6 data privacy challenges and how to fix them
Fragmented data protection laws, technology disruptions, AI adoption, data governance and consumer trust are among the complex issues confronting businesses in need of remedies.
Businesses are facing personal data privacy challenges in a dynamically evolving digital age. Companies that successfully meet these challenges can gain a competitive advantage in the marketplace. Failure to do so can negatively impact business operations.
Personal data privacy is a critical component of a comprehensive data protection strategy designed to safeguard the collection, use, alteration, retention and disclosure of data. It encompasses the right of individuals to keep their information private, while advocating for control of private information and protecting an individual's confidentiality. Personal data is typically information classified as personally identifiable information (PII), personal health information (PHI) or financial data but can also include information that's not necessarily personal.
Under some jurisdictions, sensitive data, referred to as special category data, requires additional protection. This data includes personal data revealing racial or ethnic origin, political opinions, and religious or philosophical beliefs; trade-union membership; genetic data, biometric data processed solely to identify a human being; health-related data; and data concerning a person's sex life or sexual orientation. Personal information that's publicly available, de-identified or aggregated isn't regulated.
Why is data protection important to business?
Safeguarding personal data is an ethical responsibility and an essential competency for any organization. Businesses are subject to data privacy laws and regulations, contractual obligations, consumer privacy agreements and stipulations from other sources.
Enterprises have the responsibility to keep personal data private. Data that's exposed can cause operational downtime as well as the consequences of noncompliance, including civil penalties, monetary fines, brand damage, reputation harm, legal action, consumer mistrust and financial loss.
Ensuring consumer data privacy is a business imperative. Successful companies view personal data privacy as a core business value that can be a competitive differentiator in winning and retaining business. Validating that personal data is safe is perhaps the most important selling point a business can offer consumers. Organizations that prioritize data privacy instill customer loyalty, enhancing business reputation and brand value.
Data privacy exposures, commonly referred to as data security incidents, are critical business concerns. Data incidents can result in consumer identity theft, profiling, censorship, surveillance, harassment, discrimination, exploitation and fraud.
There are two types of data incidents: data breaches and data leaks. A data breach is a security incident concerning unauthorized data access. A data leak is an internal privacy incident concerning accidental or intentional unauthorized disclosure, dissemination or sharing of protected data.
Key business challenges and remedies
Enterprises implementing effective data privacy management face several challenges. Each challenge requires measures to mitigate data incidents. Although no preventive data security measures are guaranteed 100% secure, proactive risk management better positions businesses to reduce risk exposure.
1. Consumer trust
In an age when data incidents are commonplace, businesses need to ensure their customers that their data is safe. Personal data processing today is a back-office operation. Consumers, largely unaware of how their data is being managed and shared, are left wondering, "Is my data safe?"
Mistrust is rooted in a lack of transparency. Perhaps most effective is the consent agreement in which individuals accept the terms set by the business for how their data will be processed. Unfortunately, consent is largely ineffective because individuals often ignore incomprehensible privacy agreements and simply agree to the terms. Another form of transparency that's notably absent from many consumer interactions is proactive privacy-related communication.
Companies need to be transparent to gain the trust and confidence of their customers. Be upfront in communicating data privacy protection and use it as a business strength. Transparency ensures new and existing customers that their personal information is being used and maintained with reasonable and appropriate security measures and practices. Businesses can take the following actions to ensure data privacy confidentiality and build trust among consumers:
- Be sure data privacy consent agreements are in plain language and a consumable length.
- Engage marketing and sales teams to emphasize protection messaging.
- Place a data values statement on consumer-facing website and application interfaces.
- Provide timely incident notification to consumers with remediation details.
- Give consumers a complete 360-degree view of their information.
- Offer consumers easy opt-out for their data being used.
- When importing data, ensure individuals gave their consent at the data source.
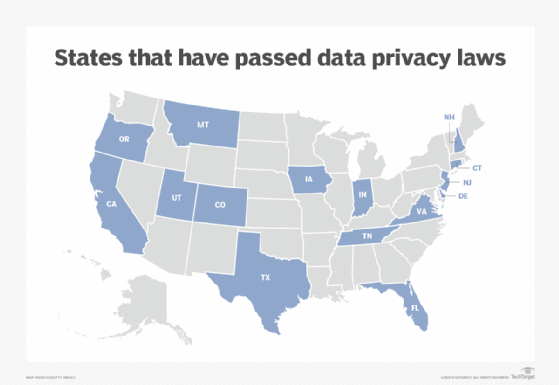
2. Law and regulation fragmentation
Businesses must navigate an increasing patchwork of data protection legislation and regulations. This environment is dynamic, complex and influenced by several factors.
International, federal and state jurisdictions can apply to a company's location as well as the location of the consumers. The U.S. doesn't have a single comprehensive federal consumer data protection law. Instead, it has several specific business-sector laws that protect specific data sets. Business revenue and the amount of personal data can affect the legal aspects relating to compliance.
Companies should plan and allocate sufficient resources to ensure impacted stakeholders are up to speed with this evolving regulatory environment. Consider the following actions:
- Do the right thing regardless of legal protection.
- Account for multiple laws and regulations, which likely vary among jurisdictions.
- Anticipate legislation and regulations that lag technology advancements.
- Align consumer consent terms with data protection regulations.
- Actively monitor new and existing changes to laws and regulations.
