
Alex - stock.adobe.com
5 key elements of data tenancy
Data tenancy is a key piece of any data protection scheme and can be crafted around five building blocks to provide safe, secure data access to users.
Safeguarding customer data is essential for any organization, and one of the key pieces of a comprehensive data protection strategy is data tenancy.
Data tenancy refers to the ability to isolate data and allow access only to authorized users. Tenants are unaware of each other and have a virtual view of data that is restricted to the data belonging to them.
Unfortunately, there isn't a data tenancy playbook on the shelf, in part because there isn't a universal strategy. Although implementations vary based on the capabilities and limitations of technology, there are common elements that can help organize an architecture.
At the highest level, a data tenancy architecture can break down into the following five main building blocks.
1. Governance
Governance is a process of overseeing tenant data. As custodians, organizations that provide any service have the responsibility to steward data according to contractual obligations, regulatory compliance and conditions from other sources.
A data tenancy framework, based on policies and standards, should define the rules that govern data tenancy across the organization, including people, process and technologies. Proper governance ensures organizations manage and enforce tenancy in a consistent and reliable way.
Accountability includes everything from managing the tenant lifecycle to enforcing tenant data access to daily operations, responding to events and performing ongoing reviews.
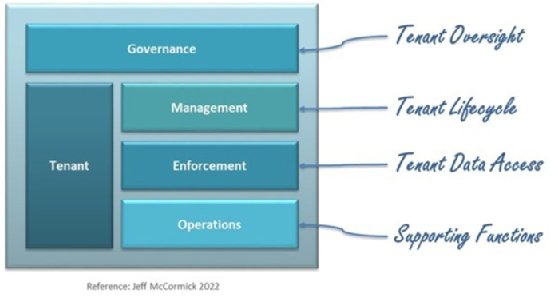
2. Tenant
A data tenant is an entity such as a person, organization or process, perhaps in combination with other things such as a product, that stores data in resources such as a database and requires data isolation and selective user access.
Organizations typically refer to the tenant as the customer of their service. A customer of many products may be a single tenant for all products or a separate tenant for each product.
Regardless of how a tenant is defined, it is important to establish a unique identifier for each tenant, commonly referred to as the Tenant ID. The Tenant ID should be a transparent administrative attribute, carrying no intelligence. Resist the urge to use the Tenant ID to influence behavior. Its sole purpose is to assist in the management and enforcement of data multi-tenancy access.
3. Management
Central management is a key architectural principle providing standardization and consistency across service offerings. Tenant management includes the entire lifecycle of a tenant, from onboarding to maintenance to offboarding. The lifecycle is best managed within a tenant master data management (MDM) asset.
Onboarding is a process in which an organization registers, profiles, configures and provisions a new tenant to local data resources. Successful orchestration of this process is critical as it is the first impression a tenant has.
Elements of an onboarding process include providing tenants with information they need to know, gathering tenant information the organization needs to know and determining how quickly tenants get up to speed using the organization's products and services.
Maintenance refers to the day-to-day changes of existing tenants, such as changes to tenant information, data restrictions and data resource mapping. Each change triggers a tenant data synchronization process from the tenant MDM to local data resources.
Offboarding is a process in which existing tenants and their data are removed from the platform. This can be logical or physical, depending on contractual, legal or regulatory requirements regarding data retention. Actions include stopping user access, liberating tenant data back to the customer and eventually purging systems of tenant data.
Characteristics of successful management include zero-touch self-service interaction, timely communication and speed. Not all of these are achievable if a customized contract is in play. Develop a playbook that achieves simple, automated and repeatable workflows.
4. Enforcement
Local enforcement is another key architectural principle providing each data resource with specific security controls. A combination of role-based access control (RBAC) and attribute-based access control (ABAC), along with security policies, helps make user data access decisions and prevents cross-tenant access, guaranteeing the safety of tenant data.
The first step to enforce data access is to determine a user's identity, which is done on a user connection basis. This means, regardless of which process requests the data -- application, database or direct connection -- the data retrieved is only for the authenticated tenant or user asserted in the tenant environment.
