What is data egress? How it works and how to manage costs
Data egress is when data leaves a closed or private network and is transferred to an external location. This occurs within the context of cloud computing when stored data moves out of a private cloud network and into a public cloud or an external network. The term is commonly used in both network security and network and data management.
A cloud storage service provider managing data for customers performs data egress when a client requests to have its data transferred from the cloud to its internal network. Examples of data egress in an enterprise setting include emails sent to clients and other external recipients and on-premises data uploaded to a cloud data storage provider. These are business operations where the data egress is authorized. On the other hand, when a malicious actor steals data from an insecure network, that is unauthorized egress. Egress management is an important business function.
Data egress vs. data ingress
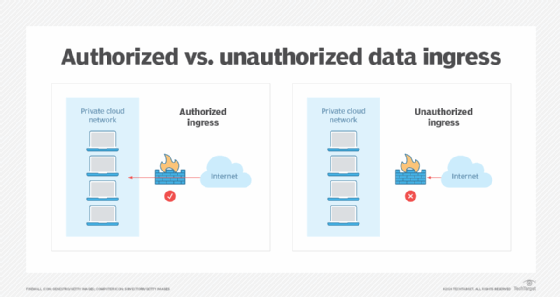
Data ingress happens when data is transferred from an external location into a closed or private network. It's the opposite of data egress. A business uploading a new data set or file to its network is an instance of data ingress. A network's IT staff is responsible for analyzing the flow of inbound and outbound network traffic.
As with data egress, ingress can be either authorized or unauthorized, also referred to as solicited or unsolicited. When data is imported from an external database for business purposes, that's authorized or solicited ingress. Meanwhile, malware hidden in an email or a data set represents unauthorized or unsolicited ingress. Data ingress traffic is typically a bigger security concern for IT teams than egress traffic.
Examples of data egress
An IT department typically uses the following methods when transferring data, all of which are forms of data egress:
- Emails. An email message or attachment sent to a recipient outside an organization's internal network is data egress.
- Data exports. A more complex egress example is a third-party cloud storage provider sending a large volume of data to a client in response to that client's request for that data.
- HTTP transfers. An IT department can interact with a third party or external application programming interface (API). Here, a request is made for specific data from the external network owning the API. From the external network's perspective, the egress occurs as data leaves the network.
- Removable storage hardware. A more traditional example involves data leaving a network to be stored on physical storage hardware, such as external hard drives or flash drives.
Data egress threats
Hackers and malicious actors are using increasingly sophisticated cyberattacks to get at data. They have different data exfiltration methods and ways to leak or steal data from a network, including the following:
- Malware. Malware and other viruses, such as backdoor Trojans, are introduced to a network through data ingress. They are often hidden within data for the purpose of damaging or stealing sensitive data. This also includes ransomware, where perpetrators lock data and require a ransom from the owner before returning it.
- Social engineering. Malicious actors use social engineering techniques in emails, texts or other forms of communication to trick individuals in an organization into revealing sensitive or personal data, such as identity information or passwords. They then use the information against the organization somehow. With phishing attacks, threat actors use urgency or emotional appeal to steal sensitive information.
- Denial-of-service attacks. DoS and distributed DoS attacks flood a network with illegitimate traffic so the network becomes slow or unusable. This makes it difficult or nearly impossible to perform normal data transfer operations.
- Data interception. Specifically, when data is in transit, bad actors can intercept and steal unencrypted data.
- Insider threats. Within a company, an employee with access network credentials can steal sensitive data for uses that violate company policies. This also represents unauthorized egress.
What are data egress costs?
Cloud storage software providers handle an organization's data management needs but often charge data egress fees. While data ingress into these platforms is usually free, users typically are charged to move data out.
End users are charged for the amount of data bandwidth they use per month. Public cloud providers charge a few cents per gigabyte (GB) of data transferred out of their platforms. Depending on the provider, data egress charges can go up or down after a set number of terabytes (TB) are transferred.
For example, Amazon Web Services' (AWS) Elastic Compute Cloud charges $0.09 per GB of outbound data for the first 10 TB transferred in a month for users in North America. That cost decreases slightly after 10 TB are transferred. Microsoft Azure's pricing allows 100 GB of free egressed data per month before also charging from $0.05 to $0.18 per GB, depending on the source continent and the amount of data.
In January 2024, Google Cloud abolished its data egress fees for customers who switch to a new platform and transfer their data out of the platform. AWS and Microsoft did the same within months. This occurred for two reasons: the competitive nature of the cloud market and the need to comply with the European Data Act and other regulations requiring sensitive data to be removed or deleted when no longer in use.
Best practices to manage data egress costs
Following a set of data management best practices positions an organization to reduce unnecessary data egress costs before they accrue. These practices include the following:
- Vet cloud services. Organizations should research several cloud services to identify platforms that fit their needs and budget. Some providers enable direct or dedicated network connections to cut costs.
- Place data in one cloud network or region. Data transfer costs are often lower within the same network or region. One specific approach is to cache frequently accessed data locally to reduce the need for transfers.
- Compress data. Data volume is one of the factors affecting egress costs. Data compression reduces transfer volumes and costs.
- Analyze use patterns. An organization should monitor how it's using data over time to identify inefficient transfer methods.
- Schedule strategically. Peak use times are when a cloud provider experiences the highest network traffic; lower rates during off-peak times encourage customers to transfer when network traffic is lighter.
Best practices to manage data egress security
Data egress costs aren't limited to data transfer costs from cloud services. They also come from loss or theft of sensitive data. The cost of data breaches includes lost productivity and legal fees.
There are a number of best practices to follow to prevent data egress security issues and avoid data breach costs:
- Monitor traffic. IT departments should monitor and log network traffic for signs of malicious activity. Tools such as security information and event management are used for these analyses.
- Create enforcement policies. Having an organizationwide policy ensures everyone knows acceptable data handling and egress practices.
- Set firewall rules. Implementing a firewall and configuring it with rules to restrict unauthorized egress are key to securing a network.
- Apply security measures. Various security measures, such as encryption, data loss prevention and virtual private networks, also secure IT networks.
- Set user permissions. Permissions make it so only authorized, trusted personnel can access sensitive data.
- Train employees. Once policies are set and security measures are in place, employees should be trained to ensure rules are followed and data is managed properly.
Cloud block storage comes with its own set of challenges, and managing data egress costs makes the list. Learn what to watch for.








