Cloud backup and disaster recovery evolve toward maturity
Christophe Bertrand, of TechTarget's Enterprise Strategy Group, discusses survey results on data protection initiatives in the cloud and challenges for organizations.
The use of cloud backup and disaster recovery technologies in organizations is widespread now and likely to become almost universal in the near future, according to a 2023 survey of IT professionals involved in data protection initiatives that was conducted by TechTarget's Enterprise Strategy Group (ESG).
Sixty-five percent of the 397 respondents said their organization was using cloud-based target systems to store backup copies of on-premises data, while the use levels for backup as a service (BaaS) and disaster recovery as a service (DRaaS) offerings were 62% and 52%, respectively. Additional deployments planned within the next 12 months would increase adoption to 90% or more for all three technologies.
But half of the surveyed organizations are recovering 75% or less of their cloud data per incident on average -- a result that "is not acceptable" for a mission-critical process, said Christophe Bertrand, practice director for data protection, data management and analytics at ESG. Bertrand co-authored a report on the survey titled "Cloud Data Protection Strategies at a Crossroads" that ESG published in August 2023. In this Q&A, he discusses some of the key survey findings and what they mean for IT teams managing cloud backup and disaster recovery efforts and for vendors of data protection tools.
Editor's note: The following was edited for length and clarity.
Are BaaS and DRaaS two different things? And if so, what's your take on the difference between them?
Christophe Bertrand: There's some confusion about that in the market, and it's unclear whether there's a clear-cut differentiation. A lot of people think BaaS and DRaaS are about the same -- it just depends on how a vendor defines its software. I prefer the term data protection as a service in general. But there's an agreement to a certain extent that BaaS is essentially as granular as on-premises backup. It's also considered to be better for ransomware recovery than DRaaS because it's a point-in-time thing.
 Christophe Bertrand
Christophe Bertrand
At the end of the day, backup as a service is kind of just that. It operates like a regular backup application, using a schedule and point-in-time backups. DRaaS is more about failing over if something comes up as a disaster recovery process. It's designed to replicate or restore data environments automatically; it doesn't transform data in the same sense that a backup may have a particular data format. DRaaS is about moving the data from point A to point B and being able to get back to it as quickly as possible, especially in the context of a failover. But again, there's a lot of fuzziness.
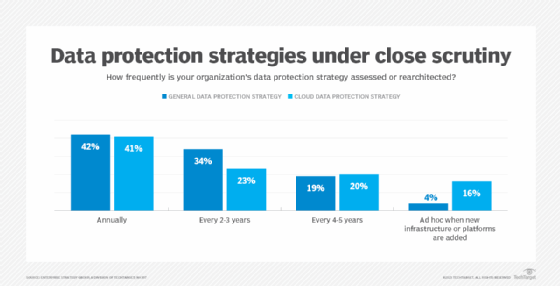
The largest groups of respondents review both their general and cloud data protection strategies annually, and a sizable number -- 16% -- review their cloud strategies when they add new IT infrastructure or platforms. What do you make of those numbers and how often organizations are reviewing their data protection strategies?
Bertrand: The fact that so many would review annually was a bit of a surprise. I was expecting it to be more like two to three years or four to five years. Historically, it's been more in that longer term. You get a backup and recovery solution, and it's kind of sticky in the environment. You don't want to go change things too quickly because it's pretty strategic and critical.
But with the flexibility that cloud data protection affords, a lot of these solutions can essentially get updated whenever you log on because they're SaaS-based. Also, there's so much data in the cloud now and lots of investment in digital transformation, new platforms and cloud-native applications, which is triggering some rethinking of cloud data protection strategies. All of this I think is shortening the review cycles.
It's actually a domino effect: Data protection follows data production. Production has become a lot nimbler as new applications are deployed or redeployed because of digital transformation, and it fundamentally changes the relationship between the vendor and the customer. When a purchase contract is signed, it may be that next year or in a couple of years we're going to revisit whether you're still the right vendor for us. And that's changing how vendors need to build a solution that has more of a lasting impact for the end user so they don't get put back into a competition every two or three years, because that's a lot of sales investment and a lot of uncertainty.
