Contact center fraud: How to detect and prevent it
Contact centers can be sitting ducks for fraudsters, but comprehensive agent training, authentication techniques and advanced technologies can protect businesses and customers.
Contact center fraud is a reality that organizations must prepare for or else risk considerable losses due to security lapses in customer data protection. Successful fraud schemes can damage a brand's reputation and result in compliance liability, especially in heavily regulated industries, such as financial services and healthcare.
Companies can mitigate their vulnerability to unauthorized access or disclosure of confidential information with the right blend of comprehensive agent training, well-documented authentication and data security processes, and contact center fraud detection technologies.
What is contact center fraud?
At many businesses, traditional call centers and customer service and support operations have evolved into contact centers to handle customer communications across multiple channels, including phone calls, live chats, email, social media, text messaging (SMS), mobile apps and video calls.
Cybercriminals target contact centers to gain access to sensitive customer information by exploiting agents and weak authentication processes. These bad actors can then use personally identifiable information (PII) and other account data -- Social Security numbers, financial institutions and credit card numbers -- to commit identity theft, set up fake accounts and participate in bank and credit card fraud.
Why do bad actors target contact centers?
Contact centers are popular targets for fraud because poorly trained agents are often vulnerable to manipulation. A toll-free number used for customer service and transactions such as purchases can allow criminals to initiate numerous fraud attempts while maintaining anonymity, provided they use caller ID spoofing techniques. Unsuspecting agents, especially in call centers, make excellent attack vectors since they're all that stand between a fraudster and customer accounts.
The transition to hybrid work environments after the COVID-19 pandemic has created challenges for contact center fraud detection preparedness. Remote work has made it increasingly difficult for agents to receive proper fraud detection training or guidance from co-workers. As a result, they may struggle with using anti-fraud tools remotely.
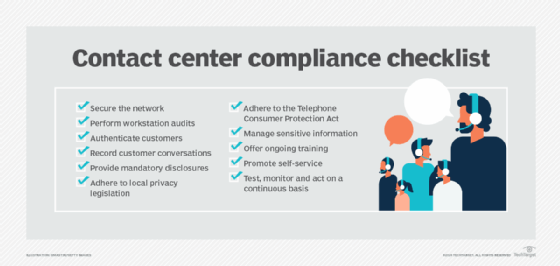
Common types of contact center fraud
While contact centers encounter many types of fraud, the most common are identity theft, account takeover, stolen credit card information, vishing scams and finagling free merchandise.
Identity theft. Criminals use stolen personal information of legitimate customers to access accounts for monetary gain. Contact center agents might struggle to detect identity theft because the bad actors have accurate customer information. Many fraud schemes use personal information found on the dark web after a data breach. Synthetic identity fraud occurs when criminals combine real PII, such as a mobile phone number and email address, with falsified data to create a manipulated or false identity. They then use the information to open accounts and initiate transactions.
Account takeover. To transfer a customer account to their account, fraudsters might change an email address or login information to reset customer portal passwords. These criminals can use automated tools to create username and password combinations in a technique known as credential stuffing to gain access to customer accounts.
Use of stolen credit card information. Fraudsters bombard contact centers with attempts to buy goods and services with stolen credit card information. Because contact centers don't require physical cards, criminals can more easily make purchases with stolen information, a tactic known as card-not-present fraud.
Attempt to receive free replacement items. Criminals act as legitimate customers who purchased goods, then claim to have problems and request replacements. Retailers are the most common victims of this type of fraud, especially those with loose warranty and replacement policies.
Phishing and vishing scams. Cybercriminals have long targeted consumers with phishing scams, sending fraudulent emails that contain malicious URLs or hyperlinks to download malware or steal passwords. Another tactic is voice phishing, or vishing, using urgent phone calls that demand victims to update company or personal data supposedly to protect bank accounts and other financial transactions. Similar fraudulent methods are used on contact center agents. A criminal vishing about problems with an account can dupe an unsuspecting agent into sharing sensitive customer data. Many contact centers have been hit with ransomware attacks, locking up communications systems until the problem is resolved or the ransom is paid. Distributed denial-of-service attacks have also been used to disrupt communications services.
Tips for identifying fraudulent customers
Criminals use different fraud methods depending on their motivation or the type of contact center they target. Common warning signs of fraud include the following:
- Social engineering methods to falsely extract information.
- Inability to verify recent transactions.
- Long pauses before answering questions.
- Communication to evoke an immediate reaction based on urgency, familiarity or authority.
- Attempts to establish a relationship or rapport with a specific contact center agent or manager.
- Inconsistency in customer history and documentation.
- Attempts to bypass regular customer service procedures.
- Red flags and suspicious activity identified by anti-fraud technologies.
- Attempts to bypass anti-fraud processes and technologies.
Tools to identify fraud
Enterprises that take contact center fraud detection and prevention seriously shouldn't rely solely on agent training. Contact center managers can integrate several technologies into most on-premises, cloud or distributed workforce contact centers to block or flag suspicious activities and enhance fraud detection.
Identity verification. Technologies like automatic number identification can verify a customer's identity based on their phone number ahead of automated or interactive voice response (IVR) interactions. Some of these fraud detection technologies track phone numbers based on information like possession (authenticating the mobile number and the device), reputation (risk score) and ownership. If additional verification is needed, layered authentication controls can help prevent fraud by sending one-time verification codes via text or email to a customer's device. In the future, individuals could have additional ways to prove their identity with mobile devices as more states offer digital driver's licenses and government IDs.
Contact source analytics. Emerging technologies can more accurately confirm a contact's true source as well as the type of device used. These attributes can tip off contact center agents about whether the caller is a real customer or a criminal in a known fraud location or using equipment common among fraudsters, such as caller ID spoofing and IVR probing tools.
Multilayered authentication. Multifactor authentication, AI and knowledge-based platforms can identify bad actors who impersonate legitimate customers. The technology platform inputs various data points and calculates a fraud risk score to inform the agent about next steps in the fraud prevention process. A one-time pin or passcode sent by text or email to an individual's device can add a dynamic layer of security before a login session or transaction. Based on risk assessments, businesses must find the right balance between frictionless customer experience and layered security measures.
Voice biometrics. Advanced audio biometrics can analyze a caller's voice, creating a new authentication layer for contact centers and customers. Voice biometric SaaS providers let remote agents access these authentication services regardless of where they work. These technologies will soon have to contend with AI-driven voice cloning and deepfake audio, which might require reevaluation of fraud protection and other security measures.
Suspicious behavior detection. AI and machine learning techniques combine with fraud detection analytics tools to detect suspicious behavior such as unusual calling patterns, IVR usage anomalies and other behavior-based indicators. The tool then decides whether the contact is legitimate. Behavioral analytics can also be used to monitor agent behavior for insider threats by flagging multiple account redirects or password resets.
Editor's note: This article was updated to reflect the latest developments in contact center fraud detection and prevention tools, techniques and practices.
Kathleen Richards is a freelance journalist and industry veteran. She's a former features editor for TechTarget's Information Security magazine.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.