Tenant binding establishes a user's tenant scope. This tenant resolution is where users are seamlessly bound to a tenant, providing user attributes for use by ABAC. It is important to establish tenant binding upfront and carry it throughout the user session.
Authorization refers to permission to access a data resource considering identity, RBAC and ABAC user, environmental and object attributes. This gets the user to the front door of a data resource but not yet to the data.
Data access is dynamically enforced at the data resource. It is important this be done at the data layer to ensure that security cannot be bypassed. Tenant binding is used as fine-grained access control to guarantee users only have access to tenant data they have been authorized to access.
If done right, applications, users and developers have limited or no awareness of data tenancy. Organizations can accomplish this transparency with administrative security controls rather than business data.
Data isolation can be logical or physical, using the capabilities of the data resource to separate data for each tenant and the desired degree of commingling between tenants' data sets. Each data resource has several tools available to separate data for single tenant, multi-tenant and hybrid models.
Notice the application is not present in the architecture. Implementation of tenancy is administrative to avoid affecting application functionality. Beyond passing the user as part of the database connection, applications are simply not part of the equation.
5. Operations
There are several foundational components needed to support data tenancy.
Because the tenant MDM is a management system, data synchronization helps apply timely updates to local resources for runtime enforcement, ensuring the system complies with the desired properties. Organizations should look to design this distribution as an event-driven architecture; an asynchronous push model strategy can help achieve timely local updates.
Analytics supports other elements of the architecture, as well as provides insight into key data protection management and enforcement metrics, access, usage and data safety.
Examples of analytics questions
Where is my data?
How is access to my data enforced?
Who can access my data?
Who accessed my data in the last 24 hours?
Who tried to access my data without authorization?
What was the extent of a data breach?
Beyond contractual, audit and regulatory requirements, validating that tenant data is safe is perhaps the most important selling point a provider can offer to tenants. Trust is essential and non-negotiable. Trust is ultimately measured by a response to the customer's question, "Is my data safe?" To be successful, there is only one acceptable answer from the provider, "Yes, and we can prove it."
Monitoring and logging methods observe data access across the architecture. These processes serve as both an alerting mechanism and audit trail. Perform capturing and analyzing events with tenant context for traceability. Although each architecture component generates events, an end-to-end consolidated view is critical for a timely response to inquiries.
Backup and recovery provide an ability to restore data in the event of logical or physical data corruption. A good strategy can minimize data loss and impact, especially in a multi-tenant model. Look to establish independent backups for each tenant and recovery strategies that limit tenant downtime.
Metering and billing at a tenant level are also important, especially for consumption-based pricing models. Not all tenants are created equal; they differ in size, behavior and more attributes. Tenant footprints may vary based on access, usage (data consumption patterns) and volumes. This irregularity is one factor to consider if contemplating tenant tiering.
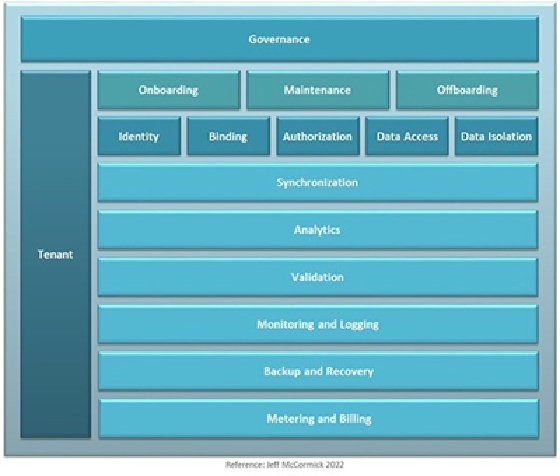
Putting it all together
A data tenancy architecture helps identify and organize the elements of a successful design. Most elements are table stakes, required in some form. The maturity of an architecture can be measured by the degree of automation, integration and friction.
A core competency of organizations is establishing an environment in which each tenant's data is protected in a consistent, reliable and provable way. As a foundational component of the architecture, it is critical to get data tenancy right. A reference architecture can help organize the key aspects and get an organization started on the path to success.








