
rvlsoft - Fotolia
How to enhance FTP server security
If you still use FTP servers in your organization, use IP address whitelists, login restrictions and data encryption -- and just a few command prompts -- to keep them secure.
There are two ways that FTP servers can be a liability: Information can leak from an insecure FTP server, and unsafe content uploaded to the server can cause chaos in the infrastructure. Luckily, there are easy steps to secure this hardware, set login protocols and allocate permissions.
At best, during a hack, the server is used for an FTP warez site with pirated content. At its worst, a hack can provide an exploitable backdoor into your data center, which can compromise security safeguards.
If you decide to experiment with FTP server security from scratch, you can install VSFTPD by using the distro-appropriate version of the command:
sudo apt-get install vsftpd (Ubuntu)
sudo yum install vsftpd (Red Hat)
Depending on your Linux OS, the VSFTPD configuration file may be located on an alternative path. The configuration options vary between OSes and the location of key files.
Enabling encrypted traffic is recommended to stop traffic being sniffed in transit; FTP passwords are sent as plain text, which isn't secure. It is important to encrypt traffic before starting any further configuration steps. You'll also need a secure password and the ability to enforce it at the OS level.
After encrypting traffic, there are several settings -- such as logins, directory and traffic filters -- that you can update to secure the server. This demo uses VSFTPD on Ubuntu.
Enforce FTP server security with login permissions
One of the easiest ways to help FTP server security is to turn off anonymous login. With anonymous login active, server access is wide open.
Anonymous login is disabled by default, but to double check, use
sudo grep 'anonymous_enable' /etc/vsftpd.conf. You can use the same command in Red Hat Enterprise Linux, though the file location might be different.
This command locates the configuration line and its output. If it is set to yes, it must be changed to no. Start this process, and log in with sudo vi /etc/vsftpd.conf.
Locate the anonymous login enable, and change it from yes to no. Once you change the setting, you must restart the server for the changes to take effect. This process works on any Linux distribution that uses systemd, and you can use sudo systemctl restart vsftpd.
You should also consider the write ability access, which is disabled by default. To enable it, locate the line write_enable=YES, and uncomment it. This lets users write files if they have the right level of access. Again, depending on security requirements, you may not need users to be able to write files.
Solidify role access with chroot
Another security step is to restrict users to their home directory. Depending on your system's setup, you may or may not need this, but it prevents users from being nosey. You can do this with the chroot command.
To enable this or see if it is enabled, open the vsftpd.conf file, and look for the line that starts with chroot_list_enable. You must also populate the chroot_list_file to include all the users you must add. This list is commented out by default. In order to update the chroot list file, uncomment all lines, and restart the file. The relevant lines appear as such:
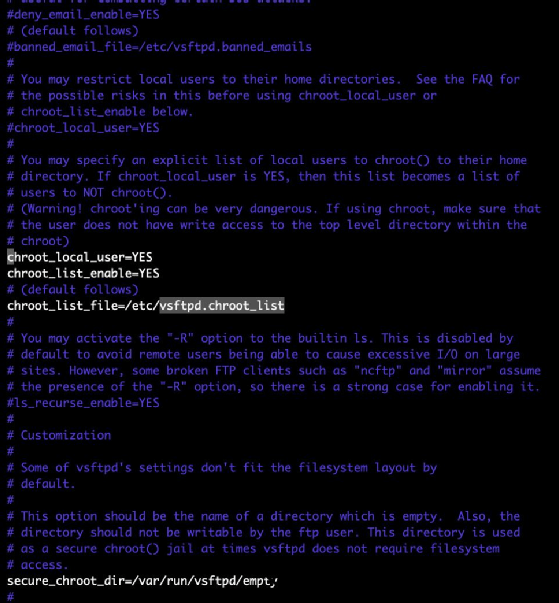
There are many configurations possible with chroot, so it would be prudent to spend some time looking at the configurations and manuals to ensure it meets the required criteria.
The system's named users will automatically be able to log in to the system. This privilege allows users to upload random binary files to the home directory and then use Secure Socket Shell to log in, change the permissions on the file and execute it.
Random file uploads aren't a desirable behavior in production systems, and they can compromise FTP server security. A user who has rights to log in to an interactive shell and upload data has all the necessary resources to upload and execute a questionable file.
For additional prevention, if you know where server data will come from -- such as businesses with static IP addresses -- you can use iptables to restrict access to known, safe IP addresses. The iptables program works to effectively block out users who should not have access and increases FTP server security.