3. Data governance
Governance is a critical process within a data privacy program. As custodians, businesses are responsible for stewarding data privacy with accountability for compliance and oversight. Companies often underestimate the complexities and fail to make proper investments, resulting in undesirable consequences.
Privacy is an increasingly complex area of data protection that's often underfunded, understaffed and an afterthought as evidenced by passively enforced policies, poor employee training and inadequate system protections. Many businesses simply don't have sufficient staff, processes and technology in place to adequately govern data.
Governance should be at the forefront of any new data initiative. Implement a framework based on policies and standards that define the rules governing personal data privacy across the enterprise, including the following considerations:
- Understand the organization's data and how it's used.
- Establish a data privacy council and foster collaboration.
- Make sufficient investments, preferably allocating a separate budget for data privacy.
- Train internal staff, have access to legal counsel and hire data privacy experts.
- Extend privacy terms to partners with contractual auditing provisions.
4. Technology disruption
Technology is a key enabler in data privacy. It can be used to better protect personal data, but it also can be used to subvert privacy itself. As technology forges ahead, data protection becomes more complex.
Advancements in fingerprint and eye scans for biometric identity recognition, IoT using sensors to track and exchange data, and AI algorithms to make better data privacy decisions assist enterprises in protecting personal data. Yet technology advancements and the variety of digital device interactions increase complexity and can compromise data privacy. Complexity also increases the potential for human error and security threats from cybercriminals using the same technology.
Businesses need to thoroughly and completely assess new technologies, understand potential risks, put protection controls in place and proactively establish mitigation and response measures ahead of interacting with customers. Consider the following actions:
- Put data privacy at the forefront of new technology decisions.
- Establish data privacy literacy and collaboration across the enterprise.
- Ensure the entire organization understands and is on board with the use of technology.
- Resist financial pressures to implement new technologies without due diligence.
- Stay abreast of new technology security threats and safeguards.
5. Data operations
Personal data collection is on the rise with no end in sight. Unprecedented amounts of personal data are being collected, bought, sold and stolen. Welcome to the modern-day Wild West. All this data is putting a strain on business operations.
Personal data is at the root of most digital interactions, including biometric scans, QR (quick response) codes, fitness trackers, smartphone location trackers, sensors, texts, pictures, internet purchases and data exchanges to third parties. Businesses utilize this information to service consumers and possibly create profiles for such things as analytics, personalization, targeted advertising and sales. Managing all this data can overwhelm a business.
It's important to operationalize privacy controls in modern systems and retrofit older systems. For new systems, data privacy should be baked into the core system design on day one. For legacy systems, data privacy should be built as a wrapper layer to the core system in a plug-and-play architecture. Consider the following actions:
- Only collect, retain and share data as needed to run the business.
- Ensure external sources provide opt-in and opt-out changes over time.
- Design systems with data privacy in mind from the start.
- Implement policy-based intelligent automation.
- Strike the right balance between data privacy protection and product usability.
6. AI adoption
Artificial intelligence is spearheading the current digital revolution. It's still early in its evolution, but it's beyond a hype wave and here as product. Predictably, AI has some growing pains and inherent concerns.
AI algorithms are using the data collected about individuals to make decisions, yet AI makes mistakes. It may be coded to be impartial, but the safety layers or guardrails on top of AI have shown bias and inaccuracies. Additionally, AI uses data to infer other data about individuals that has shown to be subject to error.
AI is used by hackers to subvert data protections and access data for nefarious reasons. Cybercriminals use AI to launch sophisticated attacks at scale to gain access to personal data.
Businesses should acknowledge that AI plays a role in data privacy. Understand associated risks and proceed with caution. Organizations should first use AI to augment human-based data privacy decisions. Any progression to autonomous AI for data privacy should be a conscious enterprise decision. Consider the following actions:
- Carefully plan the shift of data privacy management from humans to machines.
- Understand AI data protection and security threat capabilities.
- Continually assess and test algorithm bias starting at data acquisition through delivery.
- Ensure developers are creating ethical algorithms with demonstrable fairness.
- Align AI values to business values.
- Understand how third-party partners use AI for data and how consumers may perceive that.
Trends in data privacy protection
Expect several of the following trends surrounding data privacy protection to affect the way businesses collect, process, govern, secure and distribute information:
- As consumers become more savvy, new demands will be asked of businesses.
- Technology innovation is forging ahead at breakneck speed, forcing businesses to play catch up.
- AI is on a trajectory to dominate data privacy protection and threats.
- Cybercriminals will ramp up efforts to exploit vulnerabilities to steal personal data.
- Unconnected jurisdictions are racing to implement data privacy requirements, creating a proliferation of nonuniform laws and regulations.
- As the social and economic digital revolution expands, personal data collection will follow.
- Societal thinking regarding data ownership and control is evolving and a new paradigm of "privacy by default" will be needed to correct fundamental flaws.
- The cost of data privacy protection will increase because of complexity amid expanding business investments.
- Businesses will heighten their attention to digital safety and ethics and build a culture around data values.
- The sale of personal data -- whether it was acquired legally or stolen -- is big business, leading to a personal data economy.
Jeff McCormick is an enterprise data architecture director and IT principal who has extensive experience in data-related IT roles. He is also an inventor, patent holder, freelance writer and industry presenter.








