
3-2-1 backup strategy explained: Is it effective?
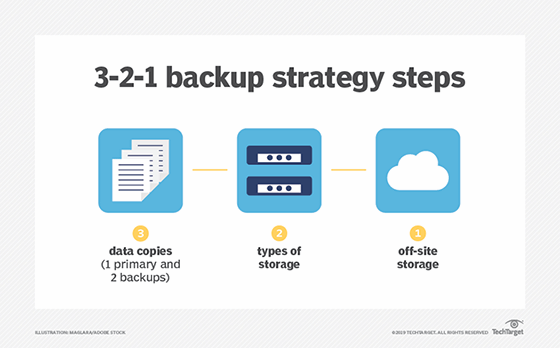
The 3-2-1 backup strategy is a time-tested data protection and recovery methodology for ensuring that data is protected adequately and up-to-date backup copies of the data are available when needed. The basic concept of the 3-2-1 backup strategy is that three copies of the data are made to be protected, the copies are stored on two different types of storage media and one copy of the data is sent offsite.
In the classic 3-2-1 backup scenario, backup software is used to make a copy of the company's critical data, with the copy of the data saved to another on-premises data storage device. During that process or immediately afterward, two more copies of the data are saved to two other devices; traditionally, at least one of those devices was a tape library. Tape was a standard part of the process because it made it easy to create a portable copy of the data in the form of a tape cartridge that could easily be sent off site. In many environments, however, tape has been replaced by a hard-drive storage system.
Although the 3-2-1 backup approach has been a keystone of data protection for decades in data centers large and small, it is a concept that is still embraced by most backup software and hardware vendors as a best practice for using their products effectively. The vendors recognize that the general concept is still valid, regardless of how or where a company stores its data, even as new requirements and voluminous data have made the 3-2-1 equation a bit more complicated.
3-2-1 backup rules
The 3-2-1 backup strategy is made up of three rules:
- Three data copies. Three copies of all critical data should be made on a regular basis -- daily or more frequently -- including the original data and at least two backups.
- Two types of storage. Two different storage types should be used to store the data. Both copies of the backed-up data should be kept on two separate storage types to minimize the chance of failure. Storage device types could include an internal hard drive, external hard drive, removable storage drive, a tape library, a secondary storage array or a cloud backup environment.
- One offsite location. One copy of the data should be shipped to an offsite storage facility. At least one data copy should be stored in an offsite or remote location to ensure that natural or geographical disasters cannot affect all data copies. This copy can be physically delivered to the offsite location, as with tape-based backups, or it can be replicated to the secondary site via telecommunications facilities.
How is a 3-2-1 backup strategy effective?
The 3-2-1 backup strategy is recognized as a best practice for information security and data protection professionals. Although the process doesn't guarantee that all data will never be compromised in some manner, the strategy eliminates some of the risks involved in backup procedures. The 3-2-1 methodology ensures there is no single point of failure for data. Not only is an organization covered if one copy is corrupted or a technology fails, but also if a natural disaster or theft occurs that wipes out the physical storage types.
This article is part of
What is cloud backup and how does it work?
The data recovery process employing the 3-2-1 methodology would be as follows:
- Original (active) data is corrupted, damaged or lost. If the production copy of data is unavailable, the first alternative is to recover the necessary data from the backup copy stored in-house on another medium or secondary storage system.
- Second data copy is unavailable or unusable. If the system -- tape or drive -- used to store the second data copy is unavailable or the data copy is damaged, out-of-date or otherwise unusable, the offsite copy should be recovered back to the in-house servers.
- Restart the 3-2-1 process ASAP. Once a suitable data copy has been mounted and operations have been restored, the backup process should begin again as soon as possible to ensure that data continues to be adequately protected.
Are there variations of the 3-2-1 backup methodology?
There are several ways to achieve a workable 3-2-1 backup system, and the variations on the basic theme will depend largely on the following:
- The amount of data to be protected.
- Currently installed and available storage equipment.
- The type of offsite repository resources that are available and easily accessed.
For example, the first step of making the three copies of the backup data can be accomplished in a variety of ways.
The simplest method would be for the backup software to create the primary backup copy and then the same backup software or a replication utility would be used to make the two additional copies, storing the two copies on different types of media. Note that if a storage vendor's replication or storage snapshot function is used, the target storage system might need to be identical or very similar to the originating system.
