states of digital data
Three states of data is a way of categorizing structured and unstructured data. The three states of data are data at rest, data in motion and data in use. Data can change states quickly and frequently, or it may remain in a single state for the entire life cycle of a computer. Understanding the characteristics and differences between data states can help organizations handle sensitive information more securely.
In the past, data center administrators (DCAs) spent a lot of their time managing data at rest, particularly in market segments that have strong compliance burdens. The degree to which companies now rely on real-time analytics, however, has put more emphasis on managing data in use.
Data at rest
Data at rest is a term used by computer professionals to describe all data in computer storage that is not currently being accessed or transferred. Data at rest is not a fixed state, although some data might remain in archived or reference files where it is rarely or never accessed or moved. Examples of data at rest might include vital corporate files stored on the hard drive of an employee's computer, files on an External hard drive, data left in a storage area network (SAN) or files on the servers of an offsite backup service provider.
Data at rest is considered stable compared to data in the other states. It is not moving between systems or devices and is not being processed by a CPU. Data at rest is considered to have reached its destination.
Businesses, government agencies and other institutions take precautions to prevent threats posed by hackers to data at rest, including data encryption, hierarchical password protection, secure server rooms and outside data protection services. In addition, multifactor authentication and strict data security protocols for employees help to protect information that is at rest. For some types of data such as medical records, specific security measures are mandated by law.
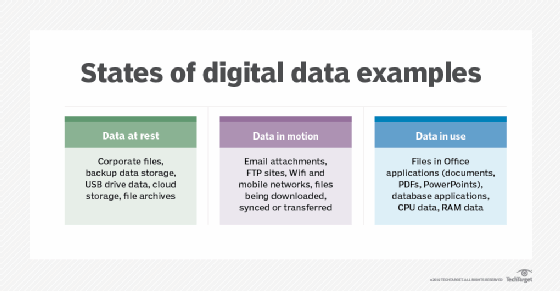
Data in motion
Data in motion is data that is moving or being transferred between locations within or between computer systems. It can also refer to data that is within a computer's RAM that is ready to be updated, processed, accessed and read. Data moving between cloud storage and a local file storage point or moving from one network to another is also considered in motion. Data in motion may be moving within a computer system, over a wireless connection or along a wired connection. In addition, files dragged from one folder to another, within an FTP site or emails are considered data in motion.
Like data in the other common states, data in motion should be encrypted in order to protect it from interception by hackers. Common forms of encryption for data in motion include encrypting the data before it is transmitted (while in a data at rest state) or encrypting the passage along which the data is sent.
Data in use
Data in use is data that is currently being updated, processed, accessed and read by a system. Because data in use is directly accessible by one or more users, this is the state at which data is most vulnerable to attacks and when encryption is the most essential. In addition to encryption, some important ways that data in use is protected include authentication of users at all stages, strong identity management and well-maintained permissions for profiles within an organization. Beyond the digital forms of protection, it is common for organizations to have their employees sign non-disclosure agreements about protecting the data they have access to.








