
tashatuvango - Fotolia
How can I integrate cybersecurity and backup planning?
Your organization should integrate its cybersecurity and backup processes. It's easy for a cyberattack to affect backups, unfortunately, so be proactive about it.
Cybersecurity should be part of everything associated with business continuity and disaster recovery planning and related activities, including backup. Regrettably, there's still the tendency to keep cybersecurity as a separate activity or part of information security planning.
In reality, a cybersecurity event can seriously impact business operations, which, of course, then triggers BC/DR responses. Let's examine ways we can cost-effectively integrate cybersecurity and backup planning, a key component of BC/DR initiatives.
A cybersecurity breach can impact virtually any kind of information in electronic form. Often, an attack damages data in transit, although data at rest -- in storage -- could still be affected. Therefore, we must ensure that backups have been scanned for any anomalies before being stored.
An organization can protect data stored within its perimeter through the use of devices such as intrusion detection systems and intrusion prevention systems. It's also important to have suitably strong firewalls and various software to detect and mitigate viruses, phishing scams and other suspicious code.
Data entering through the company's perimeter, such as email, must also be carefully scanned for any cyberattack content using many of these same technologies.
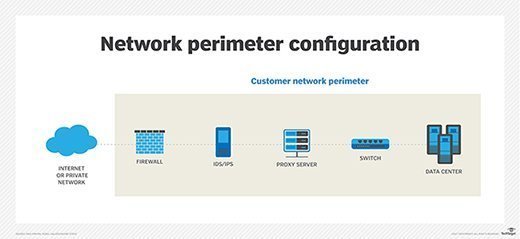
When backing up data, however, the likelihood of a cybersecurity attack increases when data is backed up off-site. Data backed up internally can still be compromised by code that attaches itself to the system performing the backups and the storage devices. You must, therefore, ensure data being backed up is protected from a cyberthreat at every stage of the backup process.
One mitigation strategy for cybersecurity and backup is to encrypt data at rest and in motion. That way, you increase the odds of the data being successfully backed up and retrieved when needed. Encryption is increasingly common in many applications today. For example, Microsoft Office 365 encrypts email and attached files. Office 365 also archives and stores email and other files in encrypted form.
In data backup planning today, it's foolish to ignore the impact of a cybersecurity breach. Work on the basis that all your backup efforts can be easily compromised by a cyberattack. Ensure encryption is a key component of your cybersecurity and backup strategies. Encryption technology continues to improve and is integrated in many applications, network devices and technology platforms.
When conducting data backup tests, be sure to verify you can retrieve and decrypt your encrypted files and other test resources with no damage to the payloads. Continually review and update your data backup software and storage technology to ensure it's optimized with regard to cybersecurity protection.