Alternatively, mirroring could be used to create the first two copies simultaneously, with the third spun off from one of those copies. Since one copy must reside on a different medium, the process of making that copy is often the final step in the process. This is because copying to a different media type is likely to occur at a different rate than that of making the first two disk or solid-state drive-based copies. Alternatively, a split mirror approach can be used to create two copies residing on the same media, followed by copying one of those copies to another medium.
For the second copy that is maintained in-house for quick or operational recoveries, companies should store that copy on another server or storage system separate from the originating equipment. Ideally, the secondary storage device should be located on a separate network -- or network segment -- to ensure both copies aren't likely to be contaminated in the event of a malicious attack. The target gear for the second copy should allow easy access to the backup data in case it's needed, such as if the original data is lost or damaged. Storing copy number two on equipment similar to the original system should facilitate recoveries.
However, the in-house copy doesn't necessarily have to be stored on the same or similar media. In some cases, an organization might make the primary copy and then copy that data to two tape drives, simultaneously or sequentially. One tape cartridge would be retained on-site, and the other would be sent to the offsite facility. The drawback to this approach is that recovering data from the on-site tape might take some time -- certainly longer than recovering from a hard disk or solid-state drive. This would also be true if other types of removable media were used, such as optical disks or removable drives, although recovery times will vary. Still, recovery from any form of removable media, including tape, is likely to be faster than recovering from a cloud storage service.
Some backup software applications will handle the multiple-copy aspect automatically, possibly even creating the second or third copy. Data duplication or replication applications can also handle this chore. In small environments, the second and third copies can be triggered manually. This method is less reliable, as it depends on manual procedures and can quickly become untenable as data stores grow.
Other strategies include 3-2-1-1, which features three copies of data stored on two different types of media, with a minimum of one copy stored offsite. Another variation, the 4-3-2 strategy, focuses on having four copies of data stored in three different locations, with two locations being offsite.
How to get the third copy of data off-site
In the traditional approach to 3-2-1 backup, satisfying the requirement that one copy of data must go offsite was typically accomplished by sending a tape to another location. Usually, a company would contract with a tape vaulting service, which would pick up and store the tape cartridge. Data copied to non-tape portable media, such as optical disks or removable drives, would similarly be handled by an offsite vaulting service.
Today, some companies still rely on tape and outside vaulting services, such as Iron Mountain. Some companies that have their own remote facilities -- such as satellite offices, secondary data centers or disaster recovery installations -- can use ordinary courier services to pick up and deliver their offsite copies. Depending on the nature and location of the remote storage facility, some environmental issues (e.g., heating, ventilation and air conditioning) might need to be resolved to ensure that the tape media is stored safely.
Vaulting or other offsite scenarios come with their own caveats. Backup tapes can get lost between the loading dock, the delivery van or the offsite service. Natural elements -- heat, cold, rain or snow -- can wreak havoc with tape cartridges, causing data loss. For these reasons, offsite copies on any medium should be tested to ensure their integrity soon after they arrive at the remote facility.
Increasingly, however, companies avoid some of the pitfalls of manually handling copies of their data by transmitting their offsite copies electronically. Instead of physically shipping tapes, disks or drives, offsite copies can be sent over the internet or private communication lines to a cloud storage service. Often, the backup software or hardware will handle transmitting the offsite copy automatically, but compatibility between the backup system and cloud service can be an issue.
If the offsite copy also represents the second media type (the "2" of 3-2-1), sending it to a cloud service adds a wrinkle to the 3-2-1 backup method, as the service is likely to store the copy on the same type of media that is used in-house. Although this deserves some consideration, it might not be an issue. Cloud storage is often considered more of a storage medium than an alternative storage location.
Universality of the 3-2-1 backup rule
Data protection technologies and techniques have evolved considerably since the 3-2-1 backup methodology was first conceived in the early to mid-2000s, but it can still be applied to the various forms of modern data backup and recovery today.
Part of the reason why the 3-2-1 backup strategy still works is due to its universality. It is useful for any industry that needs to protect mission-critical data. It can be applied to different types of data, such as structured or unstructured, text, photos, or video, for example. It can also apply to different storage formats like hard drives or cloud storage.
