation. Once the draft audit report is complete, have it reviewed by the organization being audited, if possible.
Careful planning and good project management will ensure the audit is completed on time and within budget.






