
carloscastilla - Fotolia
Linux features beyond server management
Due to its open source nature, Linux is constantly gaining new capabilities. Here's a look at some common use cases and features.
With its text-based interface, Linux provides IT administrators an easy and quick way to navigate files, grant permissions, run containers and build data processing capabilities on an open source OS.
Linux has traditionally stayed in on-premises architectures, but that's starting to change. With the development of containers and orchestration, organizations are using it beyond bare metal.
If you decide to use these newer Linux features and capabilities, however, you should still familiarize yourself with the kernel, as well as some useful commands and security protocols.
What are the main features of the kernel?
The Linux kernel is an essential part of running the OS and is fairly uniform across distributions. At its core, the kernel has an interrupt handler, a scheduler and a supervisor. These three components help the OS run smoothly and process information. It also has a few features that make Linux useful in an organization.
Two main attributes of the Linux kernel are that it is multiuser and multifunction. This means you can have more than one admin simultaneously working on the same program. The obvious benefit of this is that you and your team can use the same files, OS and command line for a range of projects, increasing collaboration and efficiency.
The Linux kernel also includes everything you need for hardware and application support.
How can I deploy containers in Linux?
With container technology, you can run applications in an isolated, more efficient way that minimizes infrastructure utilization. Containerization on Linux has been around since 2008 but is gaining more traction with tools such as Kubernetes, which launched in 2015.
Kubernetes, originally developed by Google, is a program for container orchestration. It helps you deploy, maintain, schedule and scale container applications across server nodes. It is compatible with both Docker and CoreOS Rkt, which are programs you can use for container creation, configuration and deployment.
Docker is ideal if you need to host an application and all of its associated components, and it provides one alternative to cloud-based servers. Common use cases are application testing and scaling.
CoreOS, a 2014 Red Hat acquisition, has Rkt, which operates on most Linux distributions as a binary file. It runs pods -- collections of applications -- as containers. Its components are completely open source, and it is useful for large, multimachine deployments.
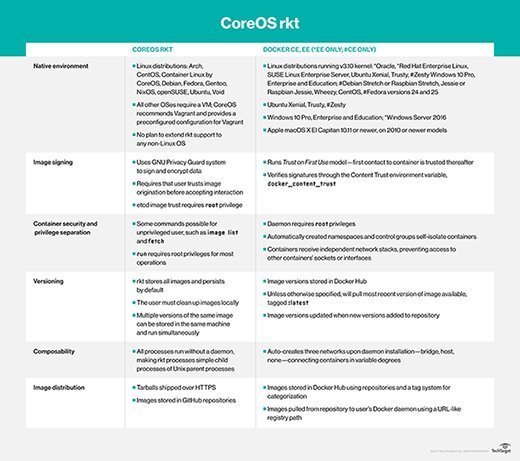
If you don't want to run either Docker or CoreOS, one Linux feature you can use is systemd containers.
Where can I start with file and permissions management?
A common Linux feature is file management, which is all done through the command-line interface. Even if you prefer to use a graphical interface, it's helpful to know a few commands for file movement and creation.
Common commands for file info and management include the following:
- mkdir: Generates a new directory with a name path;
- cp: Copies files and directories;
- mv: Moves files or directories to another file location;
- tail: Shows the last few lines of a file; and
- ls: Lists files and directories running in the active directory and provides information about these components, such as last open time and when it was last modified.
These main commands make it easy to shuffle files around and make new directories without any hassle.
What Linux features are there for security?
Because Linux is an open source OS, you must still make sure that your data center hardware and information are secure. One way to do this is to use the Security Enhanced Linux (SELinux) kernel. It has three modes: enforcing, permissive and disabled.
SELinux uses a least privilege model, which runs on specific written access policies. This means the system only grants access to users and capabilities if you script a policy for that capability.
Another well-known option is AppArmor. You can run it on SUSE Linux or openSUSE. Instead of writing permissions, AppArmor uses configuration files for its security framework. These files include all necessary information for mandatory access control to secure the OS.
One reason you might select AppArmor is usability, because it lets you customize access profiles in a few simple steps.