Snapshotting and replication are two widely used data protection technologies that help overcome some of the obstacles of adequately backing up very large data stores. Using snapshots plus replication fits nicely within the 3-2-1 model as the methods used to make the original copy of the data as well as the two duplicates. But it's important to understand the target system requirements of storage vendors' snapshot and replication applications; already installed storage systems might not be appropriate targets for some vendors' products.
Backup appliances are relatively new fixtures in some data centers that combine backup software with dedicated hardware. These devices simplify initial backups and can usually connect seamlessly with a cloud backup service to stash an offsite copy of the data. In most cases, these systems can be used to hold one of the on-site copies, making it easy to recover individual files or entire data sets.
Similarly, data protection processes such as continuous data protection (CDP) alter the 3-2-1 model a bit, but with proper management these newer approaches can support 3-2-1 effectively. True CDP copies new and modified data to a target system immediately -- or in frequent batches -- so it can be a good upgrade to a 3-2-1 system that needs to back up voluminous data. Because CDP backups are far more frequent than daily or weekly backups, the risk of losing data is considerably reduced.
Do new uses of backup data make the 3-2-1 rule ineffective?
There are other developments in modern data protection that don't eliminate the possibility of using a 3-2-1 backup scheme, but they might make it a little more complicated to manage. Some of the more impactful developments related to 3-2-1 backup processes include:
Populating data warehouses and big data analyses
- Uses for backed-up data. Companies are extracting more value from their backup data stores by using that data for things like developing and testing new applications. Contemporary approaches to programming, such as DevOps, require easy access to data that is as close to live application data as possible to ensure that applications are developed properly in a real-world environment. Backup data fills that bill very nicely, as it's likely to be freshly generated on a regular and frequent basis.
- Backed-up data is reliable and accurate. Analytical applications might also need access to large amounts of current data. By using fresh backup data, the results of the analytic process are likely to be more reliable and accurate. Tighter controls and management of data companies are required to ensure these applications get the best data possible while maintaining the primary concepts of 3-2-1 backup. Note that if one of the backup copies is used for application development or for analytics, it can be altered or unavailable, making one of the requisite three copies unusable if recovery is required.
Personal information and data integrity
- Data integrity. Data integrity has always been a key concern of data protection activities. It is not enough to simply back up data and lock away the copies; it is imperative to ensure backups are complete, uncorrupted and recoverable. Recovery testing helps in this regard, as well as employing some of the more advanced features that backup apps offer to detect ransomware and other threats. Again, these concerns don't necessarily derail a 3-2-1 backup approach, but they might add some steps to the process, such as regularly scheduled recovery testing.
- Regulation. The General Data Protection Regulation (GDPR) is another contemporary wrinkle that could affect data protection practices. The GDPR is European Union legislation that defines the steps organizations must take to protect the personal data of their users. For 3-2-1 backup practitioners, this means ensuring that wherever those three copies of data are stored, security measures -- both physical and digital -- are adequate to ensure against data theft or loss as well as avoid potentially crippling EU fines and negative publicity.
- Responding to user requests. Another directive of the GDPR says that a company's customers or users have the right to have their names and all data related to them expunged from the company's storage systems and media. In a 3-2-1 environment, this means that the information must be removed from all three copies of the data, so it's necessary to be able to search stored data on a granular level to discover the specific pieces of data that must be deleted.
Operational resiliency
- Archive data. Active archive is another contemporary application that could potentially use backup data. Data that is stored permanently and never accessed can be kept in cold storage, but active archive data is saved data that can be accessed even if its useful life appears to have expired. If one of the backup copies is also designated as an active archive resource, the data should reside on accessible storage and users will likely need search and retrieve tools to tap into the archive.
Although the 3-2-1 backup strategy is old by technology standards, it still serves as a relevant start to approach data backup. Strategies like snapshotting and replication are still relevant and can be integrated into systems quickly, for example. In some scenarios, however, implementation of this strategy requires additional precautions. And the strategy still has its challenges.
What are the challenges of 3-2-1 backup?
As an effective data protection scheme, 3-2-1 backup has stood the test of time. But, in the context of contemporary storage systems and services, some of the steps and practices might need to be adjusted to meet data protection objectives.
Keeping track of 3-2-1 backup data copies can get complicated depending on the type of backup an organization is using in its 3-2-1 setup. For most companies, doing a full backup daily is not feasible. Therefore, other approaches are likely being used, such as incremental or differential backups or CDP and eschewing batch backups entirely. Because those types of backups can require some interim actions to produce a full backup copy, the three data copies rule of 3-2-1 might require some added management to ensure that all available copies are up-to-date and easily accessible.