Forty-one percent of respondents said using public cloud data protection services creates another potential target for ransomware attacks, as opposed to 58% who said it gives them more confidence about being able to recover data after a ransomware attack. What do you think about those two data points?
Bertrand: The net-net on this is that both positions are valid. What's interesting is looking at what's behind the sentiment. Pick one or the other: 'What makes you say that?' That would be a great way for user organizations to start a conversation internally. I would expect that even in the same team, you'll have people with those opposing views, which is probably healthy.
I can argue for either side. On the one side, yes, you're right: It's great to have cloud-based data protection services simply because you have more flexibility. Those cloud vendors have done a tremendous amount of work building great security platforms -- they can potentially invest a lot more than you can as an individual company.
I can also see the argument that now we've got all these new platforms and all these new cloud vendors, but are we really managing things correctly so that we're protecting ourselves well against ransomware across the board? Isn't this just making the possibilities so much wider for the bad guys to come attack us when before I had a more contained environment and perimeter that I could better control? Both perspectives are valid, and they're not necessarily mutually exclusive -- and they should both end up in the [request for proposals] in one way or another.
Multi-cloud use is widespread: More than 90% of the surveyed organizations use multiple cloud infrastructure service providers, and more than half use three or more. Also, 70% use different backup and data protection tools in separate cloud infrastructure environments. Is using various tools instead of a single data protection platform pragmatic or potentially problematic?
Bertrand: The multiplication of tools is not a good idea long term, especially at scale. I think the 'best tool for the job' percentage just shows you that the teams are pretty siloed, potentially, in terms of who manages which cloud operations. In the end, you'll probably end up having operational efficiency issues. Long term, the unified view is better. That doesn't mean the data protection engine or the services or the APIs won't be specialized for different cloud infrastructure vendors, but there are a bunch of things that you can probably manage as a policy at a high level through a unified capability.
The risk is to have too much specialization in each hyperscaler's environment in terms of data protection, leading to complexity and the risk of incoherence because a lot of applications and data will be moving from cloud to cloud. A lot of the cloud's appeal is about this freedom of data to move around, but by being too specialized in the data protection processes, you could create an imbalance over time.
But right now, the reality is that if you're a vendor, you should make sure people think you have the best tool for the job. That's in your interest for the vast majority of the customers you'll be talking to.
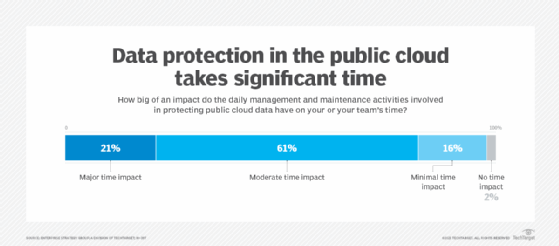
A combined 82% of the respondents said daily management and maintenance activities related to protecting public cloud data have a major or moderate time impact in their organization. What do those results indicate to you?
Bertrand: It indicates that there's still plenty of room to grow on operational efficiency, and that may be tied to the fact that people are using this 'best tool for the job' type of approach. It's a form of technical debt, really, that you're looking at here. In time, as processes get more unified, those numbers should get a little better. It should be easier to manage more with fewer people. Part of this is growing pains in the market and the evolving maturity of cloud-based tools.
Data protection is a key thing, so it should take some time, but more automation is long overdue in some areas and I also expect that to finally be solved. We're starting to see it, and automation of the orchestration process will probably become easier to get to with the adoption of new AI and machine learning technologies. They're already present in a lot of backup and recovery processes, but maybe more will be done on the ability to converse with the system, get more complete reports, do better testing, and simulate the type of failures that could happen and then optimize for the recoveries. There's a lot in flight that will happen in time.
Similarly, on staffing levels, 47% of the organizations had three to five full-time staffers focusing on cloud data protection activities, while a combined 40% had six to 10 or more than 10 people working on this.
Bertrand: It's an average, and your mileage will vary. But there are only two things we know for sure about the future: more ransomware and more data. It's not surprising that you need a lot of people to do this.
Read the full report
Enterprise Strategy Group subscribers can click here to access the research report on the survey covered in this Q&A.