One such consideration might be how many modern organizations accelerate data backup: deduplicating the source data. With this, the data that has already been backed up and hasn't changed isn't backed up again. This process is typically very granular, operating at a sub-file level. That means when deduped data is recovered, it must be reconstituted by reassembling the portions of files that were copied over the span of several deduped backup operations. The reconstitution process takes time, so recoveries of deduped data will take longer than recovering a full backup.
If a cloud storage service is being used to store the offsite copy, the service provider should be asked to provide details related to its data protection processes. Many cloud storage providers will charge customers extra to recover any data that the customer might have accidentally deleted. To avoid additional charges and to add a level of data safety, it's a good idea to copy the cloud-based backup to another cloud storage service, which effectively duplicates the 1 part of 3-2-1. Additional charges can also be incurred when recovering data from a cloud service, as some providers charge users a fee for retrieving data they have stored at the cloud service.
As noted earlier, using a cloud storage service or transmitting a backup copy to a remote facility requires telecommunications services with ample bandwidth to handle the volume of data that is being sent or retrieved. These costs can also escalate as the amount of data a company has grows. Even with fast communication lines, it takes time to retrieve data. That should be considered when developing recovery plans.
If tape or optical libraries are a part of the 3-2-1 backup scenario, it is necessary to maintain that equipment to ensure that data can be recovered in a timely manner. Generally, that should not be an issue, but if a company uses tape or optical gear that is older or even has reached end-of-life, maintaining that equipment appropriately can be difficult or costly. Alternatively, the data stored on the obsolete hardware can be recovered and rewritten to up-to-date hardware and media, but that's an expensive and time-consuming process. If tapes or other media are stored offsite at a vaulting service or another remote site, the time it takes to transport them back to a company facility where they can be loaded into a tape library must be considered when determining how long the recovery process is likely to take.
In a disaster recovery situation, more than just data is needed to recover systems and resume operations. Companies should consider disaster recovery as a service (DRaaS) as an enhancement to their 3-2-1 procedures for storing a backup copy offsite. DRaaS is enabled by server virtualization, which lets an organization back up its server OSes, environments and applications, along with the data that is typically protected during a backup. When an outage occurs, the virtual servers can be spun up, the applications restarted and the data accessed to allow business operations to resume.
Ransomware attacks might not be fully mitigated by a 3-2-1 backup strategy. A ransomware attack can encrypt data it has access to, including any locally stored backups or backups connected to the infected system.
How to successfully implement a 3-2-1 backup strategy
There are some basic managerial fundamentals for a successful 3-2-1 backup implementation:
- All data copies are identical and up to date.
- The media storing the copies is readable media.
- All copies and equipment are tested and confirmed to be in working order.
- Remote copies are stored safely.
- Recovery of single/multiple files or a full backup is tested on a regular basis.
- Internal data copies are on different storage systems and networks and are not accessible from outside the company.
The backup software used in the 3-2-1 process can be helpful as it can automatically direct the disposition of backup copies while cataloging all backup activities. Most backup apps have also added features to check for threats, such as malware, ransomware and viruses in backup copies.
If an organization uses a backup app to spin off the duplicate copies to a cloud backup or storage service, it should ensure that there aren't any compatibility issues with the backup application and the cloud service. To complete the 3-2-1 strategy, a backup of the data should still be stored locally, and another should be stored locally on a different storage medium. The cloud platform would then count as the offsite storage location.
With large volumes of data to protect, new applications that use backup data and the legal implications of maintaining the integrity of stored information, it's no surprise that many backup applications have gone beyond just making copies of data. Today, most backup apps provide built-in or optional data management and security features, such as ransomware protection; data indexing and searching; and extraction, load and transform services so that data can be used in multiple applications.
If a backup application does not provide all the information needed to effectively manage 3-2-1 backups, a backup reporting application such as Bocada or Veritas NetBackup IT Analytics can provide comprehensive backup management, including monitoring and managing cloud backup activities. These applications go well beyond just tracking backups and can be used for overall storage environment management, even with a mobile device such as an iOS or Android smartphone or tablet.
The 3-2-1 backup rule can be updated using modern storage methods, such as by using the cloud to store data offsite. Learn more about using the 3-2-1 strategy in a multi-cloud environment.





